XMUTCTF 2021 Writeup 0x2
Binary
净土截断
连接nc输入BV号取得shell,cat /flag即可
呼叫10086
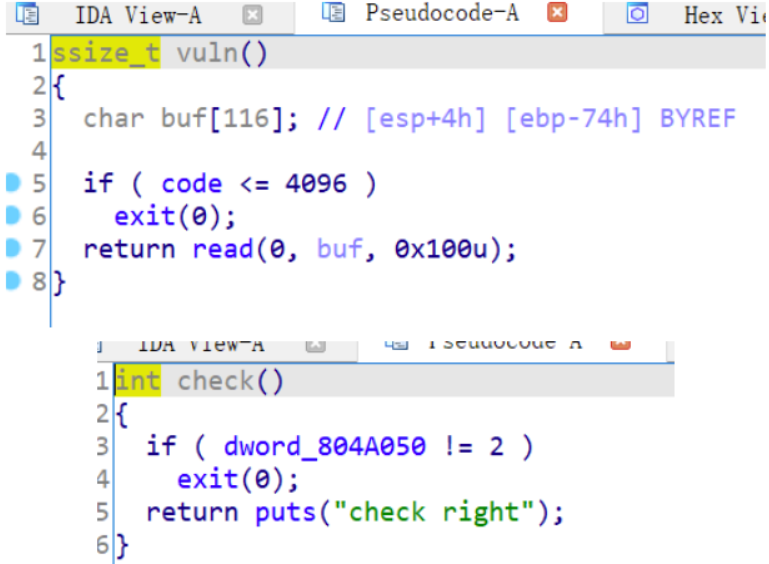
IDA打开程序,发现有个判断条件,只要把v5等于10086,就会执行 system('/bin/bsh')
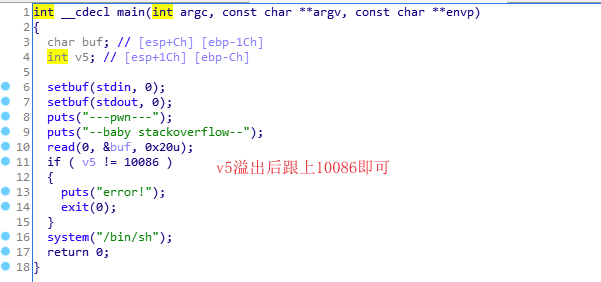
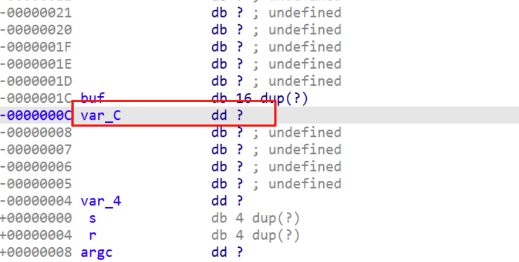
双击v5,发现它在buf变量内存下面,所以只需将buf溢出到 var_c 覆盖为10086
exp如下
1 | from pwn import * |
你会复制吗?
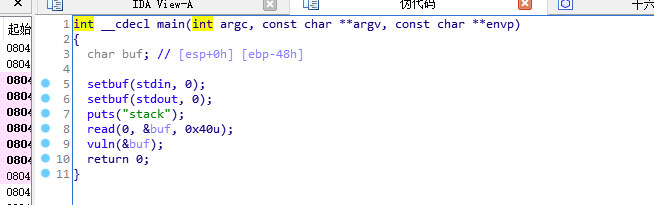
栈溢出题,buf为40,填到44后跟上/bin/sh的地址即可
exp如下
1 | from pwn import * |
0x6873
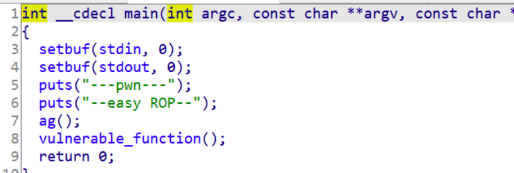
拖到IDA反编译,程序先调用ag()函数,然后调用vulnerable_function()函数
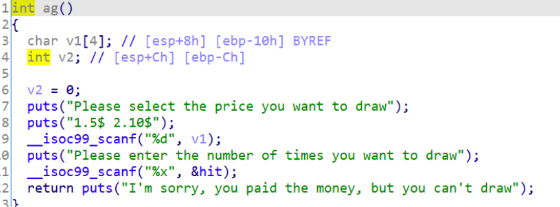
分析ag()函数和vulnerable_function()函数,发现有个read()溢出
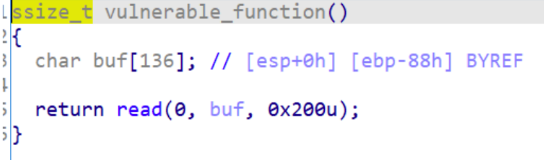
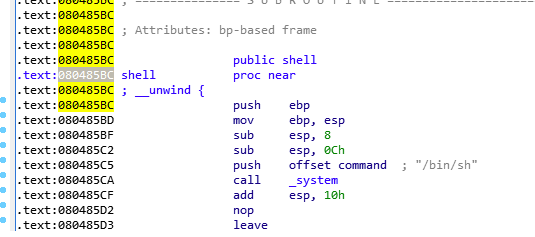
然后构造ROP,找到system和sh的地址
exp
1 | from pwn import * |
check
通过IDA观察,需要我们输入内容,然后用strncmp对buf和s进行比较,不相等就退出
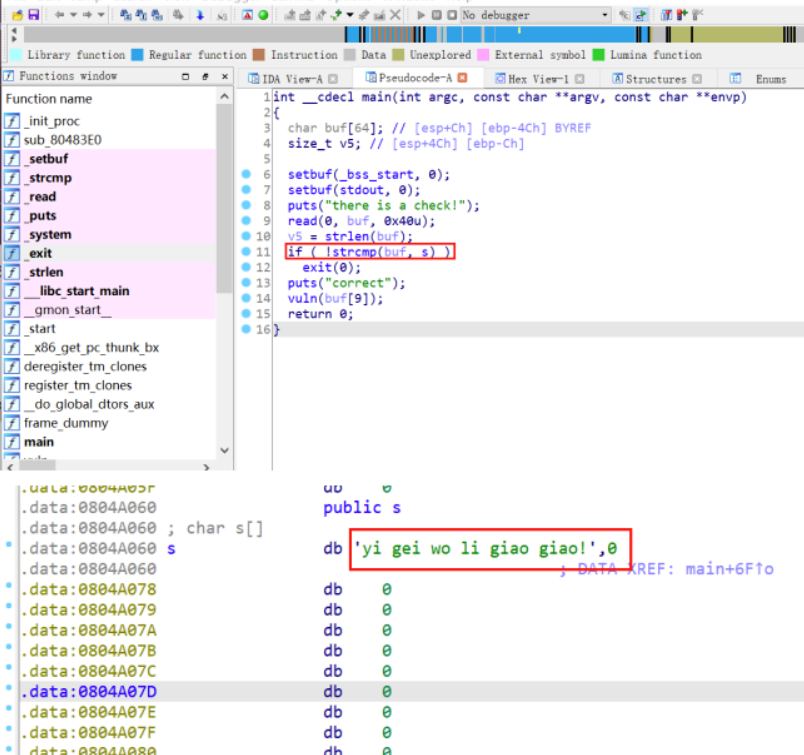
strncmp特性遇到\x00就停止,所以只需输入yi后面内容任意,然后程序将buf[9]传给vuln函数执行,判 断是否等于70,也就是字符’F’,最后利用read读取内容,这里read存在栈溢出
写Python脚本运行得到flag
1 | from pwn import * |
可爱的金丝雀
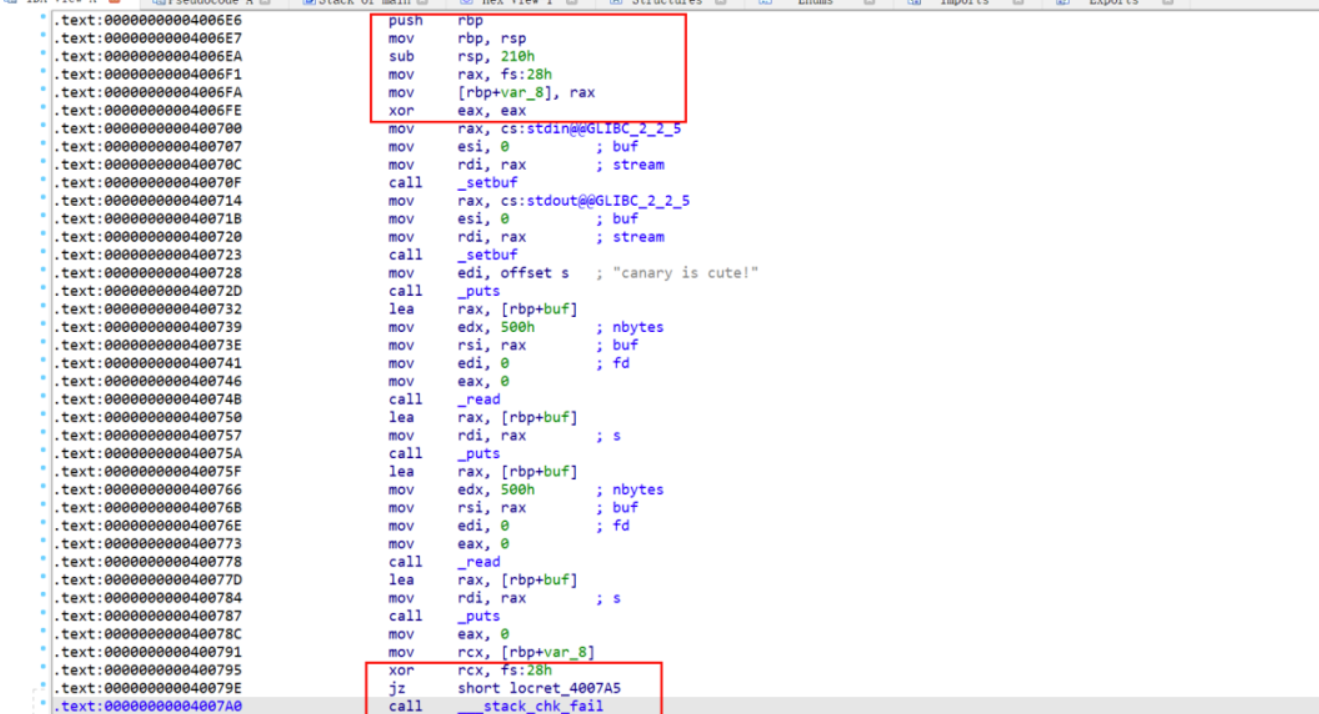
本题考的是canary保护,通过IDA也看到在main函数结束时,会取出canary的值进行比较不对就调用退出函数

分析程序,发现有两个read(),我们可以通过第一个read获取canary值,然后第二个read()写入canary 值利用溢出调用shell函数
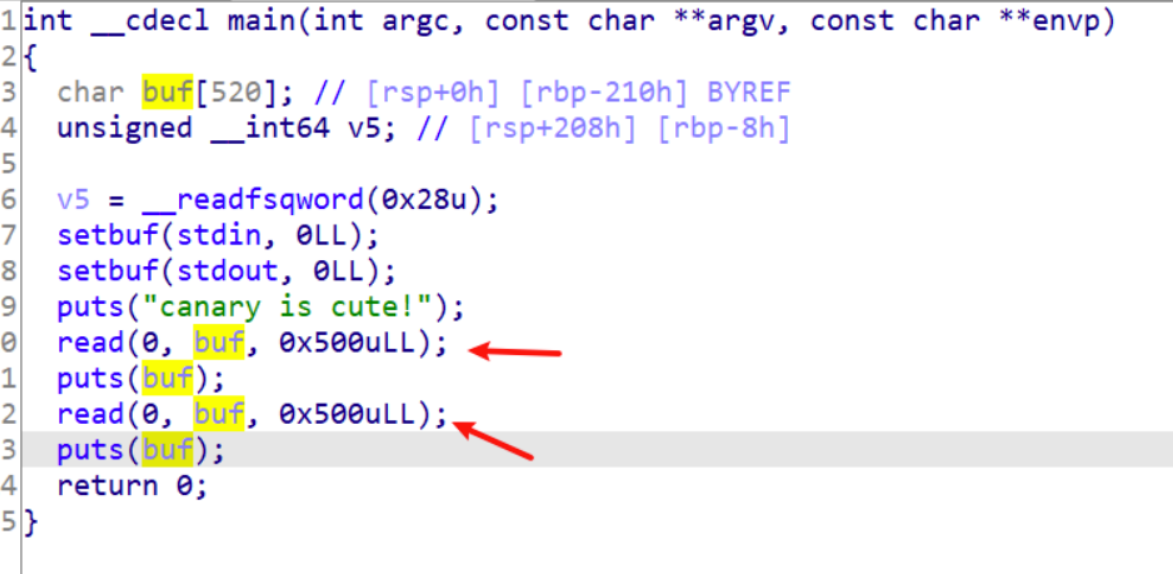
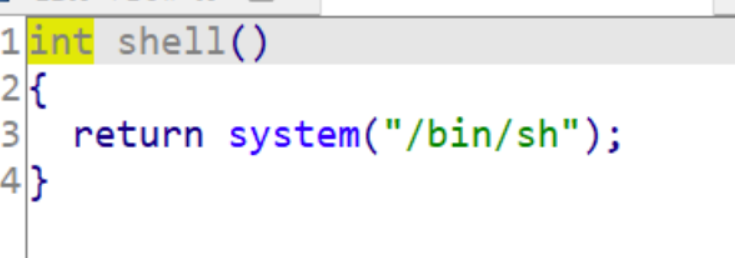
exp
1 | from pwn import * |
Fsb
IDA分析代码可知,程序会随机生成一个数赋给num,然后让我输入v5的值和num比较,相等就执行 system("/bin/sh")
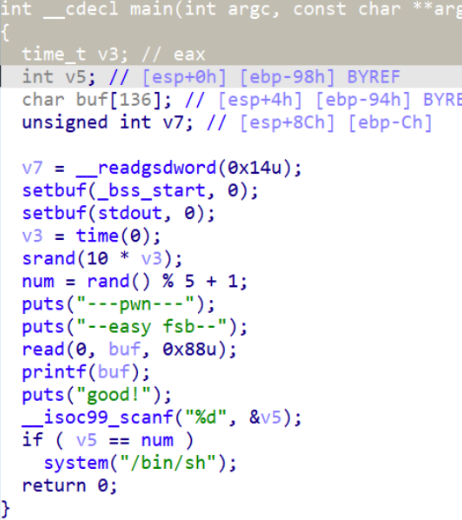
观察有read()读取内容到buf,用printf打印出来,可以利用字符串格式化漏洞修改num的值,后面v5输入我们修改的值即可调用system
1 | from pwn import * |
又小又大的pwn
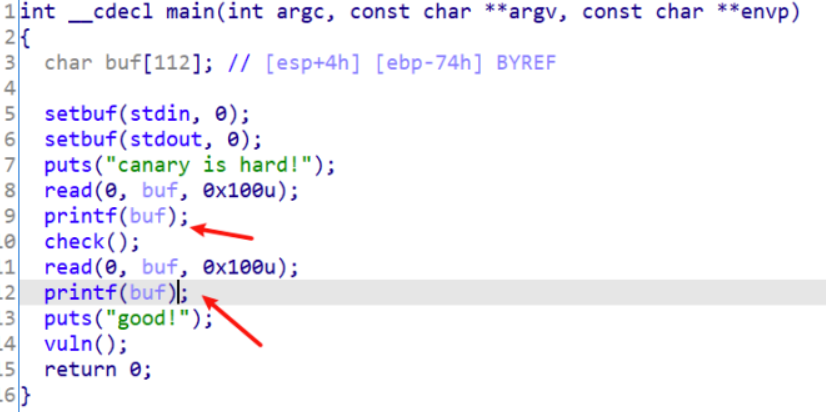
通过分析程序可知,有两处检查,一个是check判断code[1]==2和code[0]==4096
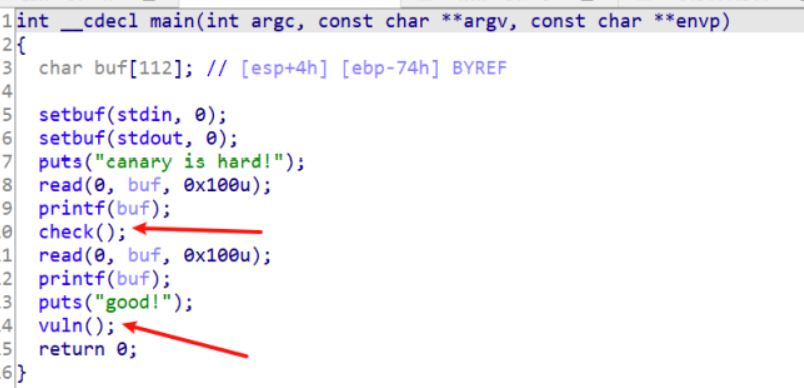
程序调用了两次read和printf,说明可以利用两次格式化字符串漏洞,
思路是第一次修改code[1],第二次修改code[0],最后利用vuln的栈溢出实现调用system,由于没有找 到’sh’或’/bin/bash’之类的字符串,所以在第二次修改code[0]的值时,可以将其修改成0x6873,写入时从 低到高写入hs,读取时高到低读取sh
1 | 0x68 |
1 | from pwn import * |
Web
easy_sql

用户名:admin,密码:随便输
easy_sql_2
登录:admin/admin,来到一个search页面,输入admin回显值
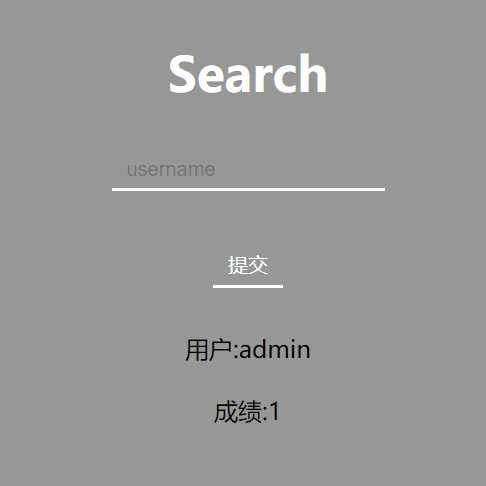
注入点:http://49.233.105.150:5004/search.php?name=admin' and 1=2--+
查列(三列):http://49.233.105.150:5004/search.php?name=admin' and 1=1 order by 1,2,3--+
最后上sqlmap,跑出来flag
easy_exec
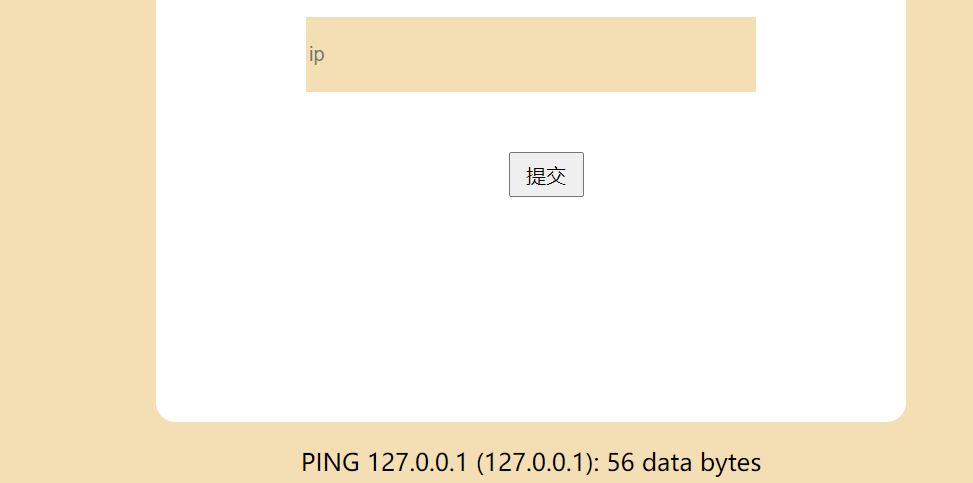
简单rce,发现输入flag会回显
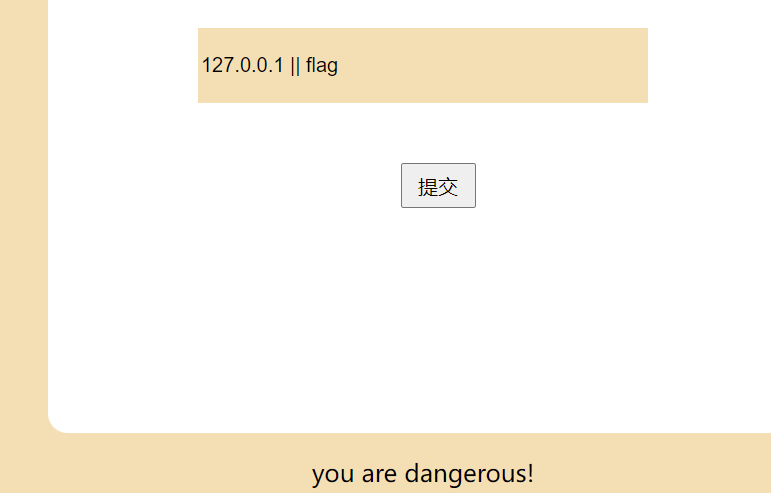
但这并不影响我们继续操作,ls跟目录发现有个flag文件
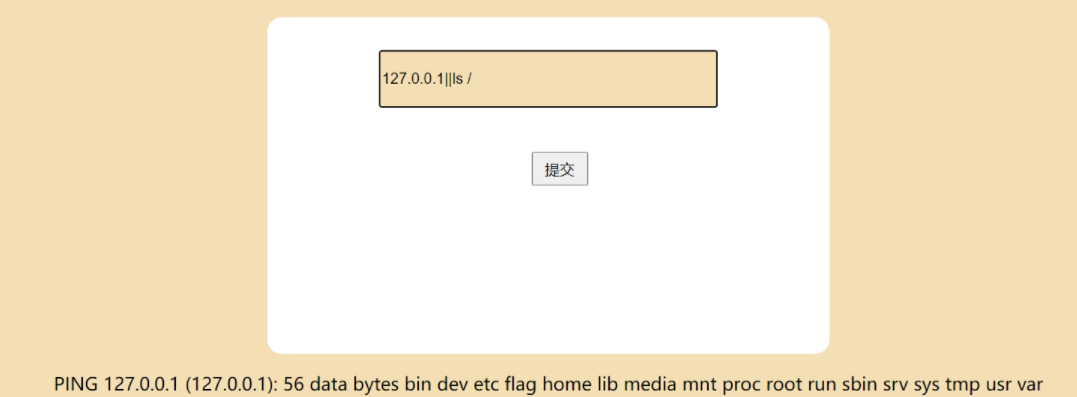
查看后发现是个假的flag
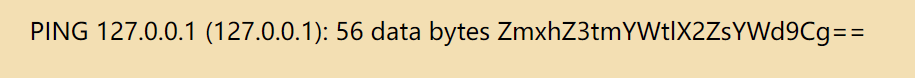
1 | flag{fake_flag} |
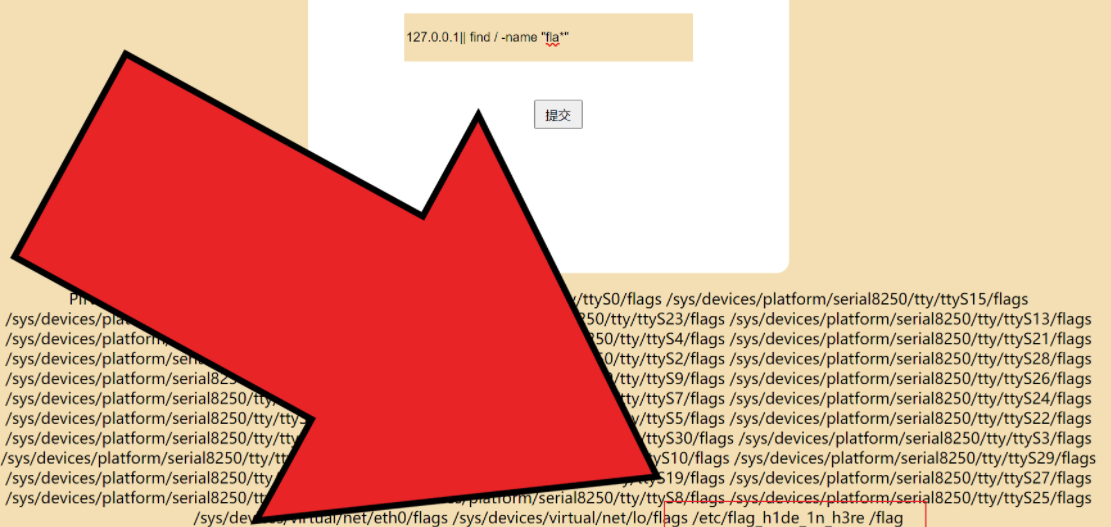
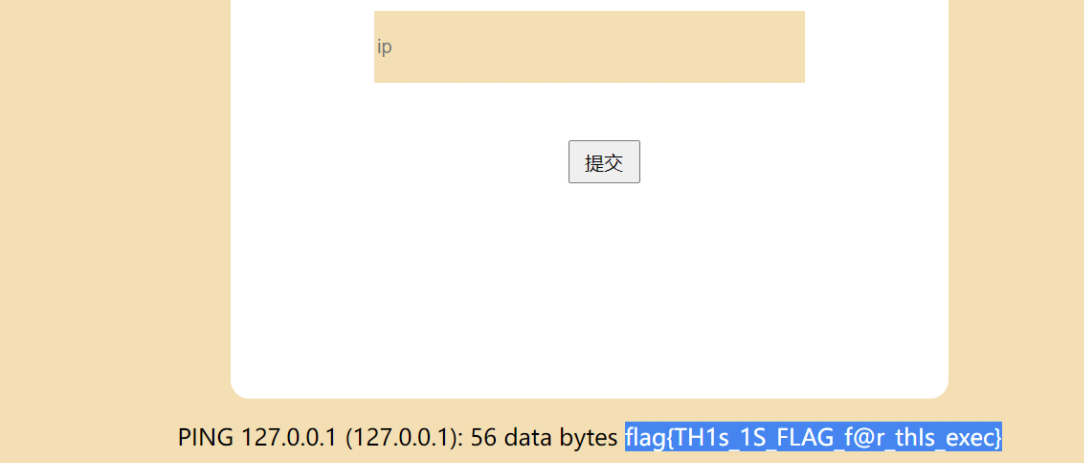
老样子搜一下flag,最后解出来得
easy_HTTP
查看robots.txt,发现hide.php文件,直接构造HTTP头
1 | User-Agent:me7eorite browser |
flag{c71b47-723409ac75-d3e6b28f-78b372ce}
easy PHP
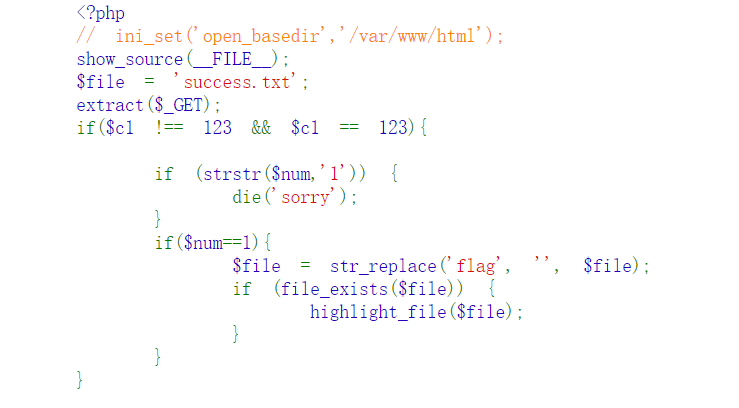
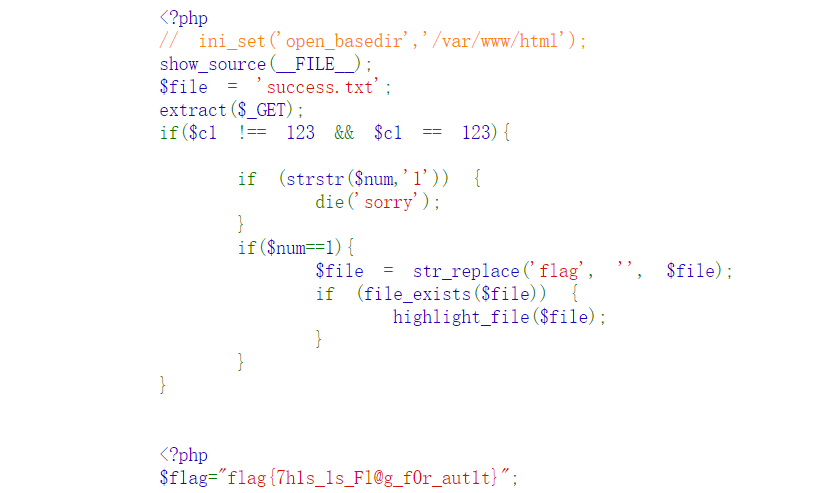
审计题,当c1=123的时候,弹到num,此时num如果为1则回回显sorry,但是如果num近似于1,即0.999999999999999999999999999,则会产生浮点漏洞,此时strstr被绕过了,然后num自然而然为1,最后发现file参数如果为flag会替换成一个空值,此时双写flag即可
1 | http://49.233.105.150:5007/?c1=123&num=0.9999999999999999999999999999&file=flflagag.php |
Reverse
lucky
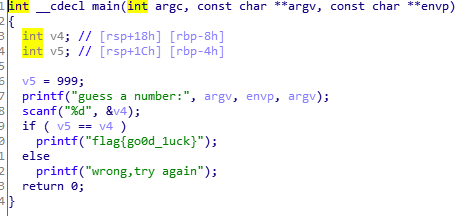
如果v4为999,输出flag
idaPro
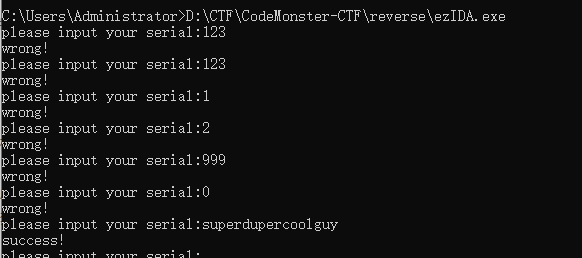
运行程序,要我们输入值
PEiD打开,发现有壳
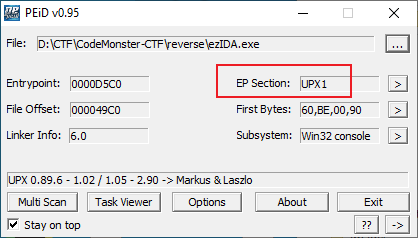
脱一下UPX的壳,然后拉入IDA
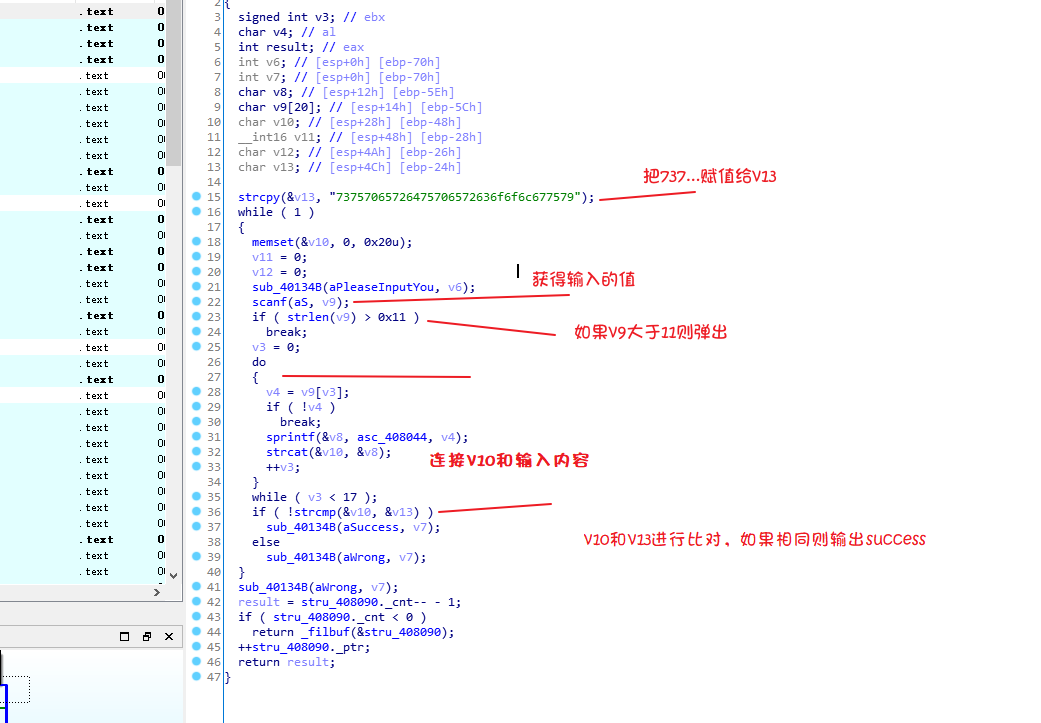
最后把73757065726475706572636f6f6c677579的值转成字符串
superdupercoolguy
发现上面这串就是flag (o_ _)ノ
flag{superdupercoolguy}
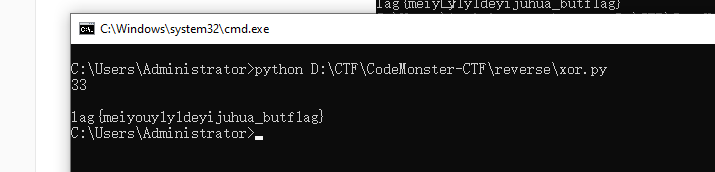
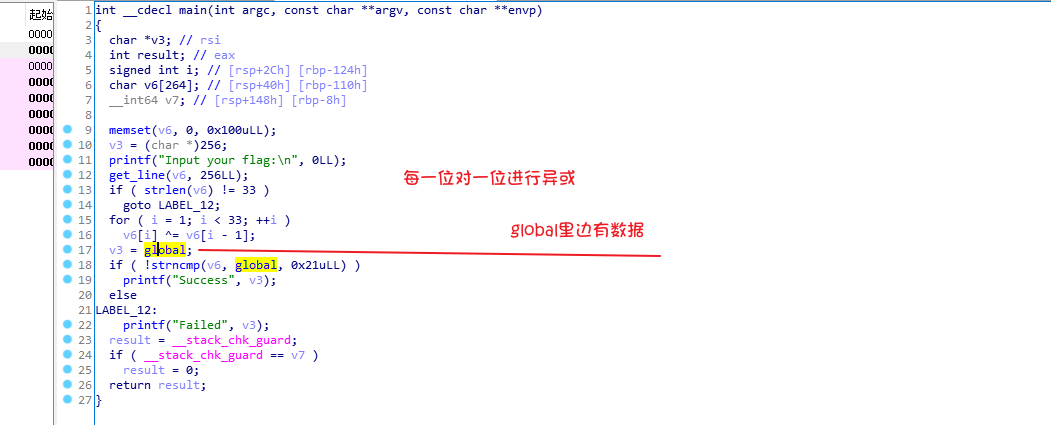
xor
一题简单的异或
GLOBAL
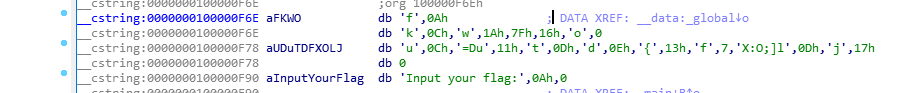
手动转成十进制…
1 | str1 = ['f',0xA,'k',0xC,'w',0x1A,0x7F,0x16,'o',0,'u',0xC,'=Du',0x11,'t',0xD,'d',0xE,'{',0x13,'f',7,'X:O;]l',0xD,'j',0x17] |
刚开始转成字符串的时候
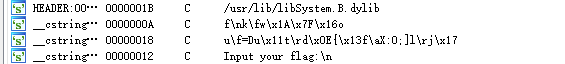
1 | #__cstring:0000000100000F6E 0000000A C f\nk\fw\x1A\x7F\x16o |
没注意到有个0截断字符串,题目死活做不对
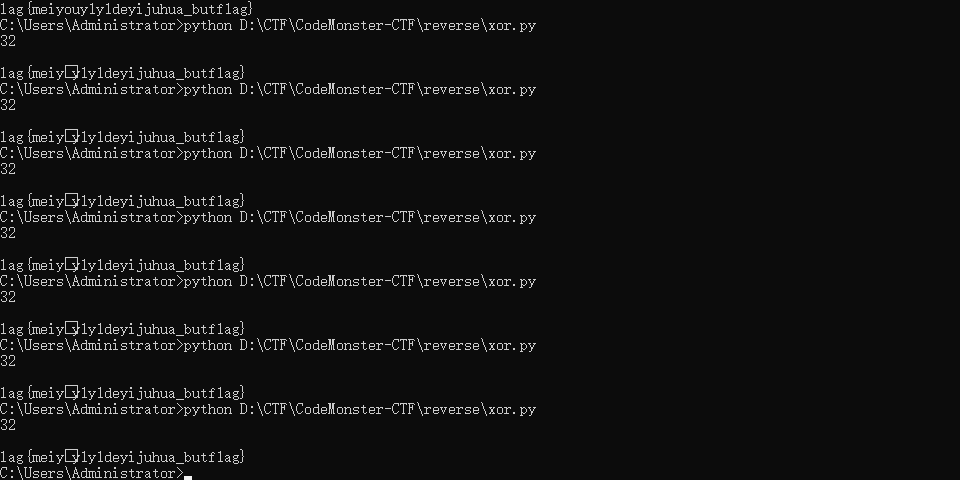
最后手动转的时候,把0给补上了flag才正确(o_ _)
exp
1 | #HEADER:00000001000004B4 0000000E C /usr/lib/dyld |
红宝石
这题。。。。要求求Time.now,自己看了下,考的Ruby。。本地没环境,好在语法简单能看懂,源码如下require ‘openssl’
1 |
|
Login
题目给出了 login.dex,那我们直接把dex转成jar,得到dex2jar.jar,然后拖到jd-gui进行分析
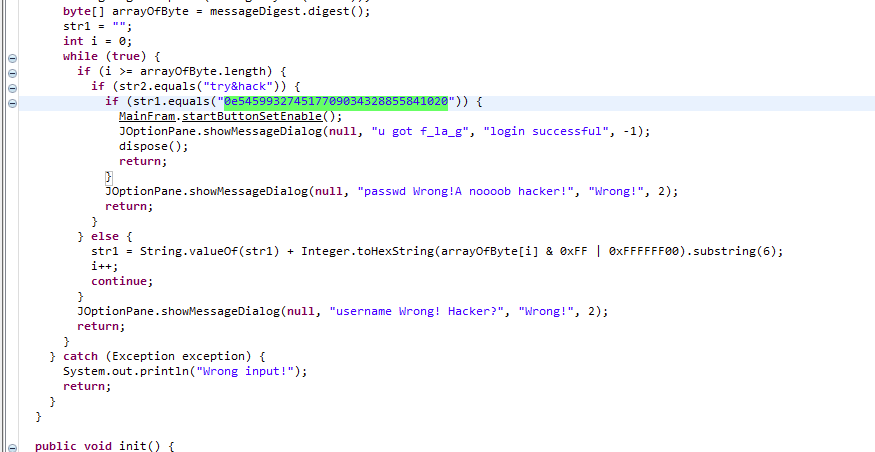
第一眼就瞄到了一串md5,直接解密得到 s878926199a(flag)
Maze
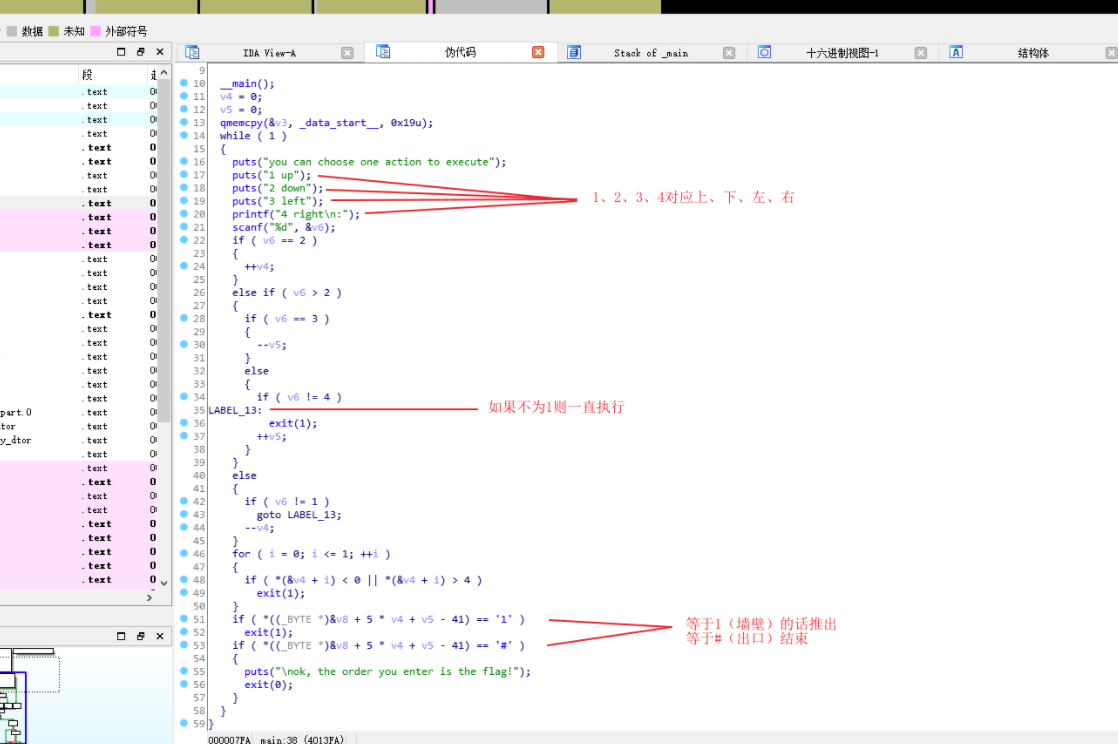
原题
1 | * 0 1 1 1 |
走迷宫就行
XMUTCTF 2021 Writeup 0x2