Here, I’m sharing my personal analysis and evaluation of certain enterprise security threat modeling cases. If you’re interested, you’re welcome to join the discussion on enterprise security modeling, First of all, we should first understand the three pillars of security: confidentiality, integrity, and availability.
From the confidentiality perspective, data must not be leaked, so data should generally be stored securely; if it is exposed on the internet, it will open up a range of attack surfaces. Integrity means ensuring content remains intact — as you can see in this article, it must have a beginning and an end. Controllability means ensuring resources can run stably; for example, when you visit a website, that site should be able to provide you with content.
| Security Attribute | Meaning | Risks | Mitigations |
|---|---|---|---|
| Confidentiality | Prevent disclosure | Data leakage, unauthorized access | Encryption, access control |
| Integrity | Prevent tampering | Data forgery, log tampering | Signatures, checksums, transactions |
| Availability | Ensure accessibility | DoS attacks, resource exhaustion | Rate limiting, redundancy / disaster recovery, WAF |
With the above foundation in place, we can begin planning how to carry out a security assessment. Generally, a security assessment can be divided into the following stages:
- Asset planning stage
- Threat modeling for assets
- Risk assessment of assets
- Determining the scope affected by the assets
- Designing a security handling plan for the assets
All of the above steps must ensure that the three security principles are implemented, Threat modeling can use the STRIDE model
| Threat Category (STRIDE) | Meaning | Typical Examples |
|---|---|---|
| S – Spoofing | Impersonating a user or system | Fake user login, forged IP address or digital certificate |
| T – Tampering | Modifying data or code | Altering database records, tampering with data in transit |
| R – Repudiation | Denying actions or operations | User denies a transaction, deletion of audit logs |
| I – Information Disclosure | Exposing sensitive information | Database leaks, logs revealing confidential data |
| D – Denial of Service (DoS) | Disrupting system availability | Overloading server with requests, resource exhaustion attacks |
| E – Elevation of Privilege | Gaining unauthorized access | Regular user exploits a vulnerability to gain admin rights |
enterprises can develop their own asset management system or use open source enterprise management systems, provided they are built on a secure foundation. with this groundwork in place, we can begin assessing the risk landscape of the assets,
$$
Risk = Threat \times Vulnerability \times Impact
$$
we can use another risk assessment model can be used here, namely the DREAD model
| DREAD Factor | Meaning | Description / Questions to Ask |
|---|---|---|
| D – Damage Potential | Potential damage | How severe would the impact be if the vulnerability is exploited? |
| R – Reproducibility | Likelihood of reproduction | How easily can the attack be repeated? |
| E – Exploitability | Ease of exploitation | How easy is it to exploit the vulnerability? |
| A – Affected Users | Scope of impact | How many users or systems would be affected? |
| D – Discoverability | Likelihood of discovery | How easy is it for an attacker to discover the vulnerability? |
I previously created a data security exercise in some CTF games, and the risk assessment method used was based on this theory. I’m sharing it here for everyone to take a look
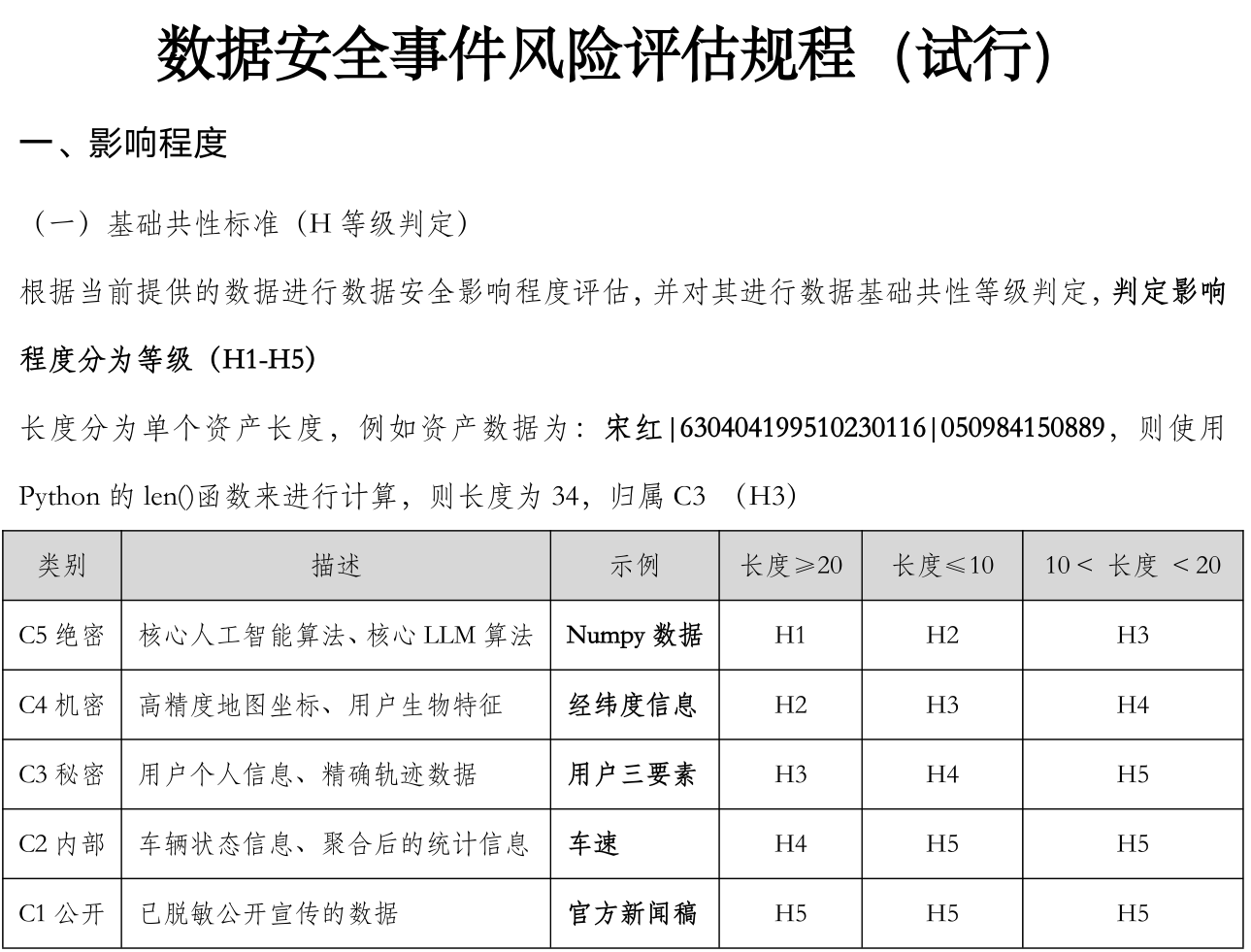
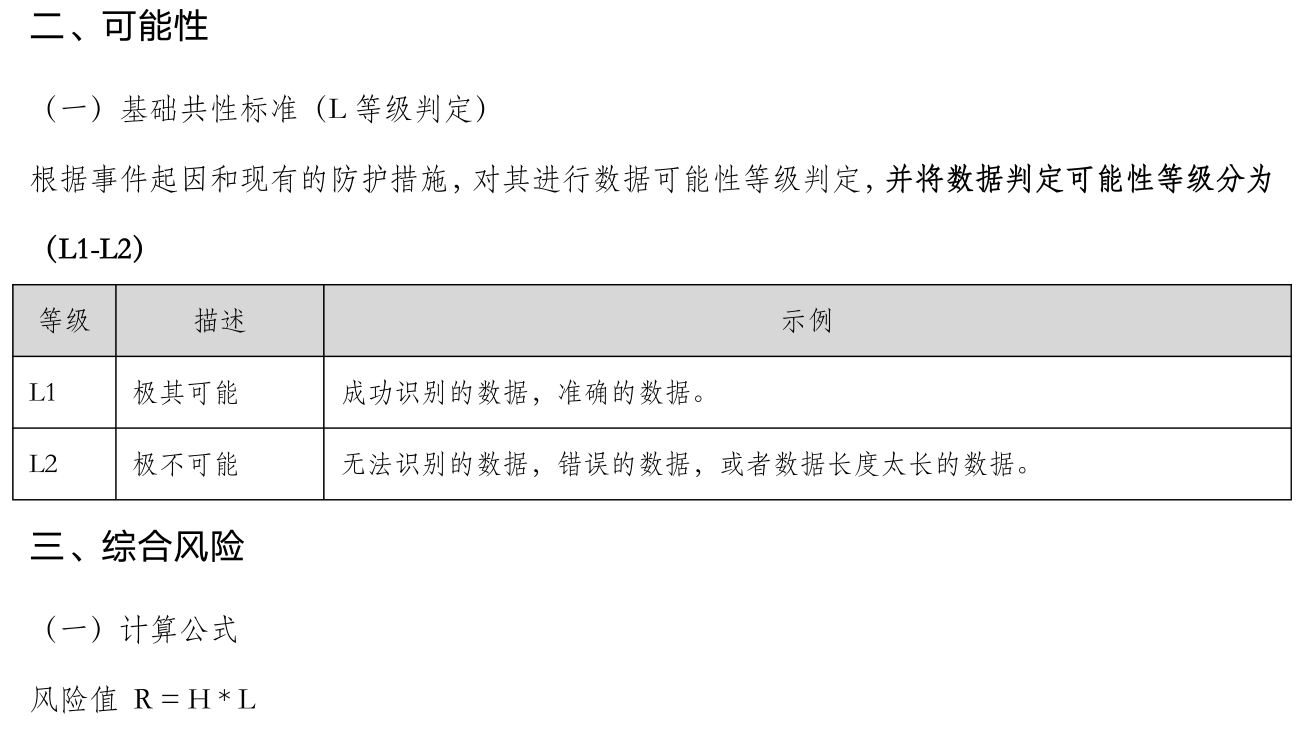
this exercise I created uses an assessment method that is applicable to data security, but it can also be applied to enterprise asset evaluation. In fact, the approaches are quite similar—as long as the assets are secured, the method works.
after determining the scope of assets and the impact of risks, we can begin designing security solutions for the affected assets. From a bug bounty hacker perspective, discovering a vulnerability is relatively easy, but fixing it can be quite challenging. When addressing a vulnerability, we must ensure that the service remains online while implementing the fix, avoid disrupting the user experience, and at the same time verify that the overall business remains secure, there are two possible solutions in this case, the first approach is to deploy upstream threat detection and defense systems, such as WAF, IDS, or IPS, while fixing the business logic, in order to block potential hacker intrusions, the second approach is to temporarily take certain business modules offline. For example, when you visit some websites, you might encounter a message like: “This service is currently unavailable due to security reasons. Please stay tuned.”
In the follow-up, we can use frameworks like the ATT&CK matrix to verify the effectiveness of vulnerability fixes and maintain the security of enterprise systems. I’ll be publishing more articles related to ATT&CK in the future. If you’re interested, feel free to subscribe to my RSS feed :)