DN42实验网络初次尝试
DN42网络是什么?
去中心化网络42(decentralized network 42,简称为 dn42,下略),是一个去中心化、端到端加密的网络,它通过使用 VPN 和软件/硬件的边界网关协议进行构建,但是与其它传统 VPN 不同的是,DN42 本身不提供 VPN 出口服务,即不提供规避网络审查、流媒体解锁等类似服务。相反,DN42 的目的是模拟一个互联网。它使用了大量在目前互联网骨干上应用的技术(例如 BGP 和递归 DNS),可以很好地模拟一个真实的网络环境。
Via Lan Tian’s Blog
### Why DN42
#### 路由实验
Participating in dn42 is primarily useful for learning routing technologies such as BGP, using a reasonably large network (> 1500 AS, > 1700 prefixes).
Since dn42 is very similar to the Internet, it can be used as a hands-on testing ground for new ideas, or simply to learn real networking stuff that you probably can’t do on the Internet (BGP multihoming, transit). The biggest advantage when compared to the Internet: if you break something in the network, you won’t have any big network operator yelling angrily at you.
#### 连接黑客空间
dn42 is also a great way to connect hacker spaces in a secure way, so that they can provide services to each other.
Have you ever wanted to SSH on your Raspberry Pi hosted at your local hacker space and had trouble doing so because of NAT? If your hacker space was using dn42, it could have been much easier…
Via Home (dn42.dev)
### Register DN42
#### 要求
- 拥有一台Linux虚拟机,Windows的话使用WSL即可
- 熟悉Linux命令,有一定的寄网(计算机网络寄础)基础
官网教程:https://dn42.dev/howto/Getting-Started
首先到 git 上申请一个账号(https://git.dn42.dev/user/sign_up),激活完成后,到这个仓库(https://git.dn42.dev/dn42/registry)fork一份到你本地上。
接着 clone 一份到本地。
1 | git clone https://git.dn42.dev/icecliffs/registry.git |
- 然后在
data/mntner下新建一个[大写昵称]-MNT的文件,抓到tony师傅惹。
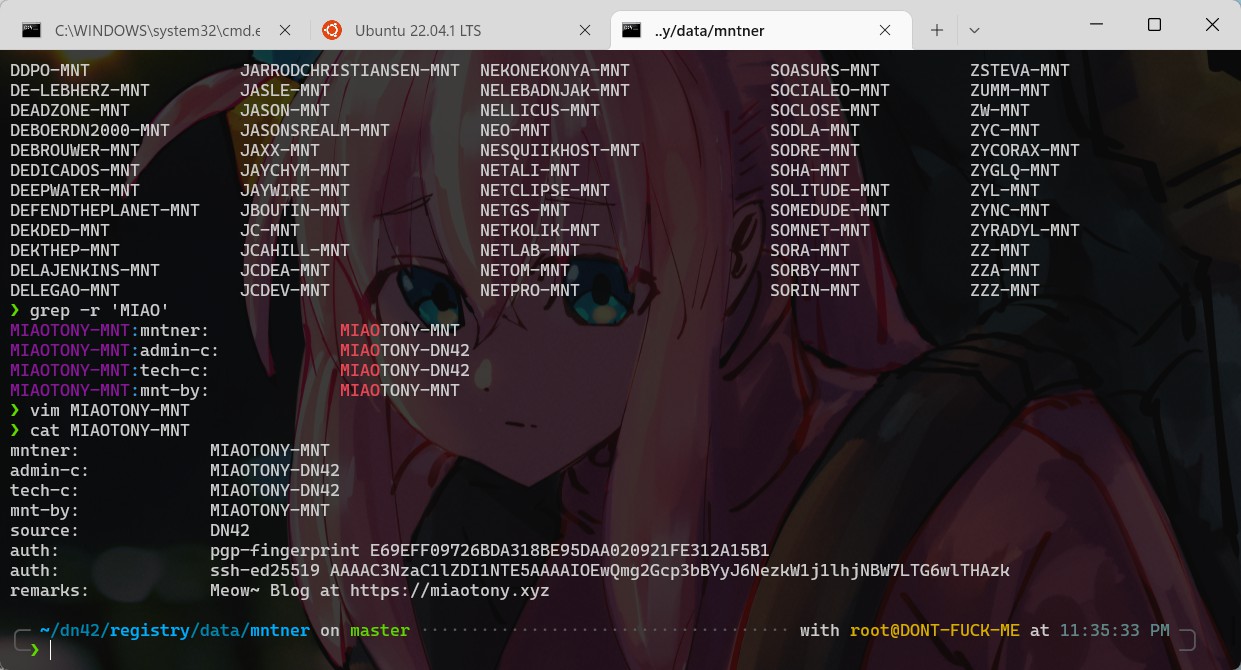
内容为
mntner:即maintainer(维护者),说明这个账户的名称,与文件名相同。admin-c:即admin contact(管理员联系信息),需要指向后续创建的 person 文件,一般为[昵称]-DN42。tech-c:即tech contact(技术员联系信息),需要指向后续创建的 person 文件,一般也为[昵称]-DN42。mnt-by:即maintain by(由谁维护),指向这个账户本身,一般为[昵称]-MNT。source:固定为DN42。auth:你的个人认证信息。一般接受两种类型:GPG 公钥和 SSH 公钥。
Via DN42 实验网络介绍及注册教程
1 | mntner: ICECLIFFS-MNT |
- 在
data/person下新建一个[大写昵称]-DN42的文件
内容为
person:你的昵称。e-mail:你的邮箱。contact:可选,你的其它联系方式,例如 IRC、Telegram 等。nic-hdl:NIC handle,指向文件本身,与文件名相同,[昵称]-DN42。mnt-by:maintain by(由谁维护),由谁维护,指向你之前的 mntner 文件,[昵称]-MNT。source:固定为DN42。
1 | person: rYu1nser |
- 接着要分配一个 ASN编号 ,这里随便挑一个你喜欢的(范围:4242420000 - 4242423999),例如我的是
AS4242422291截至 2022/12/3 00:00:00 应该还有这么多编号
1 | aut-num: AS4242422291 |
剩下的步骤我懒得写了,建议看lantian师傅的,我是照着他那个来做的()
指路🔜:DN42 实验网络介绍及注册教程(2022-06 更新) | Lan Tian @ Blog
我的IPv6:fd6d:acf4:0742::_48
我的IPv4:172.23.244.0/26
关于IP段,在这里可以找到dn42未分配的IP段,https://explorer.burble.com/free#/
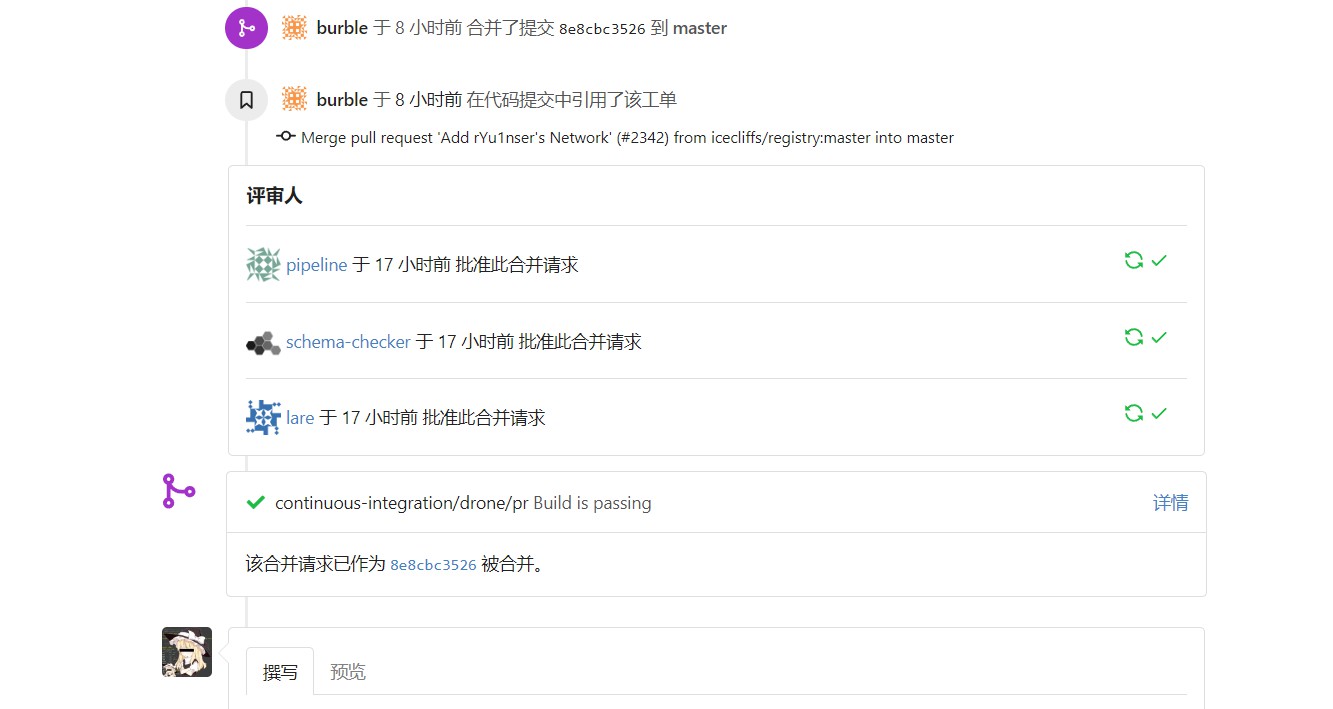
我的PR,可以说是惨不忍睹惹 :D:https://git.dn42.dev/dn42/registry/pulls/2342
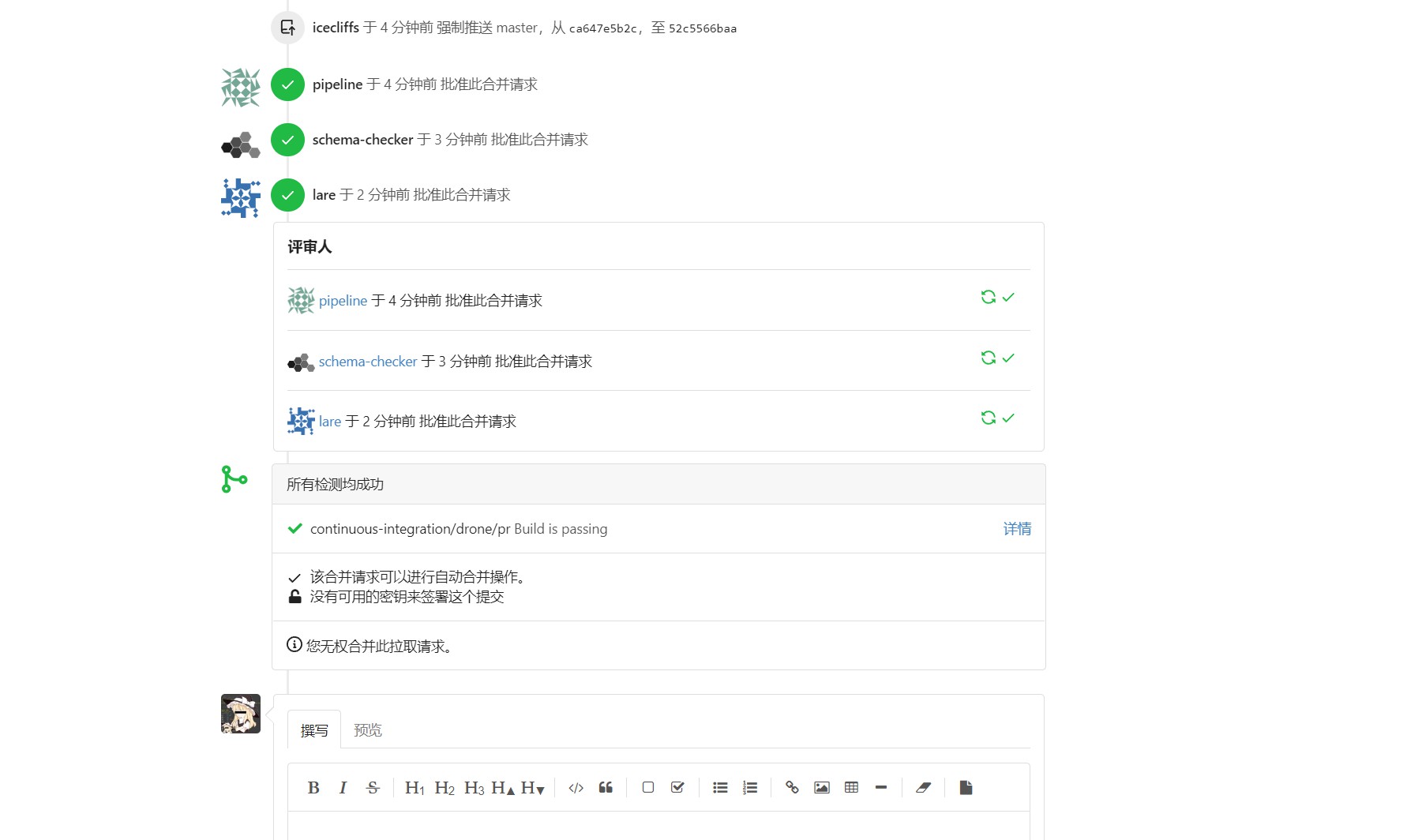
之后慢慢等,等他把你合并。
1 | [NOTE] ## Scan Started at 2022-12-03 18:51:34 |
### 建立Peer
由于DN42是模拟一整个互联网,因此没有任何官方服务器供我们接入,我们需要自己接入一台服务器到DN42里边。
配置之前现在 sysctl.conf 里边加几条配置,https://dn42.dev/howto/networksettings
一定要关闭
rp_filter并开启转发功能The first rule of dn42: Always disable
rp_filter.The third rule of dn42: Allow ip forwarding!
记得一定要关掉防火墙,否则会出现一些不可抗力的事
1 | net.ipv4.ip_forward=1 |
生效:sysctl -p
#### 寻找Peer节点
或者到其他人的博客/网站上看看有没有。
例如我的:
1 | Name : ICECLIFFS-NET |
#### 建立隧道
这里建议参考官方教程:https://dn42.dev/howto/wireguard
首先生成公私钥
1 | wg genkey | tee privatekey | wg pubkey > publickey |
如果出现命令未找到,这是因为你没安装 Wireguard
1 | apt-get update |
然后在 /etc/wireguard/ 下改改配置
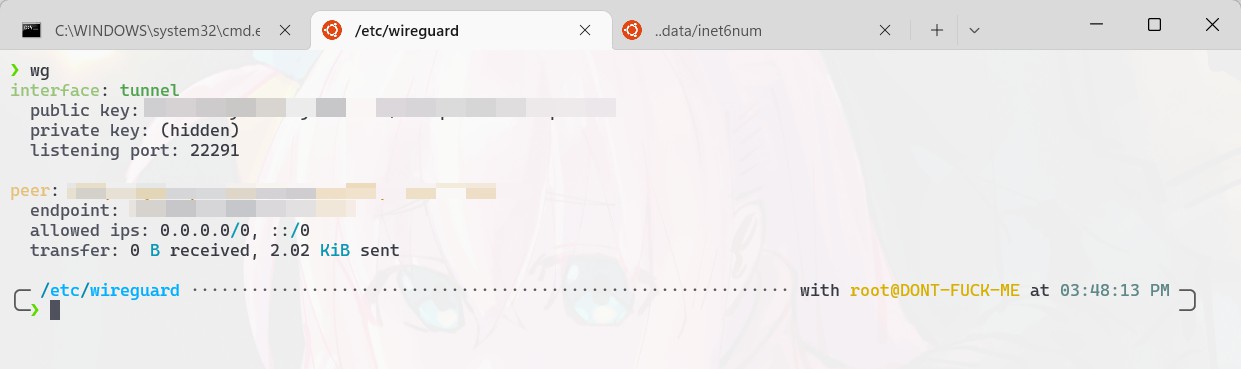
1 | # tunnel.conf |
改后好直接 wg-quick up [配置文件] 即可,然后敲一下 wg 看看能不能成功连上,如果成功连上会显示 [label]Transfer [/label] 字样
如果
#### 建立BGP会话
这里建议照着官网来做
安装
1 | wget -O - http://bird.network.cz/debian/apt.key | apt-key add - |
建议直接套模板 https://wiki.dn42.us/howto/Bird2
Replace
<OWNAS>with your autonomous system number, e.g.4242421234Replace
<OWNIP>with the ip that your router is going to have, this is usually the first non-zero ip in your subnet. (E.g. x.x.x.65 in an x.x.x.64/28 network)Similarly, replace
<OWNIPv6>with the first non-zero ip in your ipv6 subnet.Then replace
<OWNNET>with the IPv4 subnet that was assigned to you.The same goes for
<OWNNETv6>, but it takes an IPv6 subnet (Who’d have thought).Keep in mind that you’ll have to enter both networks in the OWNNET{,v6} and OWNNETSET{,v6}, the two variables are required due to set parsing difficulties with variables.
然后按照上述替换一下(/etc/bird.conf)
1 | ################################################ |
接着配置一下 ROA (Route Origin Authorization),这个一定要配好,可以写个 crontab 让他定时下载文件
The example config above relies on ROA configuration files in /etc/bird/roa_dn42{,_v6}.conf. These should be automatically downloaded and updated every so often to prevent BGP highjacking, see the bird1 page for more details and links to the ROA files. Note: edit the links to replace roa_bird1 to say roa_bird2 if using the cron jobs listed on that page.
详见:https://wiki.dn42.us/howto/Bird#route-origin-authorization0
#### 设置Peers
Please note: This section assumes that you’ve already got a tunnel to your peering partner setup.
在这里新建个文件夹
1 | # mkdir -p /etc/bird/peers |
详见:https://wiki.dn42.us/howto/Bird2
全部配置好后启动Bird bird -c /etc/bird.conf
查看连接状态:birdc show protocol
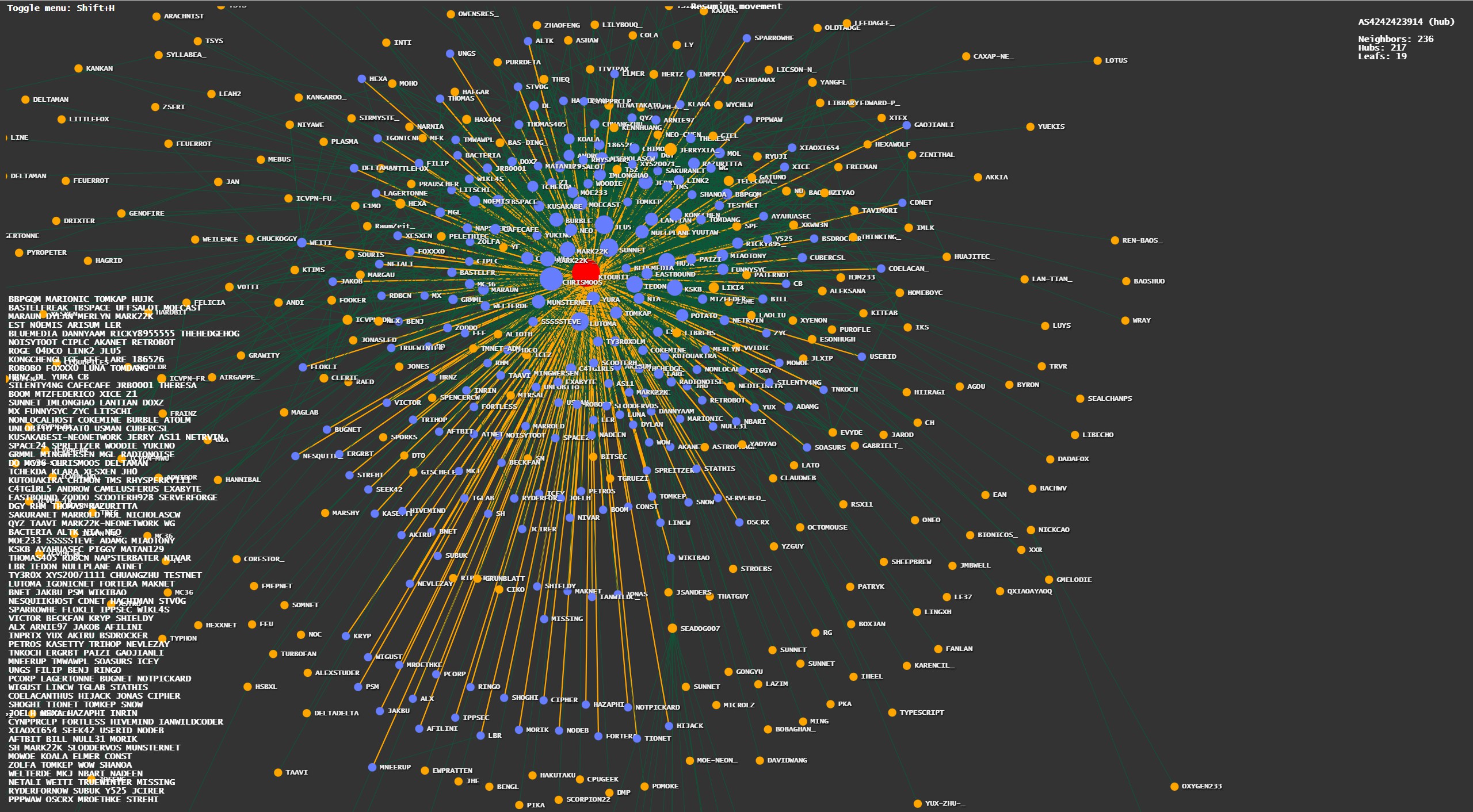
### 图形化

https://dn42.jh0project.com/map

### 参考
https://miaotony.xyz/2021/03/25/Server_DN42
https://lantian.pub/article/modify-website/dn42-experimental-network-2020.lantian/
DN42实验网络初次尝试