For learning and communication purposes only! Any illegal use of this technology is strictly prohibited! Violators will be held responsible for the consequences!
The setup tutorial is omitted (you can find a lot of them online). This is a long post, and I will slowly fill it in later. Since I’m not a communications major, please forgive any shortcomings.
This technology has been around for a long time. I remember back then, you could even use OpenBTS to send SMS messages.
My primary purpose for writing this was to see if I could still sniff SMS messages, and secondly, to refresh my knowledge of GSM networks. Refreshing the past can help you learn new things. Don’t criticize me if I don’t agree, and please point out any errors.
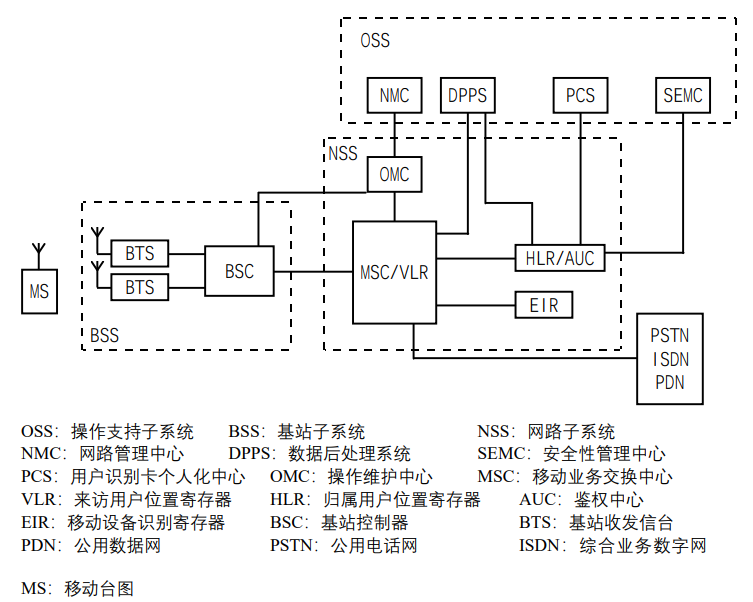
What about GSM
GSM, or Global System for Mobile Communications, is a cellular network with each cell having its own coverage area.
The basic GSM system consists of the OSS (Operations and Maintenance Subsystem), BSS (Base Station Subsystem), and NSS (Network Subsystem). Each subsystem also has different services, such as ISDN, PDN, PSTN, DPPS, and so on. It would be tedious to describe each one individually, so I’ll just give a brief explanation here. If you’d like a more in-depth explanation, please ask for the PDF document and study it yourself.
Related Information:
- SIM (Subscriber Identity Module)
This is a card with the ISO standard, the one inside your phone. It contains all user-related and radio interface information. A SIM card is required to use a mobile station. Emergency calls can be made without a SIM.
- BTS (Base Transceiver Station) and BSC (Base Station Controller)
The BTS is the radio portion of the BSS (Base Station Subsystem) and is controlled by the BSC (Base Station Controller). It typically serves the transceiver equipment in a cell and handles the switching between the BSC and radio channels.
- MSC (Mobile Switching Center)
The MSC is a node that controls multiple BSCs. It is the core equipment in the GSM system and has multiple functions.
- HLR (Home Location Register) and VLR (Very User Location Register)
The VLR serves mobile users within its control area. It stores information about registered mobile users within the control area and provides the necessary conditions for connected users to make calls.
The HLR is the central database for GSM, storing data related to all mobile users controlled by the HLR. An HLR can control several mobile switching areas. Important static data for all mobile users is stored in the HLR, including mobile subscriber identification numbers, access capabilities, subscriber categories, and supplementary services.
- EIR (Equipment Identity Register)
The EIR stores the IMEI of mobile devices. By checking against three tables—a white list, a black list, or a gray list—the EIR lists the IMEIs that are permitted, those that require monitoring due to malfunction, and those that are prohibited from use if stolen.
- AuC (Authentication Center)
AUC is primarily responsible for security measures, ensuring the confidentiality of voice data and signal information over the wireless network.
For information on the GSM security algorithm (A5…, please Google it; this article will not elaborate on it.
那么说回来,不法分子是如何知道我们的短信信息呢?这个很简单,我们的手机都处在一个大的基站辐射范围内(3G/4G)这就好比基站是谷仓,而手机是一粒粒的米粒,米粒通过电饭锅煮熟,基站负责(收发)每一粒米粒喷发出来的香味(信号)而不法分子使用降频工具手机会降级到 2G 进行通信,这个时候 GSM 嗅探工具就可以嗅探到我们的 SMS 信息了。

Pre
Hardware:
- Moto C118 (A few bucks)
- USB to TTL 2.5mm cable (the price of a bottle of drink)
- CP2102 module (the price of a bottle of drink)
Software:
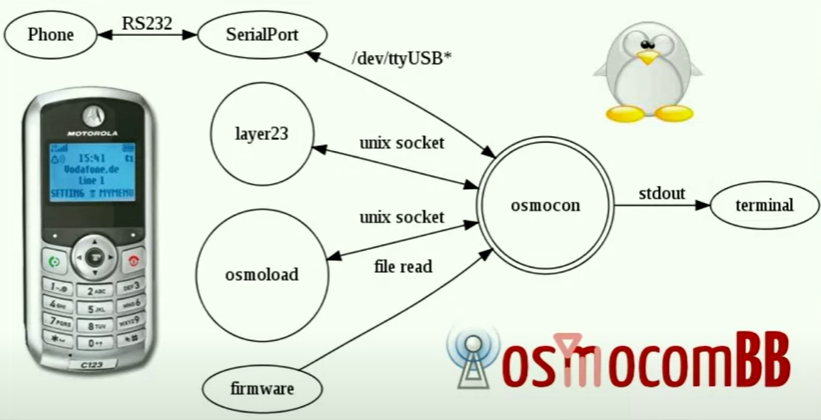
- osmocom-bb(https://osmocom.org/projects/baseband)
Regarding the osmocom-bb project, this is an open source GSM protocol project, which aims to achieve three-layer implementation from physical layer 1 to layer 3 on the mobile phone side.
- OpenBTS-5
- GNU

Build
First, update the system environment (the system here is Kali), change the source and update it yourself, then install the corresponding dependencies to prevent errors when compiling GNU later.
1 | apt-get install build-essential libgmp3-dev \ |
After the installation is complete, find a directory and create a new folder, then download the shell script to be used for compilation
1 | http://bb.osmocom.org/trac/raw-attachment/wiki/GnuArmToolchain/gnu-arm-build.3.sh |
The official website seems to be down. I put the shell script on my Github. You can fork it if you need it.
https://github.com/icecliffs/backup/tree/main/gnu-environment-shell
Create several folders install src build
Go to src and download the following files into it
1 | wget http://ftp.gnu.org/gnu/gcc/gcc-4.8.2/gcc-4.8.2.tar.bz2 |
Next, go back to the parent directory and give execution permissions to gnu-arm-build.3.sh, then ./gnu-arm-build.3.sh
1 | $ cd .. |
Press Enter to start compiling the environment. After a while, the following code will pop up, indicating that the build is successful!
1 | Build complete! Add <YOURPATH>/bin to your PATH to make arm-none-eabi-gcc and friends |
At this point, we also need to add environment variables. Open ~/.bashrc and add the following to the end:
1 | export PATH=$PATH:<YOURPATH>/install/bin |
The above is the process of building GNU. Next, we will set up the osmocom-bb environment and clone the repository to a local directory.
1 | git clone git://git.osmocom.org/osmocom-bb.git |
Before building, we also need to install the osmocom-bb libosmocore library. First, install the relevant dependencies.
1 | apt-get install build-essential libtool shtool autoconf automake git-core pkg-config make g |
Next, switch to the osmocom-bb/src directory and run the make command.
The installation steps above are very concise. Since I’ve already installed it, most of the steps are written from memory. For a more detailed version, please Google it.
If you encounter the error shown below during compilation, it’s most likely due to insufficient permissions or **uninstalled relevant libraries. You can install the package based on the **error**.
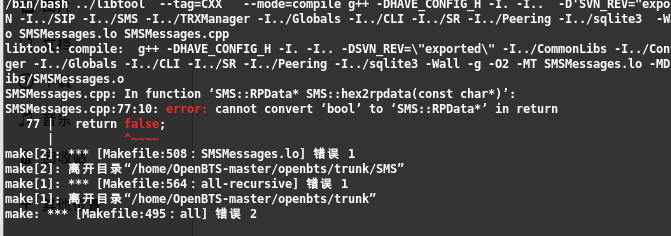
It’s also possible that the following package is missing; install it. (For reference only)
Attack
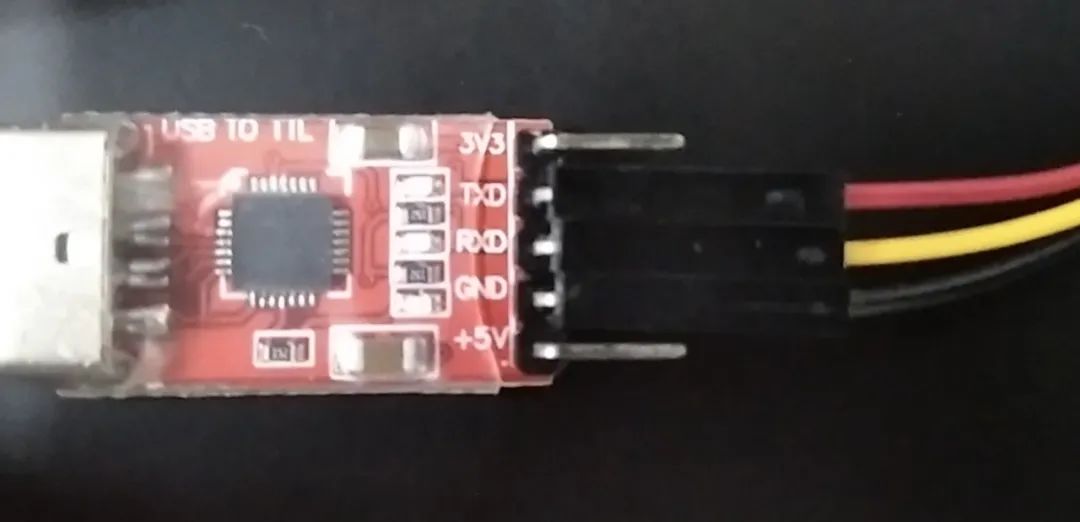
Connect your phone to a 2.5mm Dupont cable and flash the firmware. Note the connection order
Red -> TXD; White -> RXD; Black -> GND
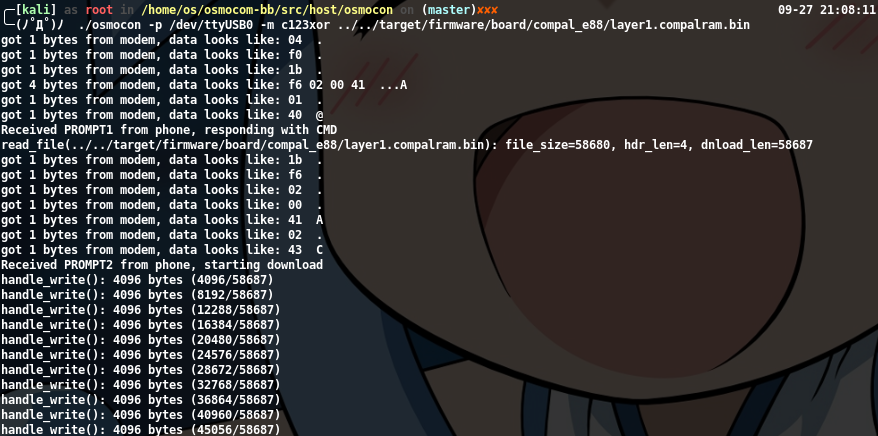
Go to osmocom-bb/src/host/ and enter the following command. Turn off your phone. After executing the command, press the power button to begin flashing the firmware.
1 | ./osmocon -p /dev/ttyUSB0 -m [firmware type] \ |
After flashing, Layer 23 will appear on the phone screen (I removed the screen, otherwise I could still show it to you, lol)
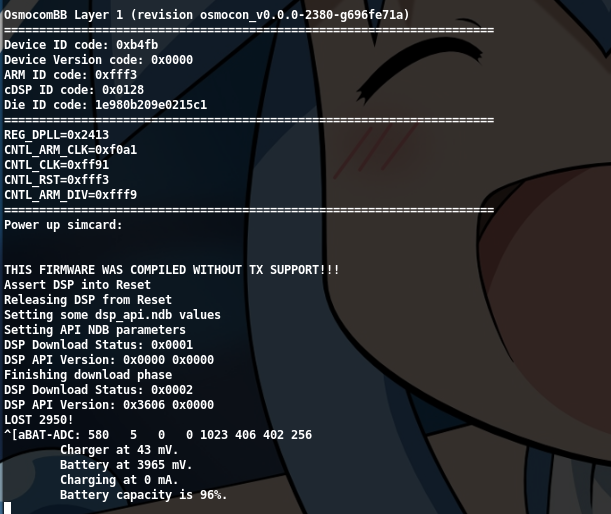
Press the button on the phone to display the relevant information.[/label]
Next, scan for nearby base stations.
1 | ./cell_log -O |
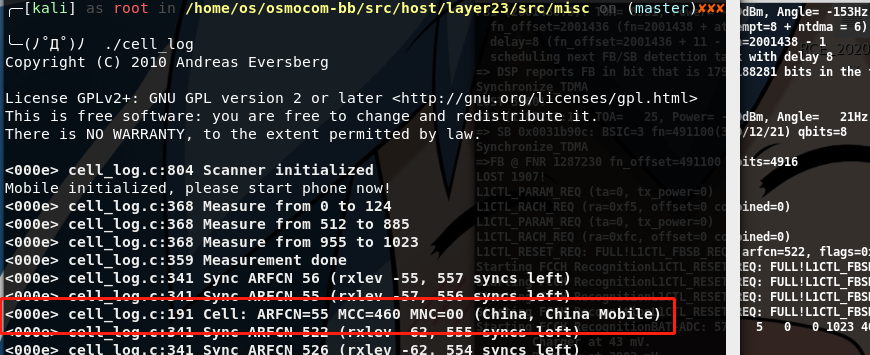
PS: Our 2G service is basically gone. I will write a new article based on the original one after I learn OpenBTS signaling technology. If there is a 2G signal, the signal (PWR) will be displayed like this
1 | <000e> cell_log.c:248 Cell: ARFCN=58 PWR=-23dB MCC=460 MNC=01 (China, China Unicom) |
Among them, PWR is the signal strength. The smaller the value, the better the signal. ARFCN is the base station channel number.
1 | ./ccch_scan -i 127.0.0.1 -a [ARFCN] |
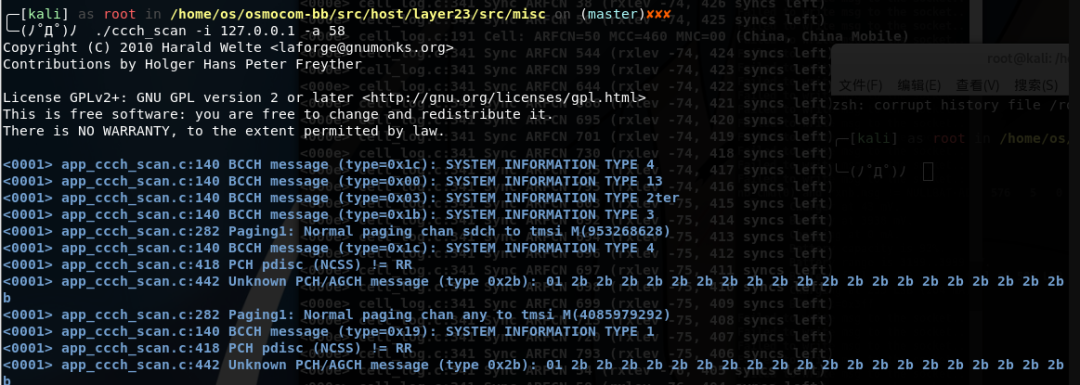
If the code continues to scroll after execution, it indicates that base station data is being sniffed normally.
For information on GSM frequency bands, refer to the chart below.
| Frequency Band | Name | Channel Number | Uplink (MHz) | Downlink (MHz) | Other |
|---|---|---|---|---|---|
| GSM 850 | GSM 850 | 128 - 251 | 824.0 - 849.0 | 869.0 - 894.0 | United States, South American countries, and parts of Asia. |
| GSM 900 | P-GSM 900 | 1-124 | 890.0 - 915.0 | 935.0 - 960.0 | This is the first frequency band implemented by GSM and is also the most widely used. |
| E-GSM 900 | 975 - 1023 | 880.0 - 890.0 | 925.0 - 935.0 | 900 MHz extended band | |
| R-GSM 900 | n/a | 876.0 - 880.0 | 921.0 - 925.0 | Railway GSM (GSM-R), a special version developed for railway dispatching communication systems. | |
| GSM1800 | GSM 1800 | 512 - 885 | 1710.0 - 1785.0 | 1805.0 - 1880.0 | Suitable for markets with high channel capacity requirements, second only to 900 MHz in application scope. |
| GSM1900 | GSM 1900 | 512 - 810 | 1850.0 - 1910.0 | 1930.0 - 1990.0 | Mainly used in America. Due to frequency overlap, it is incompatible with the 1800M system. |
Source: http://www.blogjava.net/baicker/archive/2013/11/13/406293.html
Next, open Wireshark and sniff the message, selecting the protocol gsm_sms.

As mentioned above, our three networks have basically all been decommissioned, so we need to find a 2G network.
### Extension
To more easily identify data and reduce the steps above, the GSMSniffer project provides a demo for 2G network SMS sniffing and capture, automatically loading the system, scanning base stations, capturing SMS messages, and storing them in a database.
Basic Architecture
- Tengine
- PHP 7.3
- MySQL
The setup steps for the three services above are omitted. Simply clone the project, modify the files, and run it.
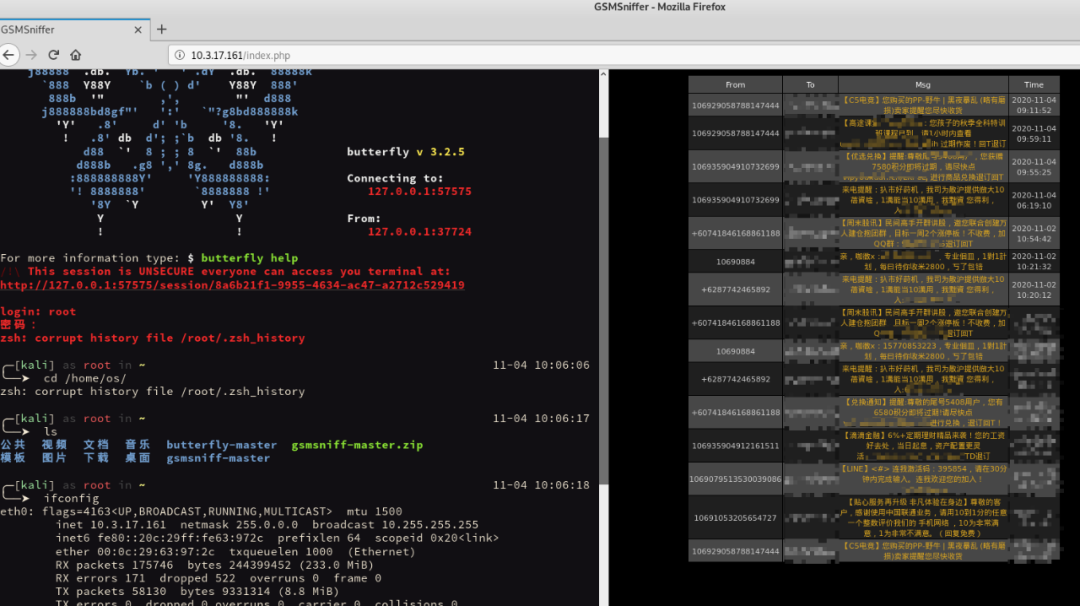
### Defence
Turn on 4G/5G Only on your phone. If it’s not enabled, you can search the phone’s engineering code and enter it to enable it yourself. Switch services. China Mobile’s 2G service still has a little bit of sustenance, China Unicom’s is basically gone, and I don’t know about China Telecom.
I hope this is my last post on GSM SMS sniffing. After all, new technologies tend to reveal vulnerabilities over time. A few days ago, a GeekPwn contestant cracked a certain telecom’s LTE micro base station (Orz).