I had always assumed that mimicry defense was about studying the dynamics of human interaction through machine learning. However, after reading online articles and studying the original competition questions, I discovered something quite different. The “Theory and Core Methods of Cyberspace Mimicry Defense” within the 863 Program proposes a dynamic, heterogeneous, redundant architecture that transforms the unknown into a known process, and then into an extremely low-probability event. This translates to “unknown+unknown+unknown=>uncertain threat.” This architecture eliminates the need for a single, static defense, but instead leverages dynamic changes to make it difficult for attackers to find exploitable, fixed vulnerabilities. The system continuously changes its operating environment, including the operating system, software version, network protocol, and even hardware architecture, making attacks more difficult. Each “unknown” represents a different dimension of uncertainty in the system. By introducing diversity and randomness, the unknown risk is gradually controlled within a certain range, ultimately minimizing the probability of a successful attack. This offers significant advantages in both offense and defense, ensuring a certain probability of preventing infiltration.
There is a very strong logic that is, if we introduce multiple backends into the system, and each request is randomly assigned to a different backend, then the attacker cannot be sure whether the response to each request comes from the same server or execution environment. I have built a similar shooting range in the process of playing school before. If you are interested, I will write an article to reproduce the situation when I have time. The specific explanation is that the attacker needs to access the API in a specific order to obtain the desired data, but because the backend is dynamically changing and the order of requests will be recorded, the attacker must ensure that each step is sent to the correct backend, otherwise he will not be able to proceed to the next step. Although it is a bit stupid, the phenomenon in practice shows that if there are multiple heterogeneous backends, each request will be randomly assigned to one of them, and the response to some requests will not be correct. The attacker must make repeated attempts to ensure that it is sent to the correct backend.
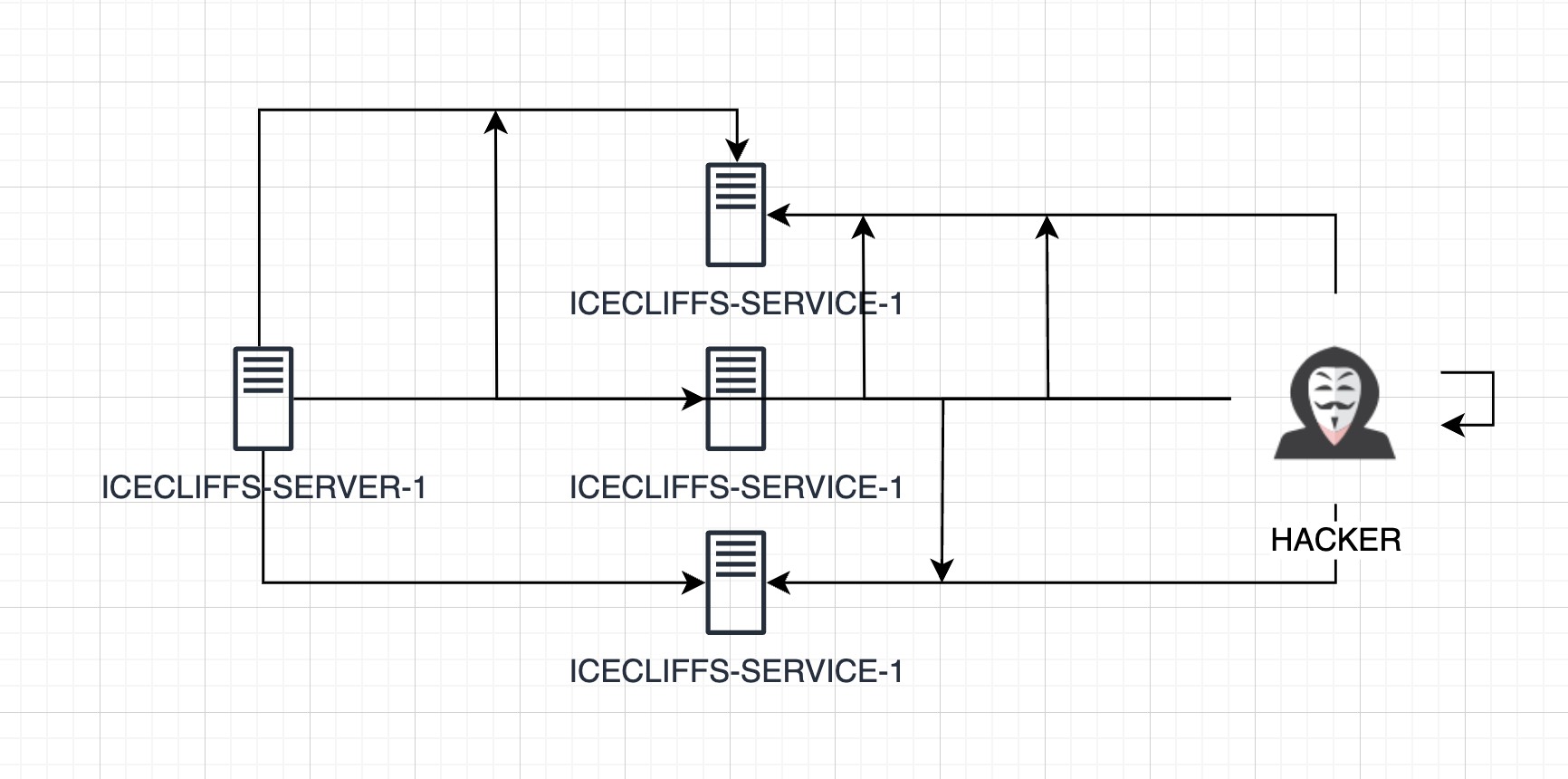
During the attack, the attacker not only exposes his own behavior but also gradually reveals the target he wants to attack. In addition, during the attack, the different responses of multiple backends will cause the system to automatically detect inconsistent behavior and issue an alarm. Changting’s Leichi community waf has a similar function. This mechanism not only makes the attacker’s behavior more transparent, but also locks the threat into an extremely low probability range by gradually narrowing the attacker’s window of success.
Here is a simple Nginx configuration file for your reference
1 | http { |
It’s even better when used with the Leichi WAF (probably, perhaps? Possibly? Using the jumping inequality, $main=6$).
Similarly, we can imagine a scenario where map software like Amap, Baidu Maps, and Tencent Maps are all vulnerable to hacking. If these mapping software were compromised within a short period of time, multiple incorrect navigation routes could cause traffic paralysis, a level of damage no less severe than a pager explosion.
Reference
- 拟态安全主动防御技术简介 - https://www.zjsee.org/detailr/id-783.html