XMUTCTF 2021 Writeup 0x1
Misc
签到
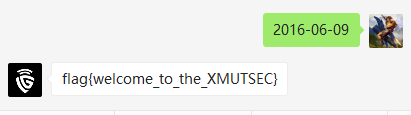
战队成立的日期
word
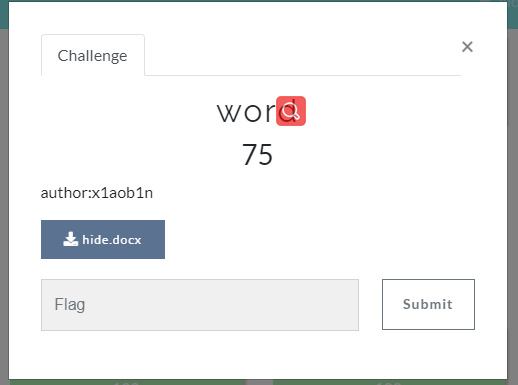
Word文字上个色
flag{code_monster_word_hide}
哦?队标!(二)
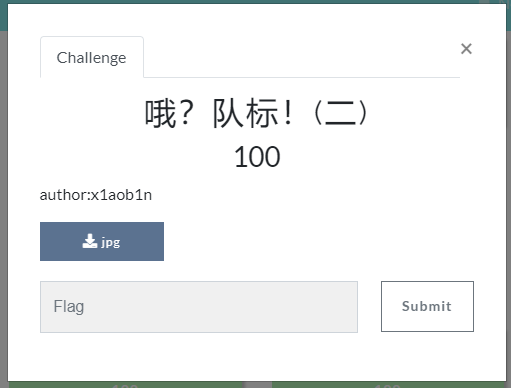
看文件头,发现是 FF D8 FF E0(jpeg)格式,改后缀,得到小恐龙
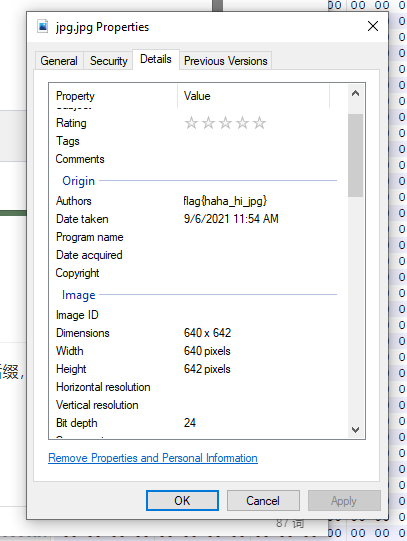
最后,右键属性打开得到flag
熟悉的pdf题,转成Word,把图片挪开即可
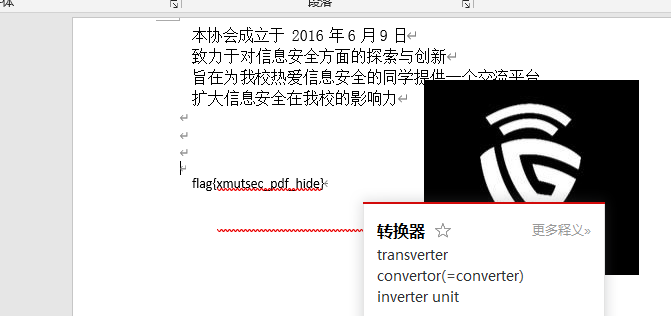
flag{xmutsec_pdf_hide}
你对程序熟悉吗
运行程序,回显 Maybe flag in Resource! 使用 Resource Hacker 打开
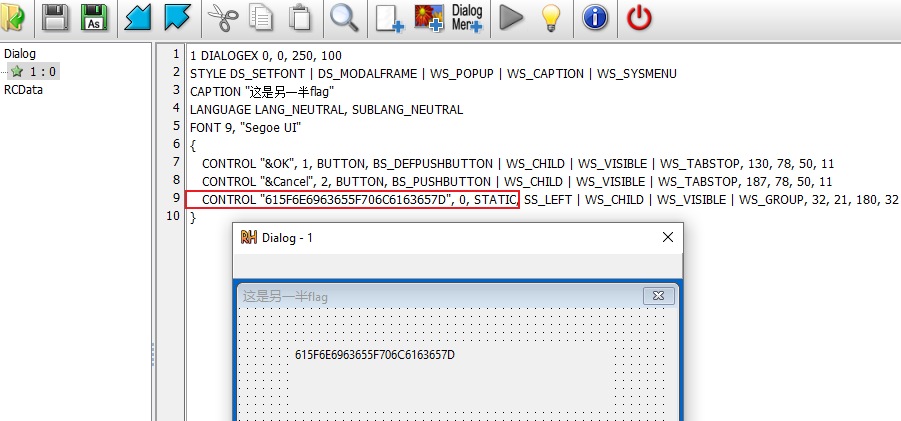
在窗体Label处发现 Hex 编码后的 flag
解密后得到一半flag a_nice_place}
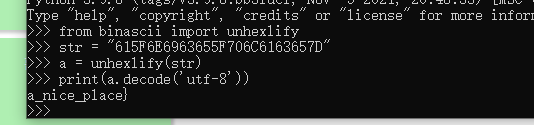
最后在文件末尾处发现逆序后的另一半flag
flag{this_is_a_nice_place}
哥谭恶梦
hex打开,发现文件头被修改了,拉到文件尾,输入正确值
压缩包解压后得到
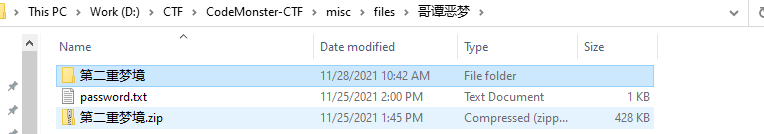
仔细看可以发现password.txt里的内容
解码过程:Hex->Str->base32->base64,解出来的值就是 第二重梦境.zip 的密码
密码:getan
第二重梦境.zip 内容 emo.zip(有密码)
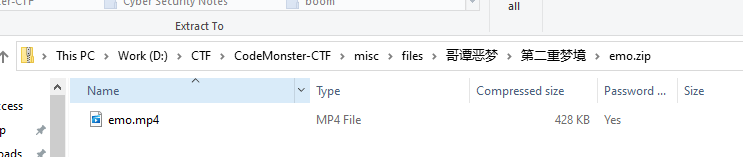
翻了半天,发现密码在文件尾╰(‵□′)╯
解压后得到一个视频,在视频第47帧的时候出现一个BV号
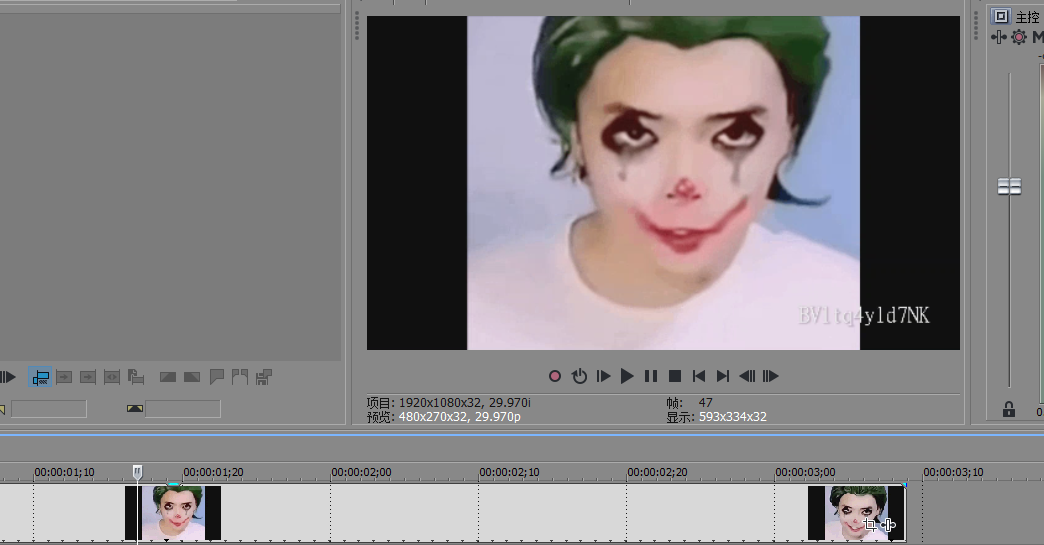
输入视频地址,查看留言板得到flag
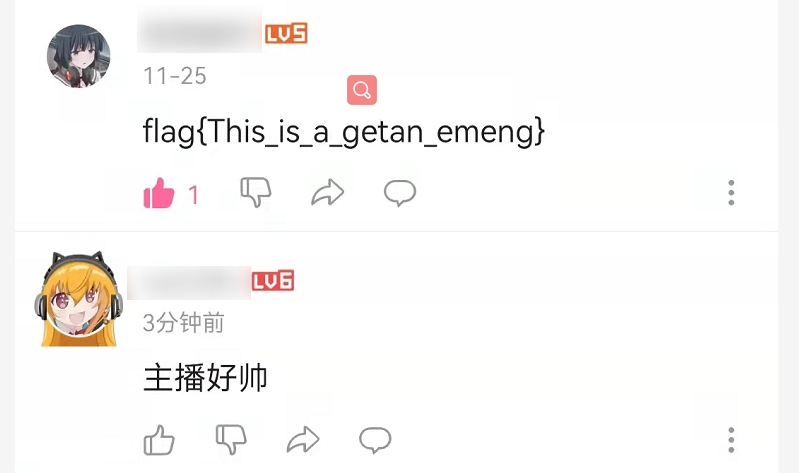
flag{This_is_a_getan_emeng}
你会倒立洗头吗
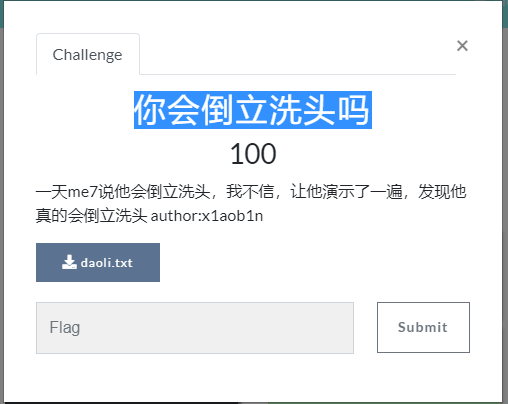
题目打开,发现是一堆十六进制编码
Winhex打开拉到末尾发现文件头为zip,每俩位反转一下,在总体反一下
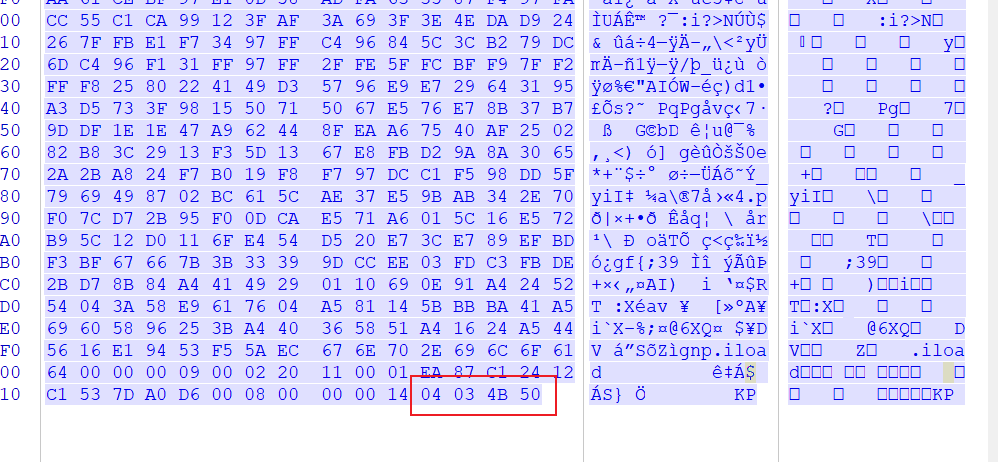
exp
1 | str = "那坨hex" |
脚本跑出来后,解压得到一张图片。图片内容为flag
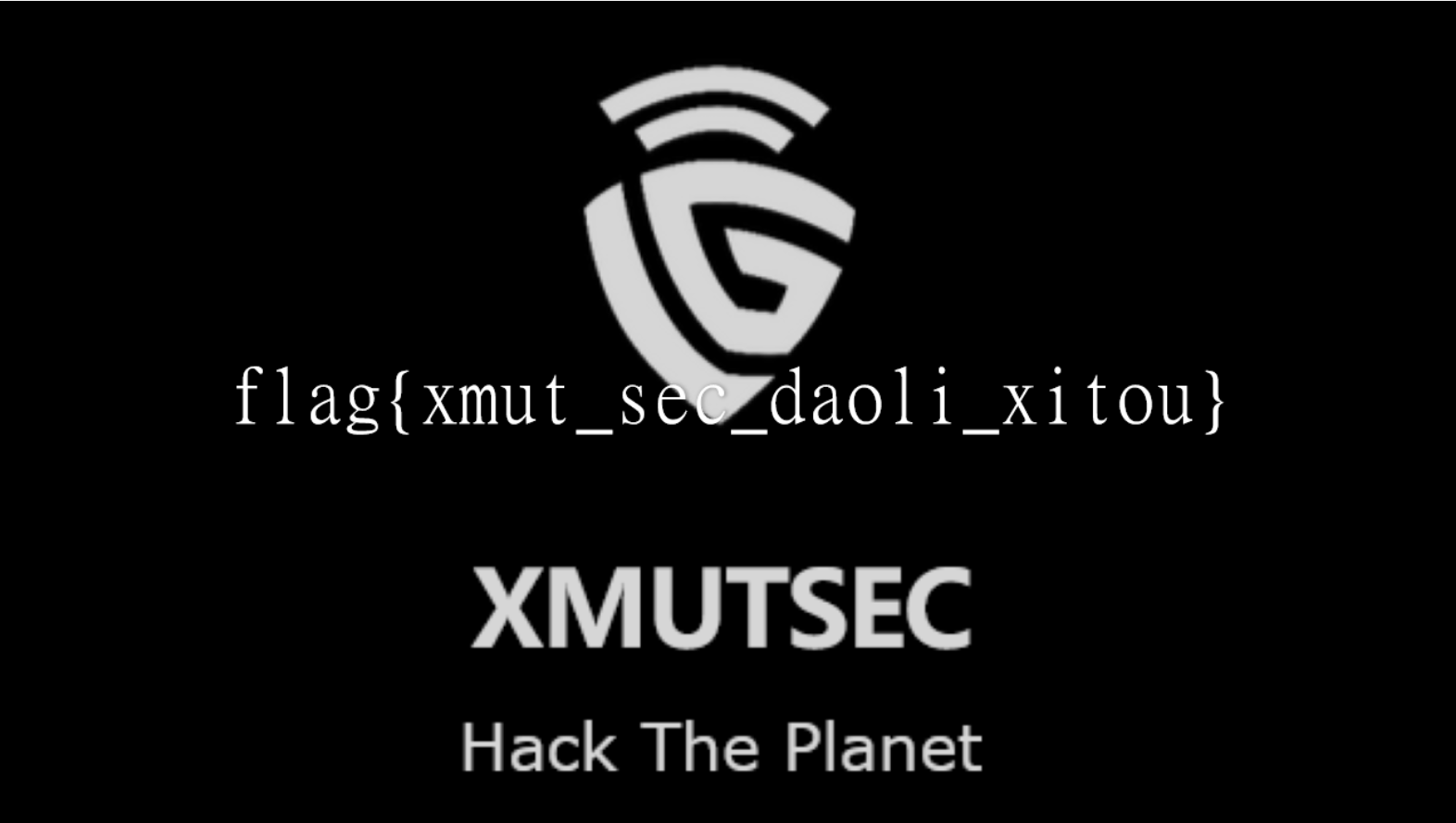
flag{xmut_sec_daoli_xitou}
简单的流量分析
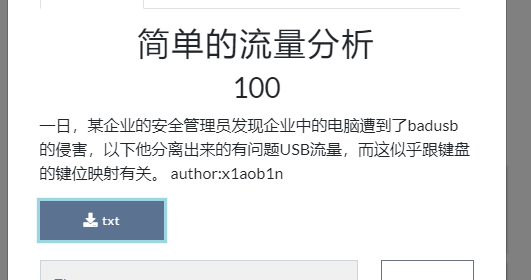
题目得到一堆键位表,写个脚本跑一下就好了0009
1 | 000f |
exp
1 | key="0009 000f 0004 000a 202f 201C 0027 0018 002D 2004 0015 0008 002D 0019 0008 0015 001C 002D 0011 001E 0006 0008 2030" |
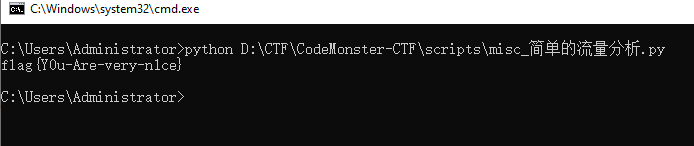
flag{Y0u-Are-very-n1ce}
审查日志,就这吗
文件打开,一堆log
当状态为500的时候出现了base64编码,解码一下即是flag
flag{YouShouJiuXing}
你会破解密码吗
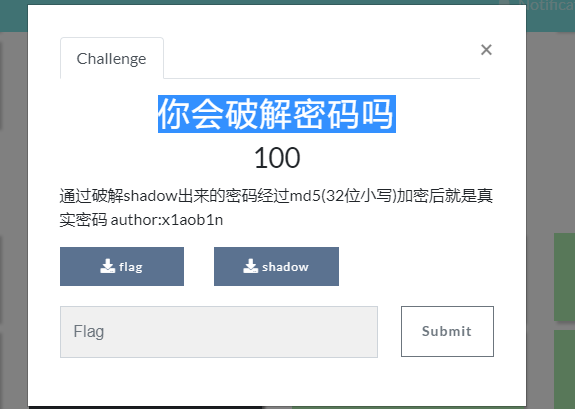
flag文件打开,发现flag(base64后的)
直接上脚本跑
exp
1 | import base64 str="MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA=,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA=,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA=,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA=,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA=,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA=,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA=,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA=,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA=,NTAgNEIgMDMgMDQgMTQgMDAgMDEgMDAgMDAgMDAgMzIgOUYgN0MgNTMgMkQgMEQ=,NDYgNkMgMkYgMDAgMDAgMDAgMjMgMDAgMDAgMDAgMDggMDAgMDAgMDAgNjYgNkM=,NjEgNjcgMkUgNzQgNzggNzQgMjcgMEEgNTcgM0QgMDEgOUUgMjYgMDIgQUUgN0U=,REMgQjIgMTkgQjYgNDEgNUUgQzkgMzUgM0YgMDEgQkMgNjIgNEMgOUUgN0QgRUE=,OUYgMDUgNEQgMDcgMUIgOTEgMkYgODMgNDUgNTIgRUYgREEgOTQgRjMgNjYgNDM=,Q0IgQjYgMTggRkEgQjAgNTAgNEIgMDEgMDIgM0YgMDAgMTQgMDAgMDEgMDAgMDA=,MDAgMzIgOUYgN0MgNTMgMkQgMEQgNDYgNkMgMkYgMDAgMDAgMDAgMjMgMDAgMDA=,MDAgMDggMDAgMjQgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMjAgMDAgMDAgMDAgMDA=,MDAgMDAgMDAgNjYgNkMgNjEgNjcgMkUgNzQgNzggNzQgMEEgMDAgMjAgMDAgMDA=,MDAgMDAgMDAgMDEgMDAgMTggMDAgNDkgNkMgRUEgMjEgNEYgRTQgRDcgMDEgMjQ=,MEEgMTUgODQgNEYgRTQgRDcgMDEgMjYgNDMgQkYgMTYgNEYgRTQgRDcgMDEgNTA=,NEIgMDUgMDYgMDAgMDAgMDAgMDAgMDEgMDAgMDEgMDAgNUEgMDAgMDAgMDAgNTU=,MDAgMDAgMDAgMDAgMDA=" #str="MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA,MDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMDA,NTAgNEIgMDMgMDQgMTQgMDAgMDEgMDAgMDAgMDAgMzIgOUYgN0MgNTMgMkQgMEQ,NDYgNkMgMkYgMDAgMDAgMDAgMjMgMDAgMDAgMDAgMDggMDAgMDAgMDAgNjYgNkM,NjEgNjcgMkUgNzQgNzggNzQgMjcgMEEgNTcgM0QgMDEgOUUgMjYgMDIgQUUgN0U,REMgQjIgMTkgQjYgNDEgNUUgQzkgMzUgM0YgMDEgQkMgNjIgNEMgOUUgN0QgRUE,OUYgMDUgNEQgMDcgMUIgOTEgMkYgODMgNDUgNTIgRUYgREEgOTQgRjMgNjYgNDM,Q0IgQjYgMTggRkEgQjAgNTAgNEIgMDEgMDIgM0YgMDAgMTQgMDAgMDEgMDAgMDA,MDAgMzIgOUYgN0MgNTMgMkQgMEQgNDYgNkMgMkYgMDAgMDAgMDAgMjMgMDAgMDA,MDAgMDggMDAgMjQgMDAgMDAgMDAgMDAgMDAgMDAgMDAgMjAgMDAgMDAgMDAgMDA,MDAgMDAgMDAgNjYgNkMgNjEgNjcgMkUgNzQgNzggNzQgMEEgMDAgMjAgMDAgMDA,MDAgMDAgMDAgMDEgMDAgMTggMDAgNDkgNkMgRUEgMjEgNEYgRTQgRDcgMDEgMjQ,MEEgMTUgODQgNEYgRTQgRDcgMDEgMjYgNDMgQkYgMTYgNEYgRTQgRDcgMDEgNTA,NEIgMDUgMDYgMDAgMDAgMDAgMDAgMDEgMDAgMDEgMDAgNUEgMDAgMDAgMDAgNTU,MDAgMDAgMDAgMDAgMDA" |
最后得到一个zip
john跑一下shadow即可,密码为:e10adc3949ba59abbe56e057f20f883e
flag(welcome_to_the_codemonsterCTF}
Crypto
一顿午饭
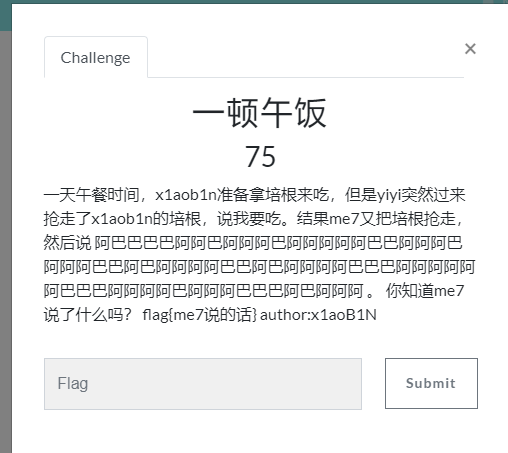
培根密码,把阿替换成A,巴替换成B,即可
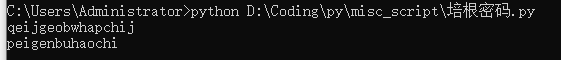
flag{peigenbuhaochi}
高等数学
高数题。。。。学长的字真好看
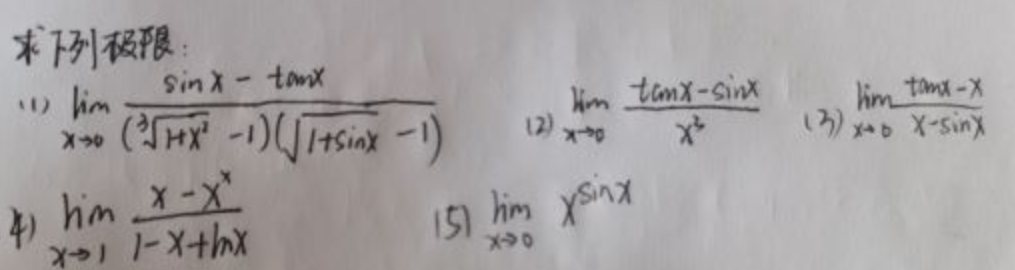
(1)
$$\lim\limits_{x \to 0}\frac{sinx-tanx}{(^3\sqrt{1+x^2}-1)(\sqrt{1+sinx}-1)}$$
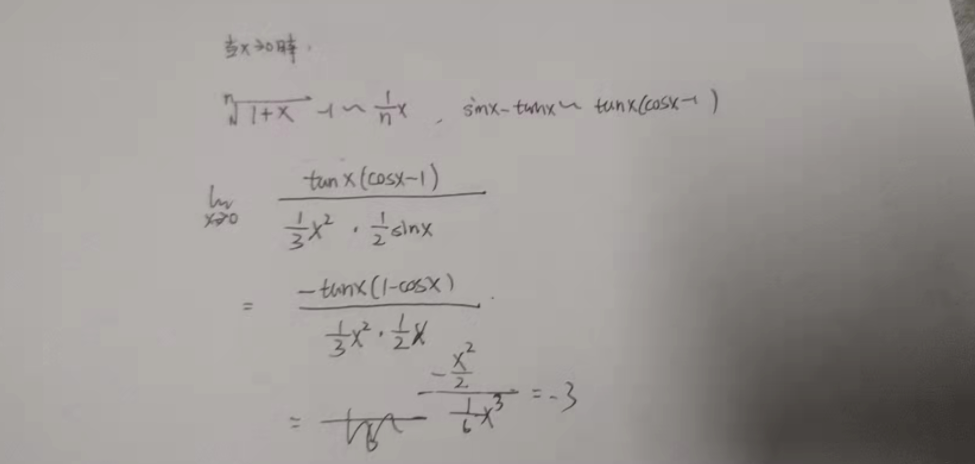
(2)
$$\lim\limits_{x \to 0}\frac{tanx-sinx}{x^3}$$
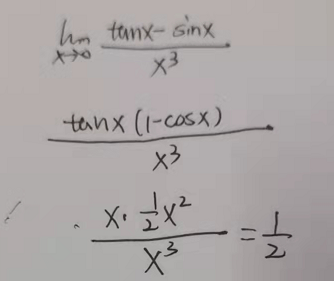
(3)
$$\lim\limits_{x \to 0}\frac{tanx-x}{x-sinx}$$
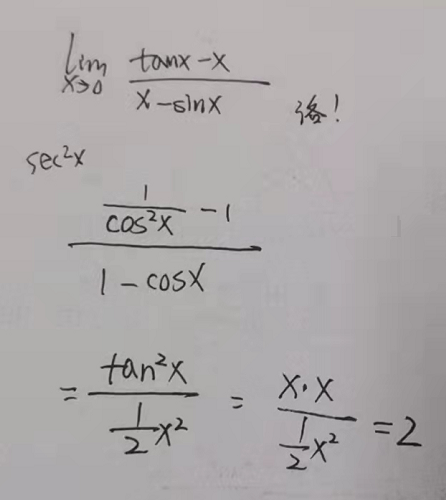
(4)
$$\lim\limits_{x \to 1}\frac{x-x^x}{1-x+\ln{x}}$$
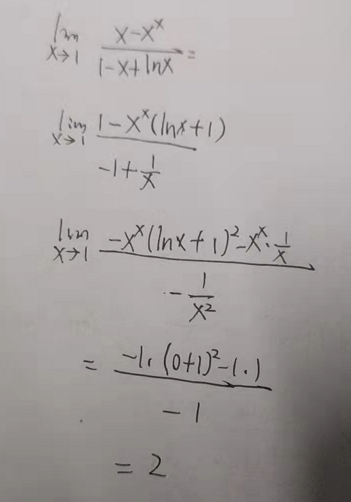
(5)
$$\lim\limits_{x \to 0}x^{\sin{x}}
flag{-3-1/2-2-2-1}
flag{-3-0.5-2-2-1}
线性代数

(1)
$$\begin{vmatrix}
1 & 2 & 3 \
3 & 1 & 2 \
2 & 3 & 1 \
\end{vmatrix}$$
$$111+333+222-312-231-231=18$$
(2)
$$\begin{pmatrix}
1 & 1 & 2 \
1 & -1 & 0 \
\end{pmatrix}
\begin{pmatrix}
3 & 4 \
5 & 4 \
2 & 7 \
\end{pmatrix}$$

easy_rsa
给出q、p、c、e
1 | q= 9961202707366965556741565662110710902919441271996809241009358666778850435448710324711706845973820669201482939820488174382325795134659313309606698334978471 |
这题不难,求出n,在求出d就可以了
1 | import gmpy2 |
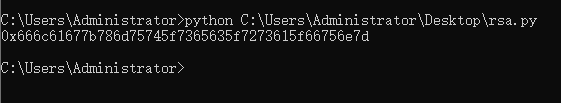
flag{xmut_sec_rsa_fun}
在社会主义下的base家族
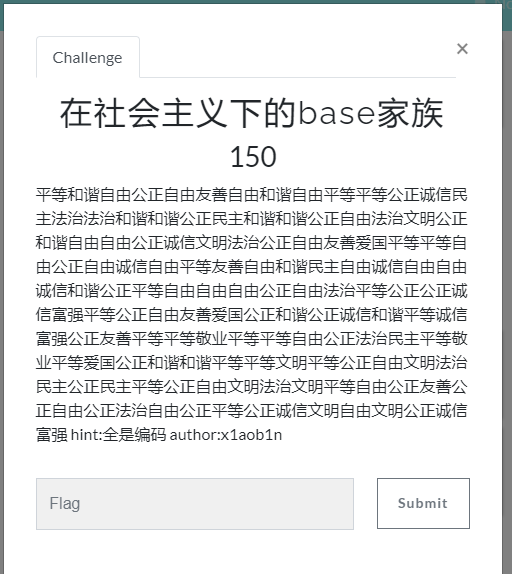
主要考查社会主义编码(SC+999999999999999999999999999999999999999)
解出来得:SFJ4Ukw3a3drcDlvNUFNZ1NMeDFGVjVNcmZkYUFqYXc5RVBqaVBrTlFtelBj
这串为base64,然后根据题意base大家族,base1-100,全部解一遍,最后解码方式base58->base85->base92
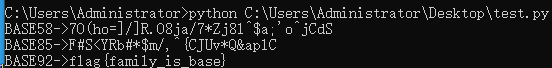
flag{family_is_base}
对称加密
科普:常见的对称加密有DES、AES、RC、Rabbit
这里题目用到的是DES-ECB方式
压缩包解压后得到
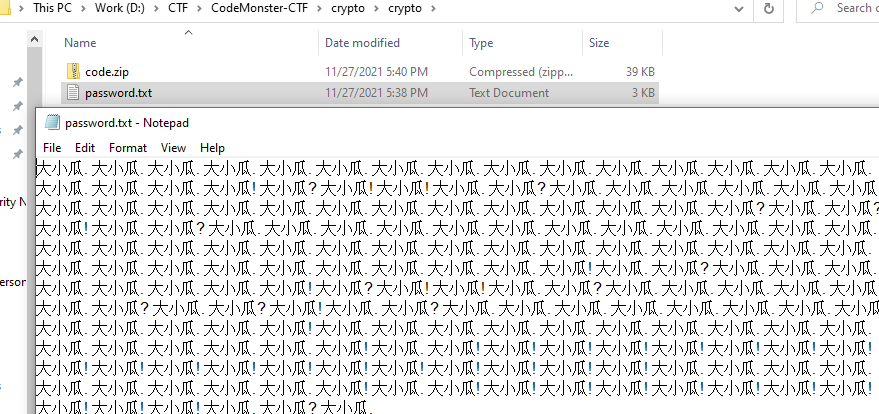
ook!编码,解得密码为:crypto,解压后分别扫码

Code1为:BuB+pJN5H0UFTZ02R+
Code2为:IMCYZ0YvimZWU49h8Nh2IXyPtB6YdfmlV7V79/VxVzw+bx
密码为:XMUTSEC

最后解得:flag{this_a_des_code}
探索中世纪城堡
题目描述(要素察觉)
1 | xxxxxxxxxx 年轻的大帝率领着64位皇珈骑士冲破了双重阻栏夺下了城池。 |
凯撒解密后得到
1 | fa{usrb_oXaga_aoaglgsbciet_inwndmwn} |
最后栏数设置为2即可
flag{subscribe_to_Xiangwan_damowang}
XMUTCTF 2021 Writeup 0x1