打着玩
时隔4个月又来打CTF了,啊,要死要死,菜的要死
decrypt_it
流量包抓大头,跟踪TCP协议,提取出脚本
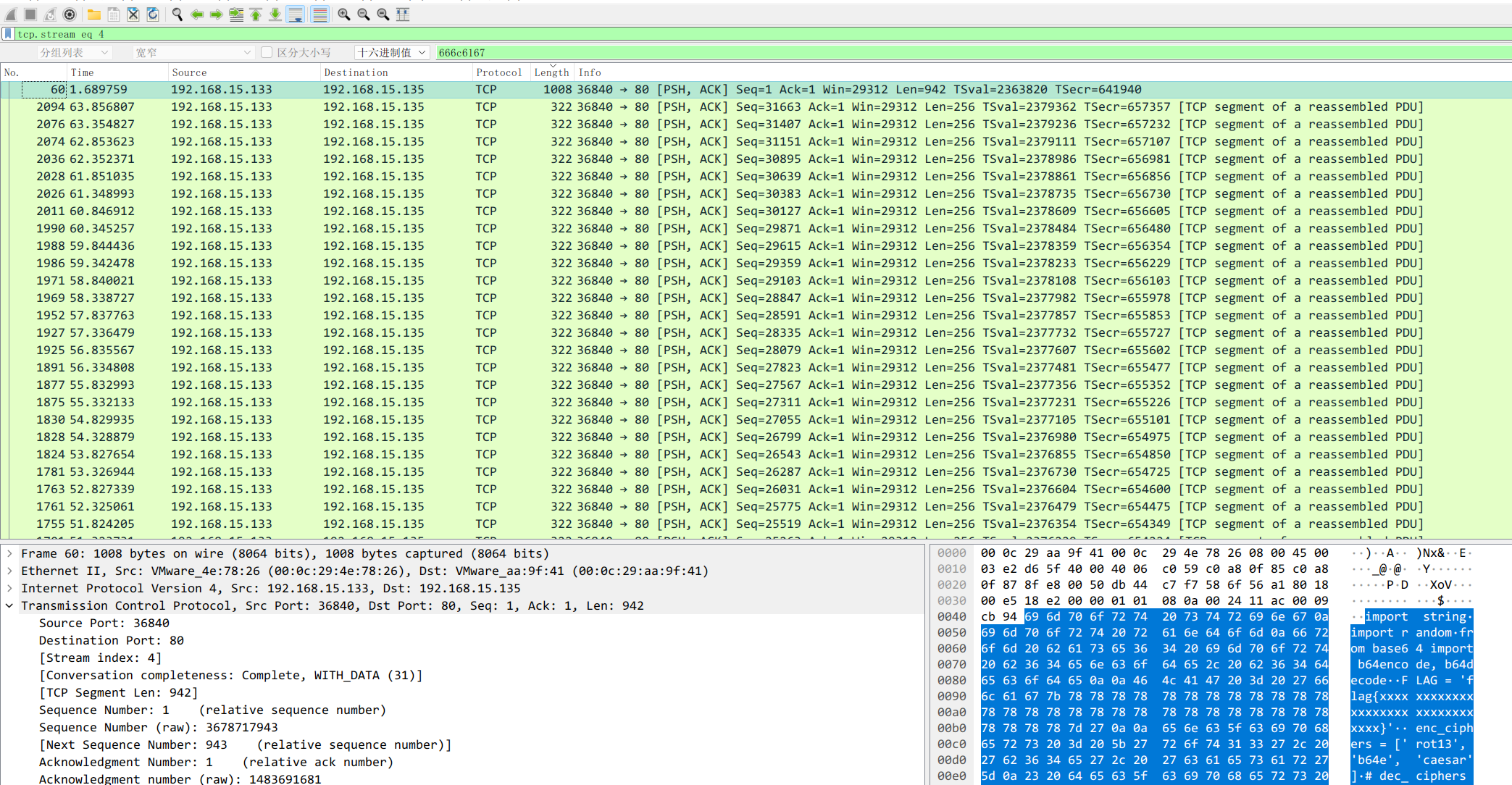
脚本如下
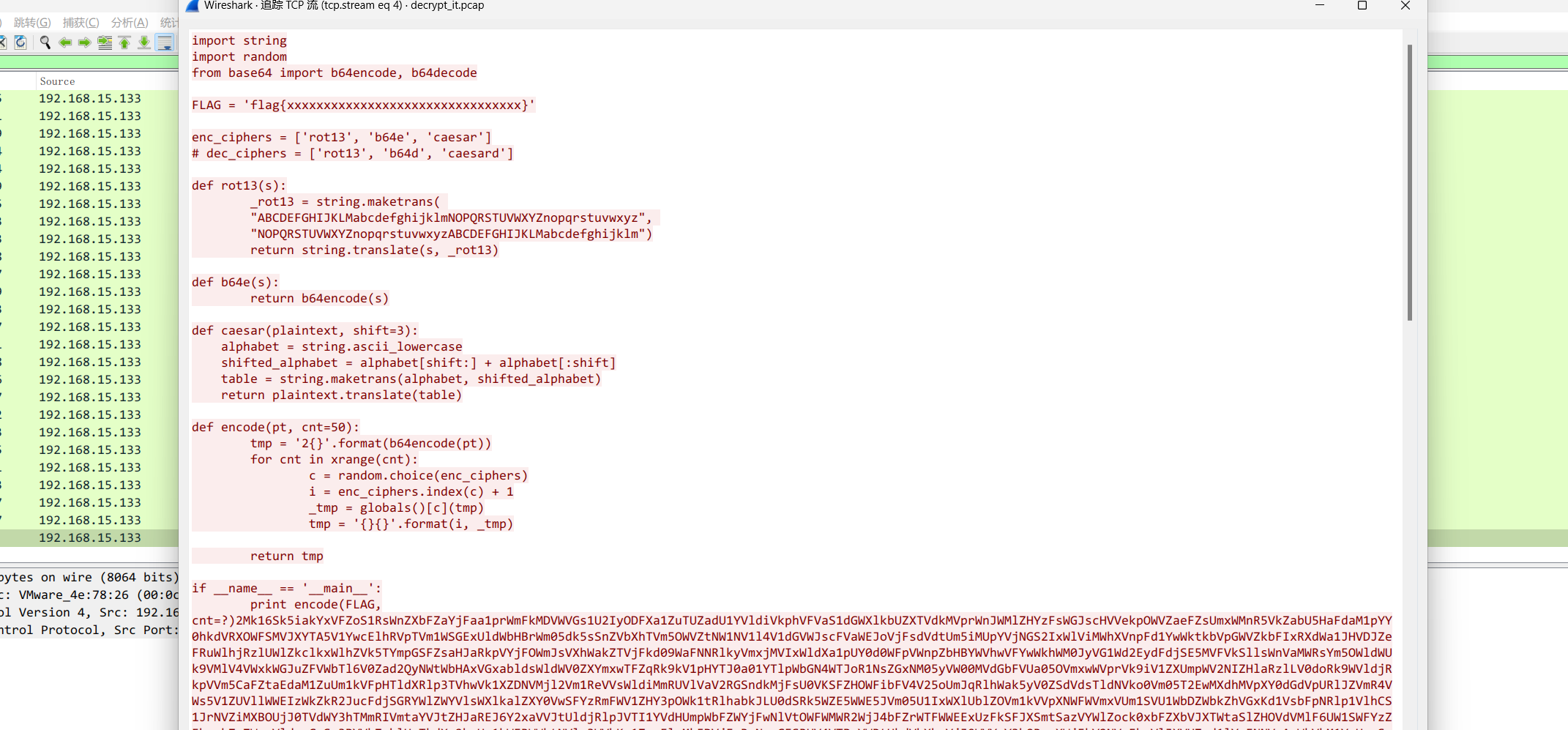
脚本不难,具体加密流程就是enc随机数组选一个值然后index放在编码后的最前面
大概这个样子
- 如果 enc = 1
- 或者 enc = 2
- 或者 enc = 3
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
| import string
import random
from base64 import b64encode, b64decode
FLAG = 'flag{xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx}'
enc_ciphers = ['rot13', 'b64e', 'caesar']
# dec_ciphers = ['rot13', 'b64d', 'caesard']
def rot13(s):
_rot13 = string.maketrans(
"ABCDEFGHIJKLMabcdefghijklmNOPQRSTUVWXYZnopqrstuvwxyz",
"NOPQRSTUVWXYZnopqrstuvwxyzABCDEFGHIJKLMabcdefghijklm")
return string.translate(s, _rot13)
def b64e(s):
return b64encode(s)
def caesar(plaintext, shift=3):
alphabet = string.ascii_lowercase
shifted_alphabet = alphabet[shift:] + alphabet[:shift]
table = string.maketrans(alphabet, shifted_alphabet)
return plaintext.translate(table)
def encode(pt, cnt=50):
tmp = '2{}'.format(b64encode(pt))
for cnt in xrange(cnt):
c = random.choice(enc_ciphers)
i = enc_ciphers.index(c) + 1
_tmp = globals()[c](tmp)
tmp = '{}{}'.format(i, _tmp)
return tmp
if __name__ == '__main__':
print encode(FLAG,
|
解码脚本如下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
| import string
import random
from base64 import b64encode, b64decode
FLAG = 'flag{xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx}'
enc_ciphers = ['rot13', 'b64e', 'caesar']
dec_ciphers = ['rot13', 'b64d', 'caesard']
def rot13(s):
_rot13 = string.maketrans(
"ABCDEFGHIJKLMabcdefghijklmNOPQRSTUVWXYZnopqrstuvwxyz",
"NOPQRSTUVWXYZnopqrstuvwxyzABCDEFGHIJKLMabcdefghijklm")
return string.translate(s, _rot13)
def b64e(s):
return b64encode(s)
def b64d(s):
return b64encode(s)
def caesard(plaintext, shift=-3):
alphabet = string.ascii_lowercase
shifted_alphabet = alphabet[shift:] + alphabet[:shift]
table = string.maketrans(alphabet, shifted_alphabet)
return plaintext.translate(table)
def caesar(plaintext, shift=3):
alphabet = string.ascii_lowercase
shifted_alphabet = alphabet[shift:] + alphabet[:shift]
table = string.maketrans(alphabet, shifted_alphabet)
return plaintext.translate(table)
def encode(pt, cnt=1):
tmp = '2{}'.format(b64encode(pt))
for cnt in xrange(cnt):
c = random.choice(enc_ciphers)
print(c)
i = enc_ciphers.index(c) + 1
print(i)
_tmp = globals()[c](tmp)
print(_tmp)
tmp = '{}{}'.format(i, _tmp)
return tmp
def decode(pt):
if (str(pt).startswith("2")):
pt = b64decode(pt[1:])
return pt
elif(str(pt).startswith("3")):
pt = caesard(pt[1:])
return pt
elif(str(pt).startswith("1")):
pt = rot13(pt[1:])
return pt
for i in range(100):
flag = decode(flag)
print(flag)
|
跑一下就好了
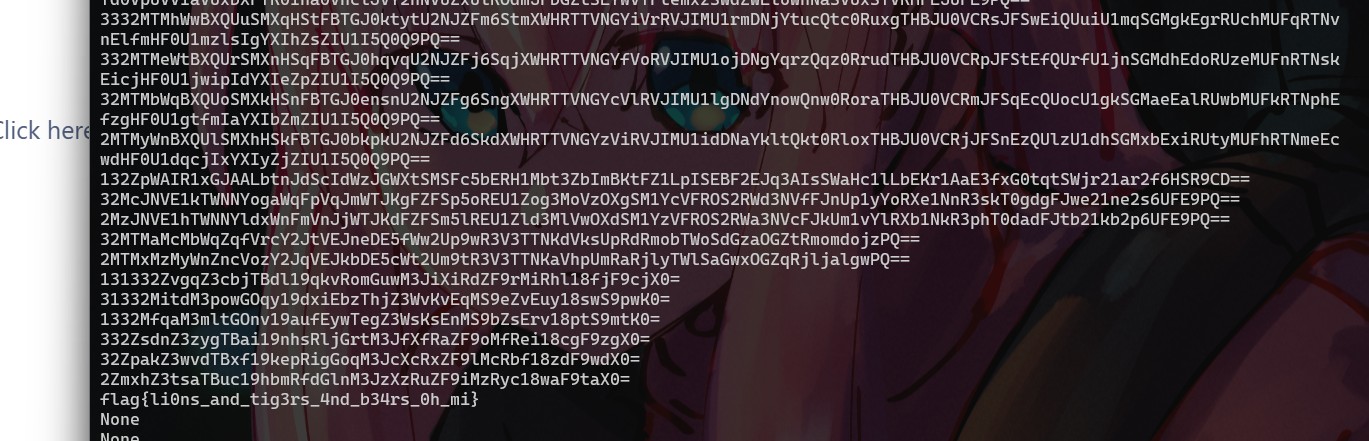
shell
流量包分离 flag.zip 压缩包
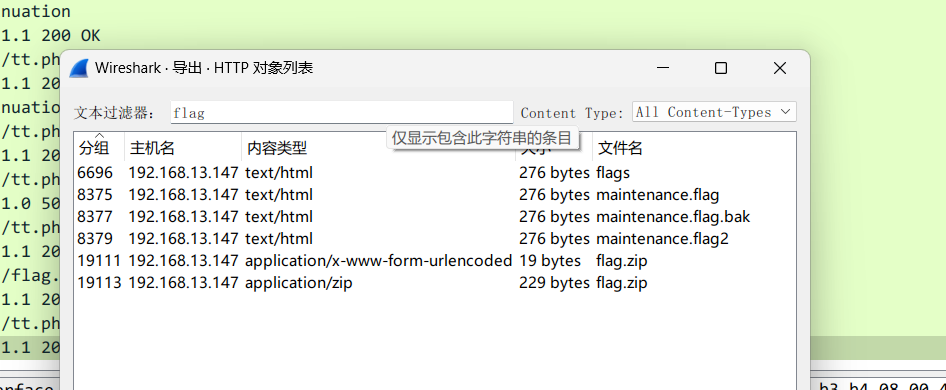
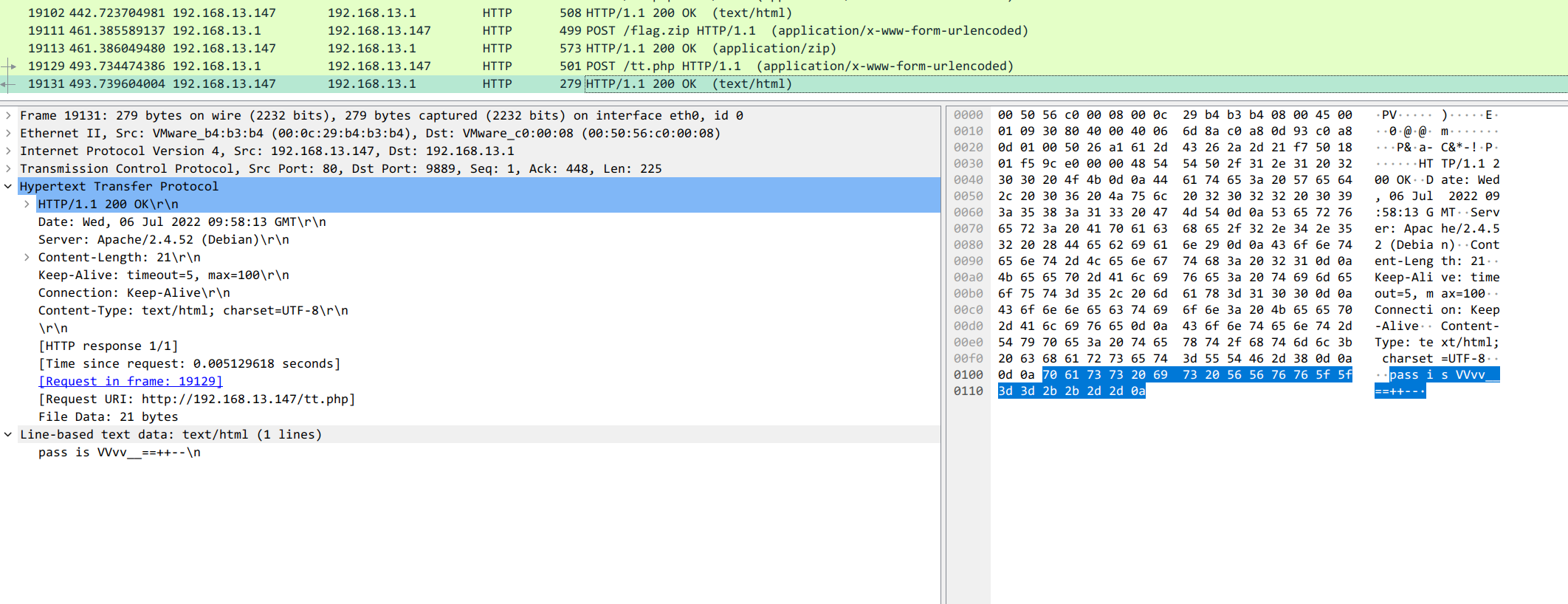
密码在流浪包最后一个位置,密码为 VVvv__==++--
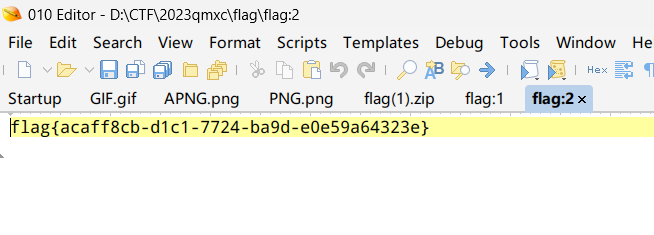
解压获得flag
注入分析
比较暴力,时间=1说明执行成功,时间=3说明执行失败,写个脚本跑一下
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
| # -*- coding: utf-8 -*-
# @Author: rYu1nser
# @Date: 2023-04-11
# @Last Modified by: rYu1nser
# @Last Modified time: 2023-04-11
from datetime import datetime
import urllib.parse
date_format = '%d/%b/%Y:%H:%M:%S %z'
with open('log', 'r') as f:
last_line = None
last_time = None
for line in f:
if last_time is not None:
current_time_str = line.split('[')[1].split(']')[0]
current_time = datetime.strptime(current_time_str, date_format)
time_difference = current_time - last_time
if time_difference.total_seconds() < 3:
s= urllib.parse.unquote(last_line)
print(s[143:])
last_line = line
last_time_str = line.split('[')[1].split(']')[0]
last_time = datetime.strptime(last_time_str, date_format)
|
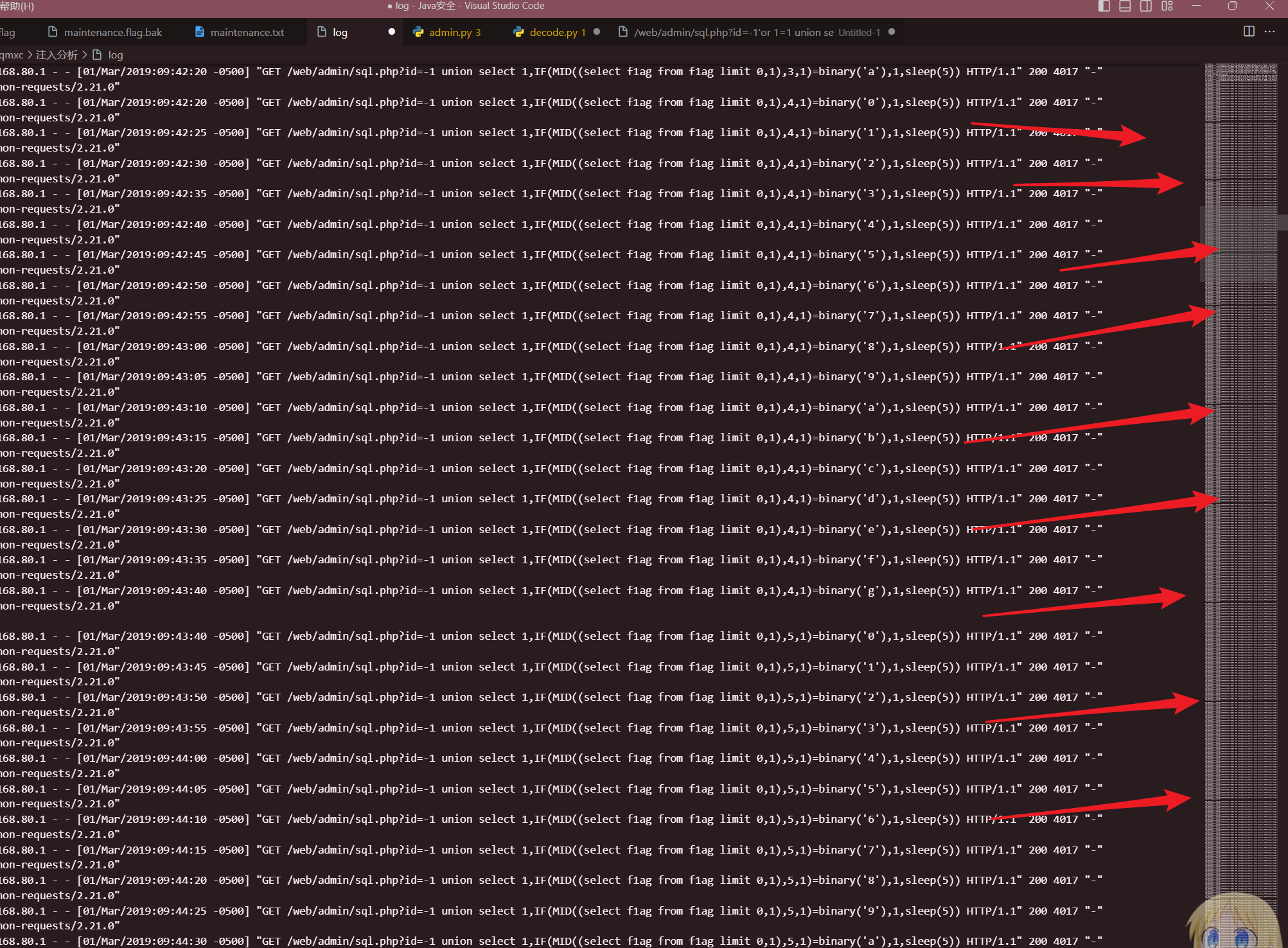
结果
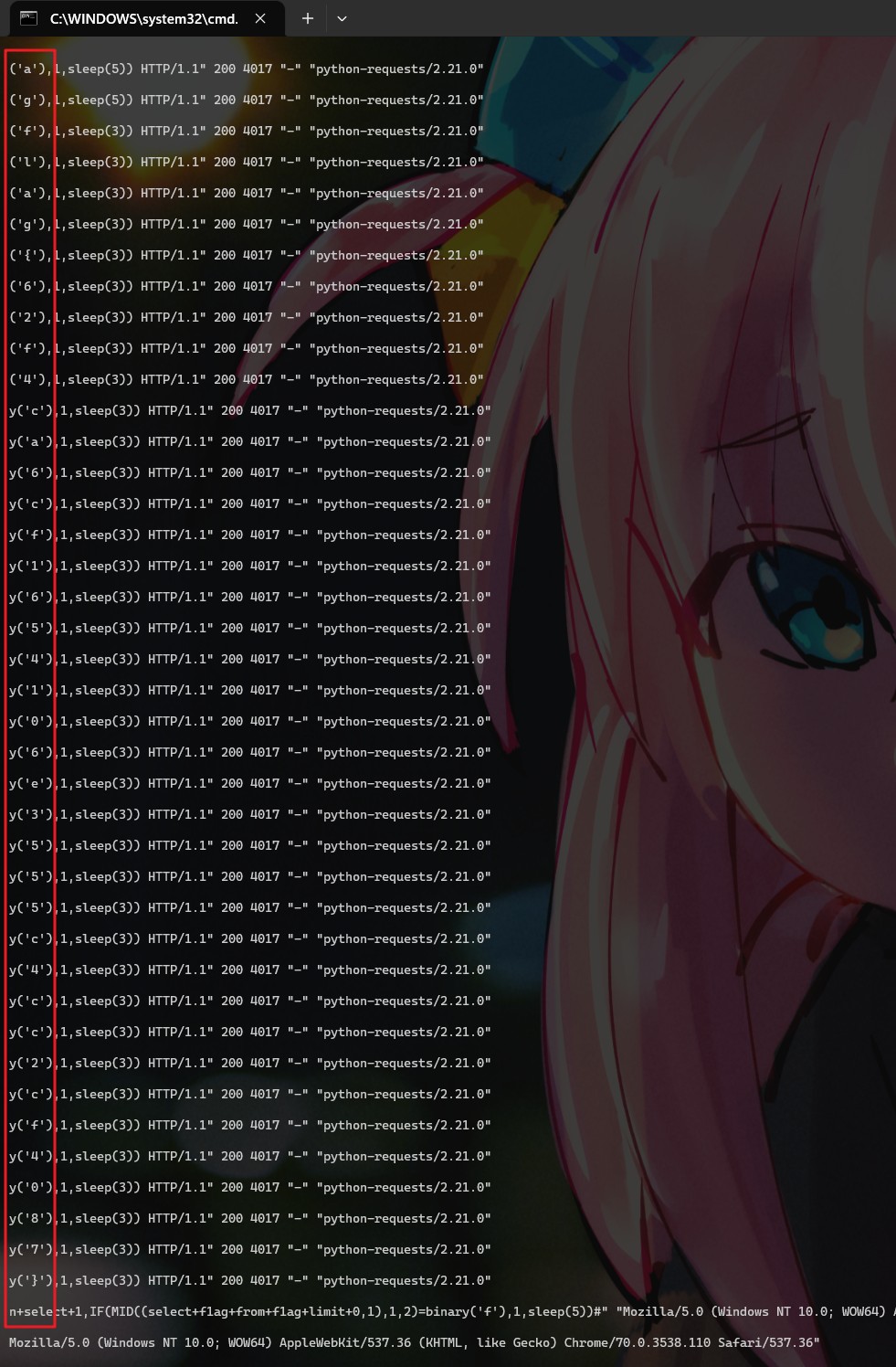
1
| flag{62f4ca6cf1654106e3555c4cc2cf4087}
|